zzcms2025 - Database Stores User Passwords in Plaintext
zzcms2025 - Database Stores User Passwords in Plaintext#
Vulnerability Author: airrudder
Affected Version: ZZCMS 2025
Vendor: http://www.zzcms.net/
Software Download: http://www.zzcms.net/download/zzcms2025.zip
Vulnerable File:
/reg/user_save.php
Vulnerability Description
The user data storage module of the zzcms2025 version has a sensitive information plaintext storage vulnerability. When the system registers/saves user information, it does not hash or encrypt the user's password, but stores it directly in plaintext in the database's user table (e.g., the zzcms_user table). If an attacker gains access to the database, they can directly read all user passwords in plaintext, leading to a complete compromise of user accounts.
Vulnerability Reproduction
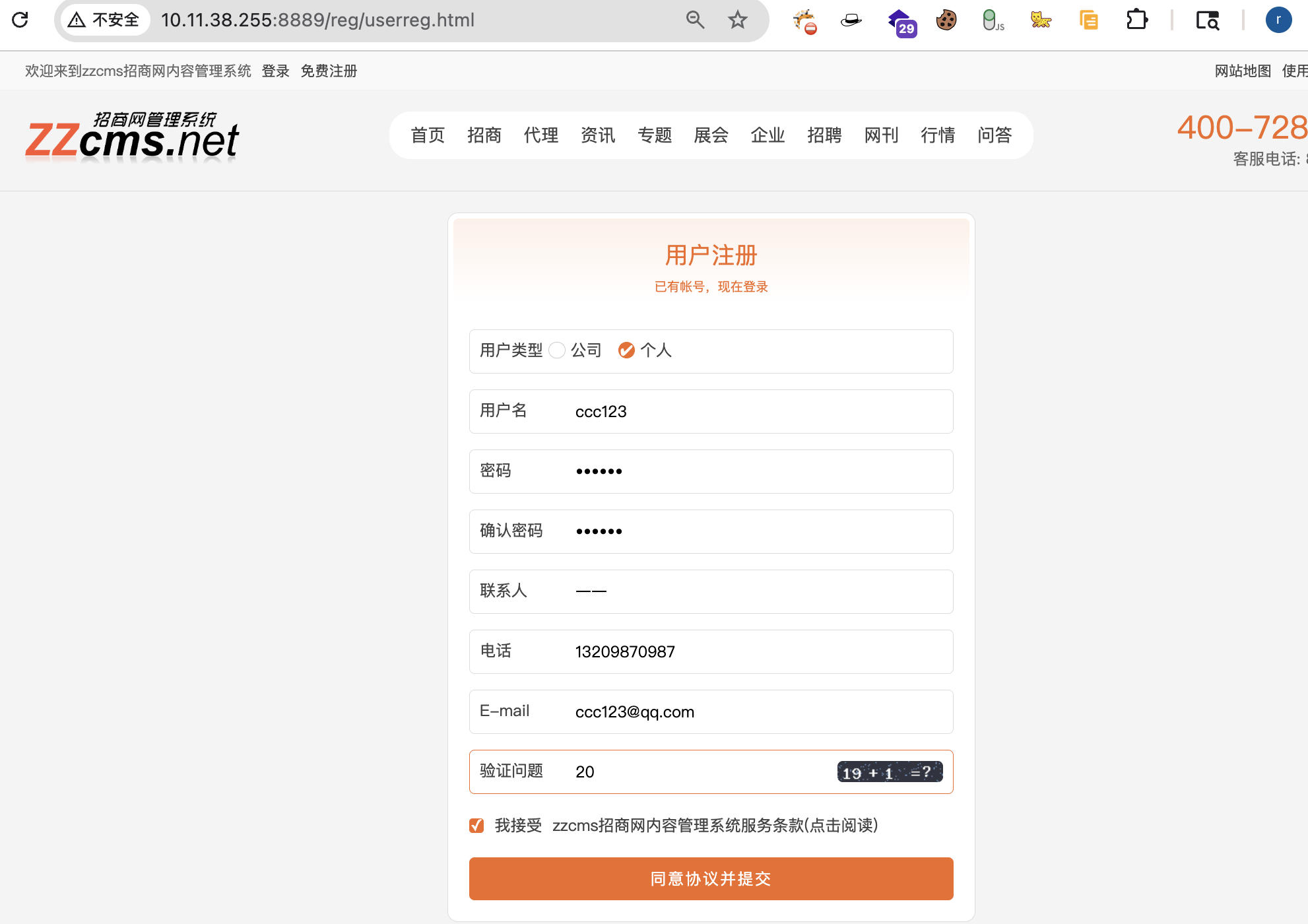
Register directly by visiting /reg/userreg.html.
In the database, you can find that both the hash value of the registered user's password and the plaintext password are stored in the database.
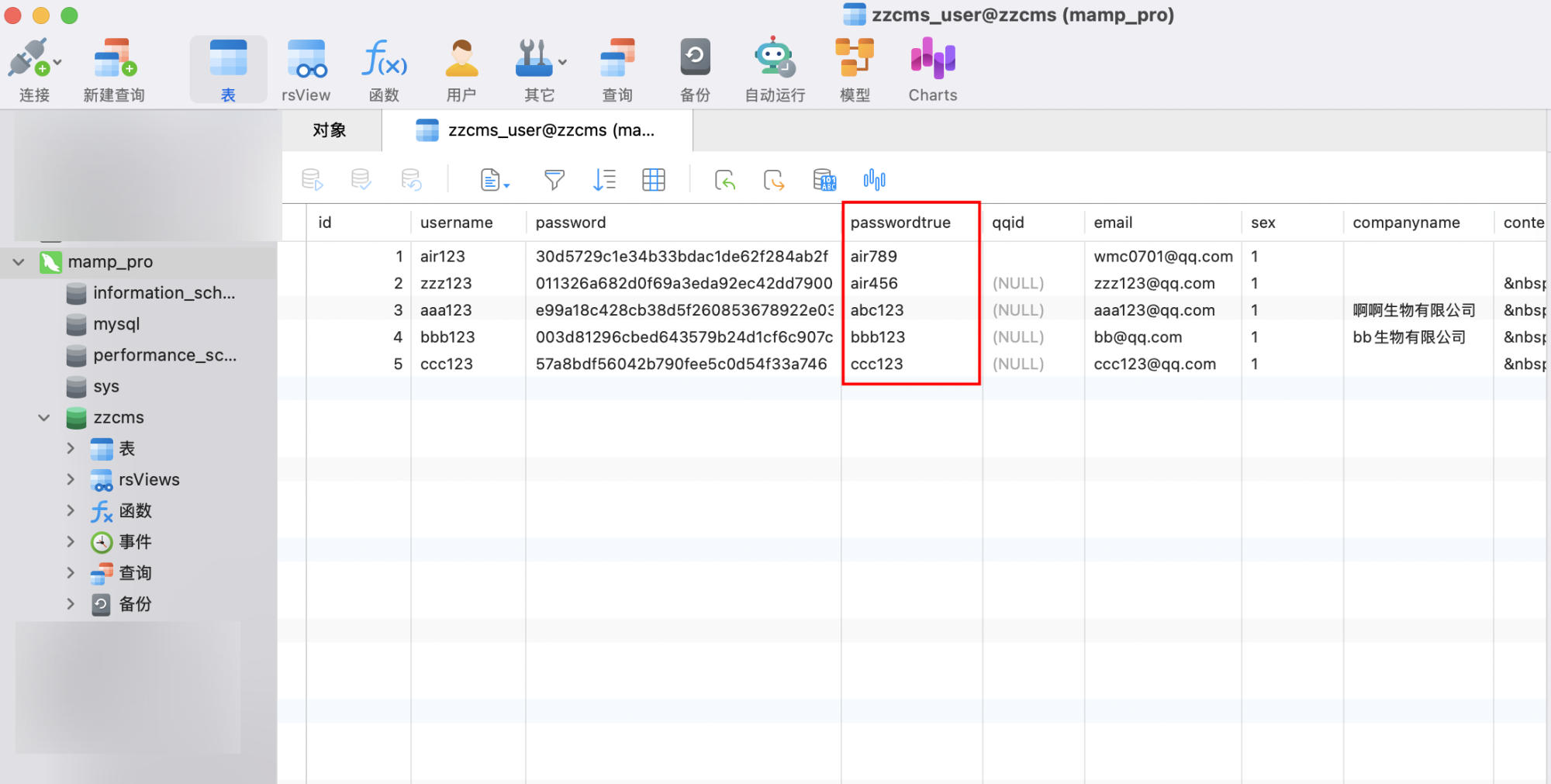
This is a very serious product design flaw. Storing passwords in plaintext can lead to user data leakage incidents.